Suggested Articles:
Cisco CallManager-CCME
Free Cisco IP Phone & ATA Firmware (SCCP & SIP)…
Firewall.cx readers can now download free Cisco firmware files for all Cisco IP Phones & Cisco ATA devices. Our new Cisco IP Phone & ATA Firm…
Cisco CallManager-CCME
Cisco Unity Express Installation & Setup - ISM-SR…
Unity Express is a popular add-on for Cisco Unified Communication Manager Express (CallManager Express) and Cisco Unified Communication Manager (CUCM…
Cisco Routers
Configuring NTP on a Cisco Router (NTP Client and…
Network Time Protocol (NTP) is a vital service not only for Cisco devices but almost every network device. Any computer-based device needs to be accu…
Cisco Firewalls
Understand & Configure NAT Reflection, NAT Loopba…
This article examines the concept of NAT Reflection, also known as NAT Loopback or Hairpinning, and shows how to configure a Cisco ASA Firewall runni…
Featured Subcategories:
Data Center Articles:

NEXUS NX-OS: Useful Commands, CLI Scripting, Hint…
Whether you’re new to Cisco Nexus switches or have been working with them for years this article will show how to get around the Nexus NX-OS usi…
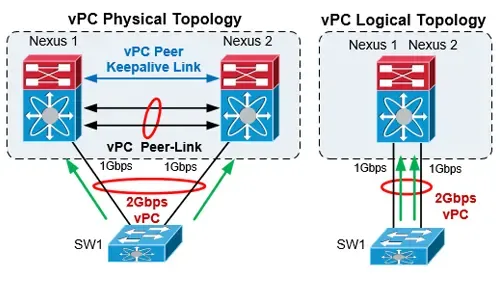
The Complete Cisco Nexus vPC Guide. Features & Ad…
Cisco virtual Port Channel (vPC) is a virtualization technology, launched in 2009, which allows links that are physically connected to two different…

Join Australia’s First Official Cisco Data Center…
It’s a reality – Australia now has its own Official Cisco Data Center User Group (DCUG) and it’s growing fast! Originally inspired by Cisco Champions…

Nexus 7000/7700 Software Upgrade via ISSU. Comple…
This article shows how to perform an ISSU (In-Service Software Upgrade) on a Nexus Data Center switch (7000 and 7700 models) and avoid service and ne…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Cisco Switches
Spanning Tree BPDU Guard and Errdisable Interface Auto…
Running Spanning Tree Protocol (STP) in a large network environment can be a challenging task especially when features/enhancements such as BPDU Filter an…
Cisco Switches
Forcing A Cisco Catalyst Switch To Use 3rd Party SFP M…
Many companies are seeking for Cisco SFP alternatives to help cut down the costs on these expensive modules.
A frequent customer problem with Cisco's new…
Cisco Switches
VLAN Security Tips - Best Practices
This article focuses on VLAN Security and its implementation within the business network environment. We provide tips and Cisco CLI commands that will hel…
Cisco Switches
Installation of a Cisco Catalyst 4507R-E Layer 3 Switch
Driven by our thirst for technical material and experience, we thought it would be a great idea to start presenting various installations of Cisco equipme…
Cisco Firewalls
Converting Cisco Firepower from Platform mode to Appli…
This article explains how to configure a Cisco Firepower 2100 series device to operate in Appliance mode. We’ll show you how to switch from Platform mode…
Cisco Firewalls
Cisco ASA 5500-X Series Firewall with IPS, ASA CX & Fi…
The Cisco ASA Firewall 5500-X series has evolved from the previous ASA 5500 Firewall series, designed to protect mission critical corporate networks and d…
Cisco Firewalls
Upgrading - Uploading AnyConnect Secure Mobility Clien…
This article will show how to download and upload the newer AnyConnect 4.x VPN clients to your Cisco ASA Firewall appliance (5500 & 5500-X Series) and…
Cisco Firewalls
Cisco ASA 5500 Series Firewall Modules & Cards – Conte…
Cisco’s Adaptive Security Appliance (ASA) Firewalls are one of the most popular and proven security solutions in the industry. Since the introduction of t…
Popular Topics

Virtualization & VM Backup
Ultimate Guide: Install Windows 11 on VMware ESXi – Ea…
In this article, we’ll show you how to setup or install Microsoft Windows 11 on VMware’s ESXi servers and bypass the Trusted Platform Module version 2.0 (…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
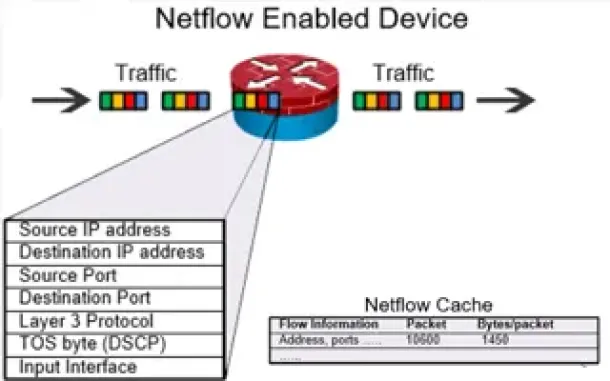
Netflow
Complete Guide to Netflow: How Netflow & its Component…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive into the…
Virtualization & VM Backup
SysAdmin Day 2020 - Get your Free Amazon Voucher & Gif…
SysAdmin Day has arrived, and with it, gratitude for all the unsung heroes that 2020 has needed. Your hard work has made it possible for all of us to keep…



















