Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
Network Protocol Analyzers
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
Network Protocol Analyzers
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…

OpManager - Network Monitoring & Management
Optimizing Cisco Router Performance: Best Practic…
Effective monitoring and management of Cisco routers and network devices are essential for ensuring a robust and efficient network infrastructure. In…
Network Protocol Analyzers
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
Featured Subcategories:
WireShark Articles:
How To Detect ARP Attacks & ARP Flooding With Col…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addres…
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enforcemen…
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with the…

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on P…
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a P…
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…
Windows Servers
New Upcoming Features in Hyper-V vNext - Free Trainin…
With the release of Hyper-V vNext just around the corner, Altaro has organized a Free webinar that will take you right into the new Hyper-V vNext release…
Windows Servers
How to Install Windows 2012 Hyper-V via Server Manager…
Our previous article covered the basic concepts of Virtualization and Windows Server 2012 Hyper-V. This article takes a closer look at Microsoft’s H…
Windows Servers
Introduction to Windows DNS – The Importance of DNS fo…
The Domain Name System (DNS) is perhaps one of the most important services for Active Directory. DNS provides name resolution services for Active Director…
Windows Servers
Renaming Windows 2000 Domain Name
Sometimes renaming a domain is an essential business requirement. There are many situations, such as mergers, change of company name or migration from a t…
Popular Topics
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
In this article, we will cover more advanced DHCP features and topics such as server options, superscopes, multicast scopes, dynamic DNS, DHCP database ba…
Windows Servers
Easy, Fast & Reliable Hyper-V & VMware Backup with Alt…
As more companies around the world adopt the virtualization technology to increase efficiency and productivity, Microsoft’s Hyper-V virtualization platfor…
Windows Servers
Renaming Windows 2000 Domain Name
Sometimes renaming a domain is an essential business requirement. There are many situations, such as mergers, change of company name or migration from a t…
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With Colasoft…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC address and…
Cisco CallManager-CCME
Cisco CallManager Express CME v8.8 & v9.0 GUI Web Inte…
Cisco's CallManager Express GUI interface is an important part of the CallManager Express product as it provides the ability to administer CME via a web b…
Cisco Wireless
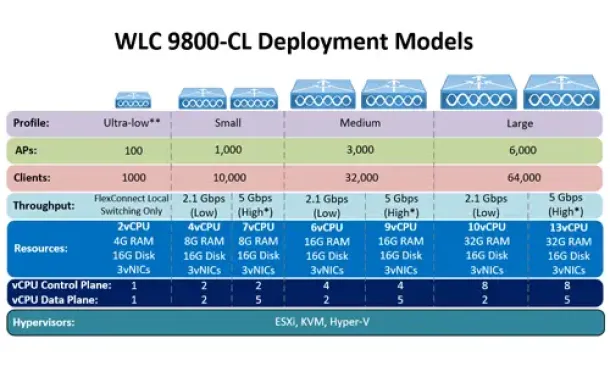
Complete Guide: How to Download & Deploy The Cisco 980…
This article covers the deployment of the Cisco WLC 9800-CL cloud-based controller on the VMware ESXi platform. We explain the CPU, RAM and storage requir…
Cisco CallManager-CCME
CallManager Express GUI Software Installation & Config…
Cisco CallManager Express, also known as CME or CCME, runs on both Cisco ISR Routers and UC500 platform, including UC520, UC540 and UC560.
CallManager Ex…
Cisco Firewalls
Converting Cisco Firepower from Platform mode to Appli…
This article explains how to configure a Cisco Firepower 2100 series device to operate in Appliance mode. We’ll show you how to switch from Platform mode…



















