Suggested Articles:
Ethernet Protocol, CSMA/CD, Collisions
802.3 Fast Ethernet (100 Mbit/Sec) Model
Here we see a logical drawing of the Fast Ethernet Data Link Layer sublayers. Data is passed down from the upper layers (such as TCP/IP or Novell Net…
ICMP Protocol
ICMP Protocol - Part 6: Redirect Messages
The ICMP - Redirect Message is always sent from a gateway to the host and the example below will illustrate when this is used.
Putting it simply (be…
TCP - UDP Protocol Analysis
UDP Protocol - Header
This article covers the UDP protocol. We examine the structure of the UDP header, the protocols that use UDP as a transport plus a lot more.
Some co…
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 7: TCP Data Payload…
Finally, the last page of our incredible TCP Analysis. As most of you would expect, this section is dedicated to the DATA section that follows the TC…
Featured Subcategories:
Netflow Articles:
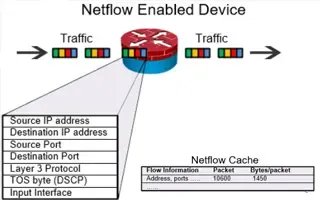
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
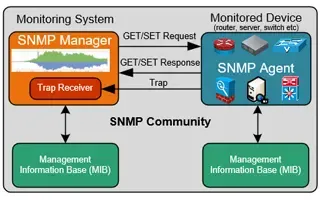
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
InterVLAN Routing - Routing between VLAN Networks
This article deals with the popular topic of InterVLAN routing, which is used to allow routing & communication between VLAN networks. Our article anal…

VLAN Networks
The VLAN Concept - Introduction to VLANs
We hear about them everywhere, vendors around the world are constantly trying to push them into every type of network and as a result, the Local Area Netw…

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…
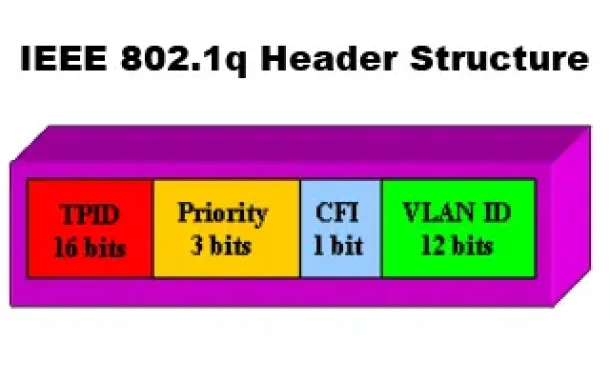
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…
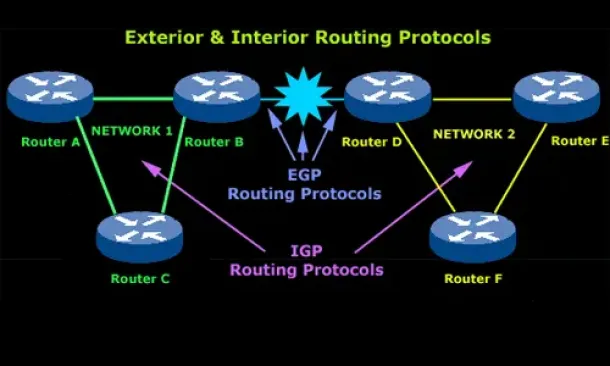
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchange…
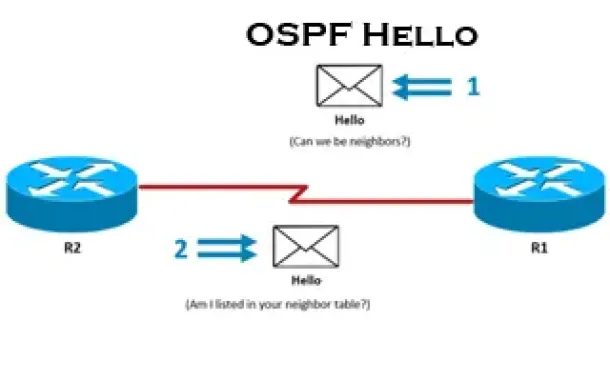
Routing
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Proce…
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll examine…
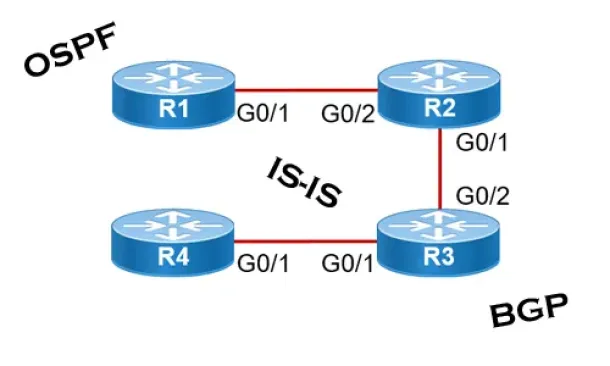
Routing
Link State Routing Protocols
Link State routing protocols do not view networks in terms of adjacent routers and hop counts, but they build a comprehensive view of the overall network…
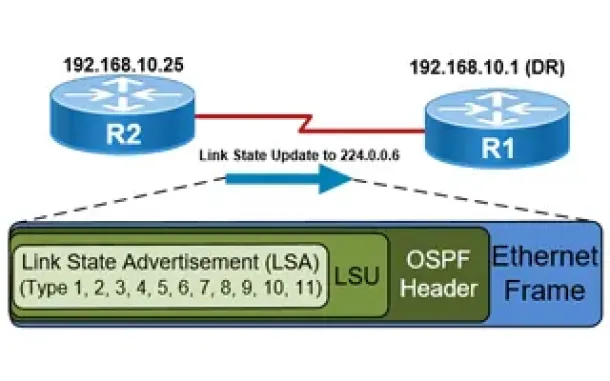
Routing
OSPF - Part 5: Analysis of OSPF Link State Update (LSU…
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router recei…
Windows Servers
Installing Windows Server 2012 Active Directory via Se…
This article serves as an Active Directory tutorial covering installation and setup of a Windows 2012 Domain Controller using Windows Server Manager (GUI)…
Virtualization & VM Backup
Understanding Deduplication. Complete Guide to Dedupli…
When considering your VM backup solution, key features such as deduplication are incredibly important. This is not simply from a cost perspective but also…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
In this article, we will cover more advanced DHCP features and topics such as server options, superscopes, multicast scopes, dynamic DNS, DHCP database ba…
Windows Servers
Guide to Windows Server 2016 Hyper-V Hypervisor: New V…
One of Windows Server 2016 highlights is the newer Hyper-V server that not only extends the hypervisor’s features and capabilities but also introduces a n…



















