Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:

ManageEngine Firewall Analyzer
7 Essential Firewall Management Strategies for Ma…
A firewall appliance is a fundamental pillar of network security, acting as the first line of defense against cyber threats. However, its strength…

ManageEngine Firewall Analyzer
Ensuring Compliance and Business Continuity in a…
In the wake of digital transformation, the work landscape as we know it has undergone a dynamic shift. People can now work from home, from the office…
EventLog Analyzer
Detecting Windows Server Security Threats with Ad…
Windows Servers stand as prime targets for hackers and malicious actors due to their widespread usage and historical vulnerabilities. These systems o…
OpManager - Network Monitoring & Management
Ensuring Enterprise Network Readiness for Mobile…
Demands for Enterprise networks to properly support mobile users is on a continuous rise making it more than ever necessary for IT departments to pro…
Featured Subcategories:
WireShark Articles:
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtual…
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fire…
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall PAN-OS…
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, saf…
Windows Servers
Guide to Windows Server 2016 Hyper-V Hypervisor: New V…
One of Windows Server 2016 highlights is the newer Hyper-V server that not only extends the hypervisor’s features and capabilities but also introduces a n…
Windows Servers
Creating a Virtual Machine in Windows Hyper-V. Configu…
Our previous articles covered basic concepts of Virtualization along with the installation and monitoring of Windows 2012 Hyper-V. This article takes the…
Windows Servers
Renaming Windows 2000 Domain Name
Sometimes renaming a domain is an essential business requirement. There are many situations, such as mergers, change of company name or migration from a t…
Windows Servers
Download Altaro Free VM Backup & Win a PlayStation 4 P…
We have some exciting news for you today!
Altaro has launched a great contest in celebration of SysAdmin Day on 27th July!
They will be giving away Amaz…
Popular Topics

Network Fundamentals
Network Switches & Bridges
Network Switches are the evolution of Hubs and Repeaters, and enable the creation of networks by connecting multiple devices together. They are critical c…

Virtualization & VM Backup
8 Critical Features to Have in a VM Backup Solution
Businesses that rely on virtual machines for their day-to-day operations should think twice about securing their infrastructure. Modern use of virtual mac…
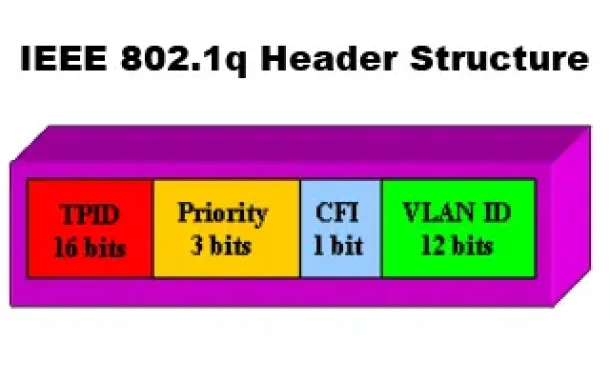
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…
SASE & SD-WAN Networks
MPLS vs. SD-WAN vs. Internet vs. Cloud Network. Connec…
The Wide Area Network (WAN) is the backbone of the business. It ties together the remote locations, headquarters and data centers into an integrated netwo…
Cisco Services & Technologies
Unified Communications Components - Understanding Your…
What Is Unified Communications (UC)?
Unified communications is a very popular term these days and we see it appearing on almost every vendor as the…
Cisco Routers
Understanding MPLS IP VPNs, Security Attacks and VPN E…
What Are MPLS Networks?
Multi-Protocol Label Switching (MPLS) networks are the next-generation of networks designed to allow customers create end-to-end…
Cisco CallManager-CCME
Introduction to Cisco Unified Communication Manager Ex…
We have been hearing about VoIP for many years now and while some have never worked with it, it has become today's standard in IP Communications and Priva…
Cisco Switches
Cisco 4507R+E Layer 3 Installation: Redundant WS-X45-S…
It's no news that we here at Firewall.cx enjoy writing about our installations of Cisco equipment and especially devices that we don’t get to see and play…



















