Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
UDP Protocol - Header
| Read |
Suggested Articles:
Ethernet Protocol, CSMA/CD, Collisions
Introduction to Ethernet Collisions
The word "Collision" shouldn't be any new news to people who work with networks everyday. If it is thought, don't worrie, that's why you are here.
A…
The OSI Model
The OSI Model: Layer 7 - Application Layer
The Application layer of the OSI model is where users communicate with the computer. The Application layer is responsible for identifying and establi…

Network Fundamentals
Need for Speed – The Data Tsunami & Advancements…
A long-long time ago (not long ago in earth time) 100 Mbps was THE technology. 100 Mbps uplinks bundled with ether-channel was the ultimate uplink te…
Ethernet Protocol, CSMA/CD, Collisions
The IEEE 802.3 Frame Format
The following is a description of the Ethernet Frame Format described in the IEEE 802.3 Specification. The 802.3 Specification defines a 14 byte Data…
Featured Subcategories:
Netflow Articles:
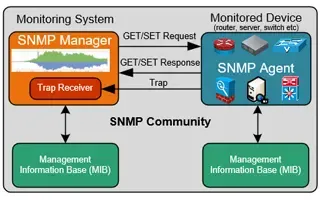
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
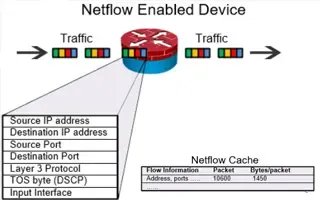
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
Dynamic VLANs
Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of their…

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trunks…

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Stati…
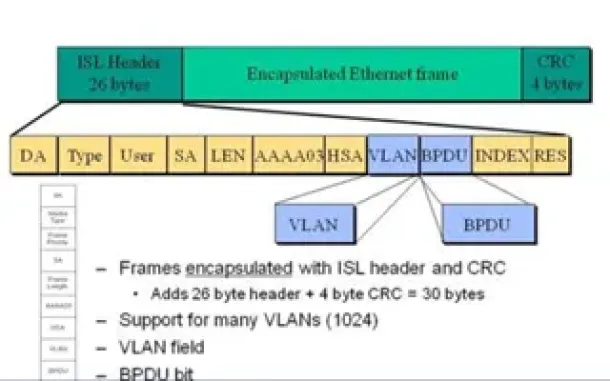
VLAN Networks
VLAN InterSwitch Link (ISL) Protocol Analysis
Deciding whether to use ISL or IEEE 802.1q to power your trunk links can be quite confusing if you cannot identify the advantages and disadvantages of eac…
Routing
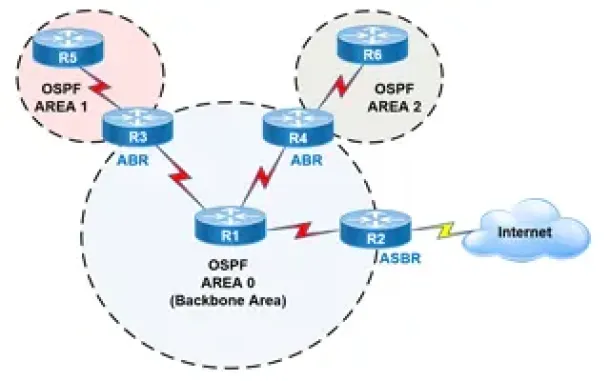
OSPF - Part 2: How OSPF Protocol Works & Basic Concept…
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose (N…
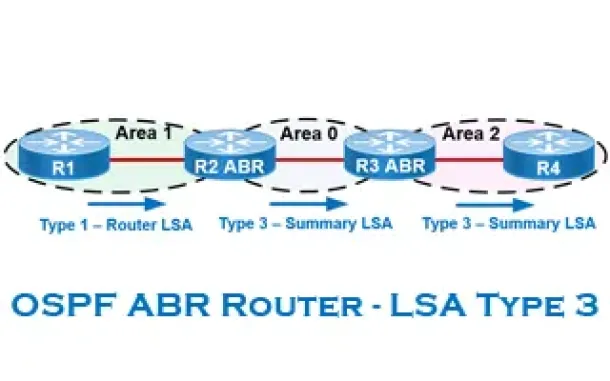
Routing
OSPF - Part 6: OSPF LSA Types - Purpose and Function o…
Our previous article explained the purpose of Link State Update (LSU) packets and examined the Link State Advertisement (LSA) information contained within…
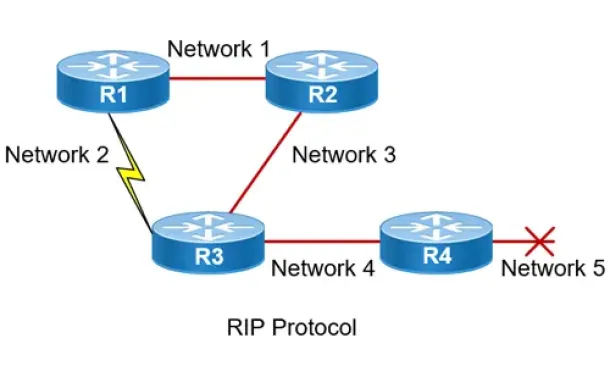
Routing
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…
Routing
Enhanced Interior Gateway Routing Protocol - EIGRP
Enhanced Interior Gateway Routing Protocol (EIGRP), similar to IGRP, is a Cisco proprietary routing protocol that is used to exchange routing information…
Cisco Routers
How to Restrict Cisco IOS Router VPN Client to Layer-4…
In our article Cisco VPN Client Configuration - Setup for IOS Router we explained how to setup up a Cisco IOS router to support Cisco IPSec VPN clie…
SASE & SD-WAN Networks
WAN Optimization vs SD WAN Networks. Today’s Challenge…
Enterprises have been successfully running WAN optimization appliances at their many distributed sites for years. The devices have done a good job of help…
Cisco Switches
Cisco Catalyst 4500 Series Zero-Downtime IOS Upgrade P…
The Supervisor Engine is the heart of the Cisco Catalyst 4500 and 6500 series switches. It is the equivalent of an engine in a car. Every packet that ente…
Windows Servers
Free Webinar: Scripting & Automation in Hyper-V withou…
System Center Virtual Machine Manager (SCVMM) provides some great automation benefits for those organizations that can afford the hefty price tag. However…



















