Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
|
Articles:
The OSI Model: Layer 5 - Session Layer
| Read |
|
Articles:
The OSI Model: Layer 4 - Transport Layer
| Read |
|
Articles:
The OSI Model: Layer 3 - Network Layer
| Read |
|
Articles:
The OSI Model: Layer 2 - Datalink Layer
| Read |
|
Articles:
The OSI Model: Layer 1 - Physical Layer
| Read |
Suggested Articles:
Network Address Translation - NAT
Dynamic NAT - Part 1
Dynamic NAT is the second NAT mode we're going to talk about. Dynamic NAT, like Static NAT, is not that common in smaller networks but you'll find it…
Ethernet Protocol, CSMA/CD, Collisions
The IEEE 802.3 SNAP Frame Format
While the original 802.3 specification worked well, the IEEE realized that some upper layer protocols required an Ethertype to work properly. For exa…
Network Cabling
Serial Direct Cable Connection, DB9, DB25, COM Po…
This article covers the popular serial ports on workstations, servers and laptop computers. We cover serial data transfer, port pinouts, port speeds…
Ethernet Protocol, CSMA/CD, Collisions
Troubleshooting techniques for Fast Ethernet
This page will primarily discuss problems unique to Fast Ethernet.
The Collision Domain
Incompatible Ethernet Jabber
Auto-negotiation Priorities…
Featured Subcategories:
Netflow Articles:
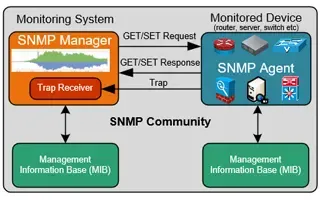
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
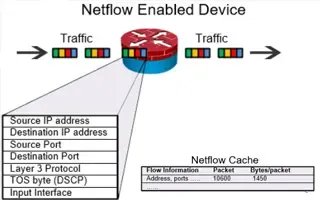
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
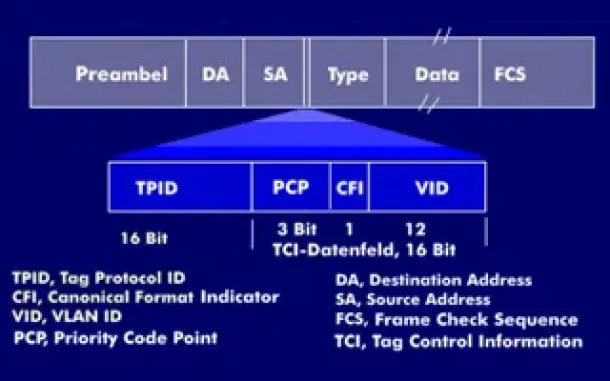
VLAN Networks
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trunks…

VLAN Networks
Static VLANs
VLANs are usually created by the network administrator, assigning each port of every switch to a VLAN. Depending on the network infrastructure and securit…

VLAN Networks
Comparing Traditional Flat & VLAN Networks
Designing and building a network is not a simple job. VLANs are no exception to this rule, in fact they require a more sophisticated approach because of t…
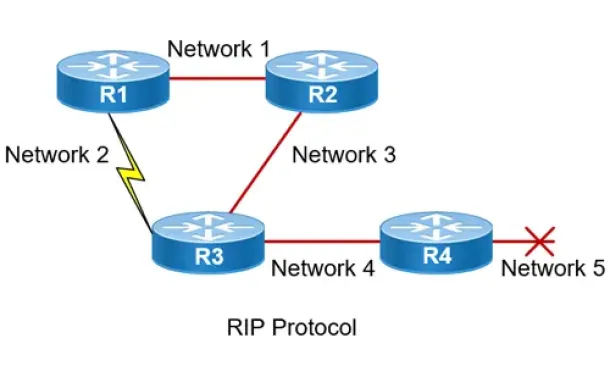
Routing
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…
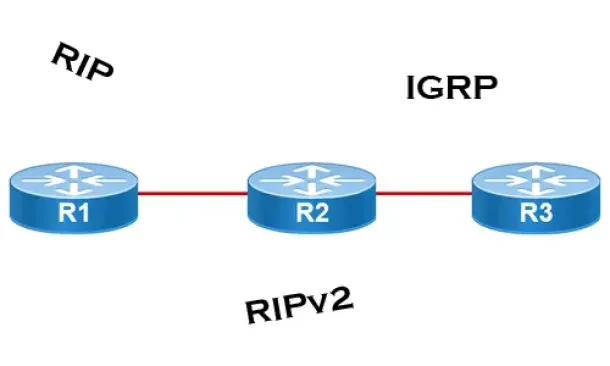
Routing
Distance Vector Routing Protocols
Distance Vector routing protocols use frequent broadcasts (255.255.255.255 or FF:FF:FF:FF) of their entire routing table every 30 sec. on all their interf…
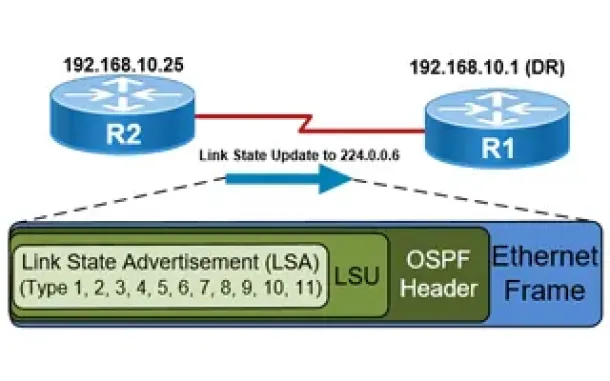
Routing
OSPF - Part 5: Analysis of OSPF Link State Update (LSU…
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router recei…
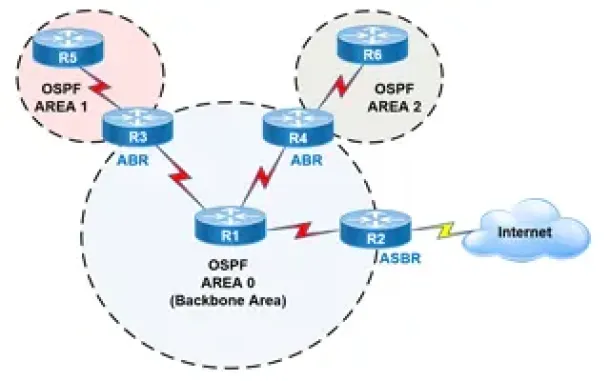
Routing
OSPF - Part 2: How OSPF Protocol Works & Basic Concept…
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose (N…
Cisco Routers
Disabling Cisco Router Password Recovery Service
Most Cisco engineers are aware of the classic Password-Recovery service Cisco equipment have. If the device's credentials are lost, then performing the Pa…
Windows Servers
Windows Server 2016 VM Backup with Altaro's New VM Bac…
Altaro has released Altaro VM Backup, a faster and lighter upgrade to its flagship Hyper-V and VMware backup solution, which now supports all Windows Serv…
Palo Alto Networks
The Benefits of Palo Alto Networks Firewall Single Pas…
What makes Palo Alto Networks Next-Generation Firewall (NGFW) so different from its competitors is its Platform, Process and Architecture. Palo Alto Netwo…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
In this article, we will cover more advanced DHCP features and topics such as server options, superscopes, multicast scopes, dynamic DNS, DHCP database ba…



















