Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:

ManageEngine Firewall Analyzer
7 Essential Firewall Management Strategies for Ma…
A firewall appliance is a fundamental pillar of network security, acting as the first line of defense against cyber threats. However, its strength…

OpManager - Network Monitoring & Management
Elevate your network management: Maximizing effic…
As technology evolves, so do our networks. Today's sprawling network infrastructures are intricate ecosystems, demanding more from IT teams than ever…

ManageEngine Firewall Analyzer
Ensuring Compliance and Business Continuity in a…
In the wake of digital transformation, the work landscape as we know it has undergone a dynamic shift. People can now work from home, from the office…
Network Protocol Analyzers
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
Featured Subcategories:
WireShark Articles:
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Palo Alto Networks
The Benefits of Palo Alto Networks Firewall Single Pas…
What makes Palo Alto Networks Next-Generation Firewall (NGFW) so different from its competitors is its Platform, Process and Architecture. Palo Alto Netwo…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based Po…
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient wa…
Windows Servers
New Features in Windows Server 2012 - Why Upgrade to…
There is no doubt that Cloud Computing is hot topic these days. Innovations in cloud computing models have made every industry and company IT departments…
Windows Servers
How to Install Windows 2012 Hyper-V via Server Manager…
Our previous article covered the basic concepts of Virtualization and Windows Server 2012 Hyper-V. This article takes a closer look at Microsoft’s H…
Windows Servers
Free Webinar: Migrating from Hyper-V to VMware
If your organization is planning to migration from a Hyper-V virtualization environment to VMware then this FREE webinar is just for you.
Aimed toward Hy…
Windows Servers
Renaming Windows 2000 Domain Name
Sometimes renaming a domain is an essential business requirement. There are many situations, such as mergers, change of company name or migration from a t…
Popular Topics
Network Fundamentals
Power over Ethernet - Understanding PoE Technology, Po…
Power over Ethernet (PoE) was invented by PowerDsine back in 1997 and the first power injector (Midspan) was installed in 1998! Many manufacturespartnered…
SASE & SD-WAN Networks
The Most Common Worst Networking Practices and How To…
In the rush to keep pace with the many challenges facing today’s organizations, all too often networking teams end up adopting practices and processes tha…

Network Fundamentals
Multicast - Understand How IP Multicast Works
Multicast is a communication method used in computer networking where data is sent from a single sender to a group of destination devices. In this method…
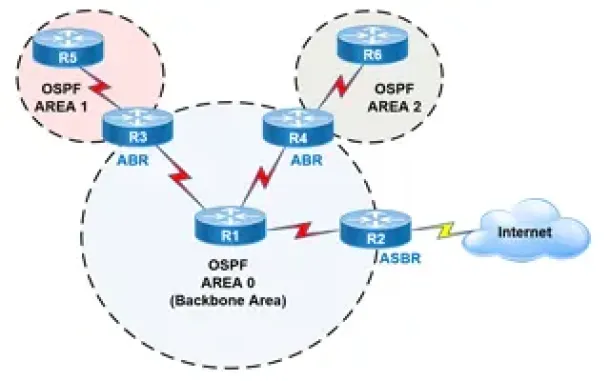
Routing
OSPF - Part 2: How OSPF Protocol Works & Basic Concept…
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose (N…
Cisco Firewalls
Cisco ASA Firepower Threat Defense (FTD): Download and…
One Appliance – One Image is what Cisco is targeting for its Next Generation Firewalls. With this vision, Cisco has created a unified software image named…
Cisco Switches
Cisco Catalyst 4500 Series Zero-Downtime IOS Upgrade P…
The Supervisor Engine is the heart of the Cisco Catalyst 4500 and 6500 series switches. It is the equivalent of an engine in a car. Every packet that ente…
Cisco Services & Technologies
Comparing Cisco VPN Technologies – Policy Based vs Rou…
Virtual Private Networks constitute a hot topic in networking because they provide low cost and secure communications between sites (site-to-site VPNs) wh…
Cisco Wireless
Introduction To Cisco Wireless Controllers (WLC) - Bas…
The Cisco Wireless Controller (WLC) series devices provide a single solution to configure, manage and support corporate wireless networks, regardless of t…



















