Suggested Articles:
Cisco CallManager-CCME
Cisco Unity Express Installation/Setup - Service…
Mentioned in Part-1 of our Cisco Unity Express installation article, the Cisco Unity Express setup procedure is identical for ISM-SRE-300-K9 and SM-S…
Cisco Routers
How To Fix Cisco Configuration Professional (CCP)…
Our previous article covered how to fix the Cisco Configuration Professional display/window problem where the CCP application is displayed in about o…
Cisco Switches
Download The Complete Cisco Catalyst Switching Po…
The Cisco Catalyst Switching Portfolio is perhaps one of the most useful Cisco PDF files, containing all Catalyst series products. The portfol…
Cisco Switches
Cisco Catalyst Err-disabled Port State, Enable &…
Errdisable is a feature that automatically disables a port on a Cisco Catalyst switch. When a port is error disabled, it is effectively shut dow…
Featured Subcategories:
Data Center Articles:

NEXUS NX-OS: Useful Commands, CLI Scripting, Hint…
Whether you’re new to Cisco Nexus switches or have been working with them for years this article will show how to get around the Nexus NX-OS usi…

Introduction to Cisco Nexus Switches – Nexus Prod…
This article introduces the Cisco Nexus product family (Nexus 9000, Nexus 7000, Nexus 5000, Nexus 3000, Nexus 2000, Nexus 1000V and MDS 9000). We exp…

Join Australia’s First Official Cisco Data Center…
It’s a reality – Australia now has its own Official Cisco Data Center User Group (DCUG) and it’s growing fast! Originally inspired by Cisco Champions…
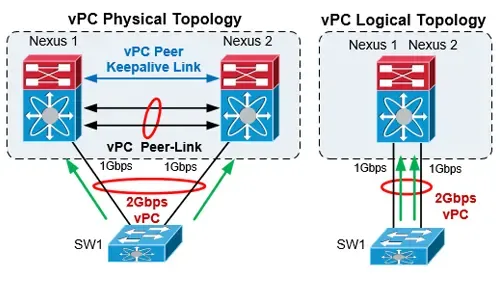
The Complete Cisco Nexus vPC Guide. Features & Ad…
Cisco virtual Port Channel (vPC) is a virtualization technology, launched in 2009, which allows links that are physically connected to two different…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Cisco Switches
Configuring SPAN On Cisco Catalyst Switches - Monitor…
Being able to monitor your network traffic is essential when it comes to troubleshooting problems, performing a security audit or even casually checking y…
Cisco Switches
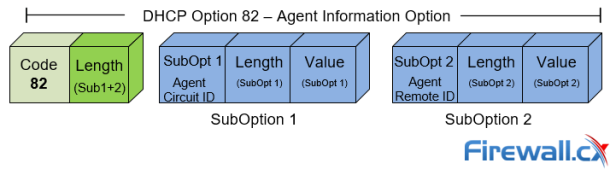
DHCP Option 82 Message Format, Analysis. DHCP Snooping…
This article provides in-depth analysis of DHCP Option 82 (DHCP Relay Agent) which is one of the +180 DHCP Options available to the DHCP protocol and used…
Cisco Switches
Installation of a Cisco Catalyst 4507R-E Layer 3 Switch
Driven by our thirst for technical material and experience, we thought it would be a great idea to start presenting various installations of Cisco equipme…
Cisco Switches
Complete Guide to DHCP Snooping, How it Works, Concept…
This article covers popular Layer 2 & Layer 3 network attacks with a focus on DHCP Starvation Attacks, Man-in-the-Middle attacks, unintentional rogue…
Cisco Firewalls
Converting Cisco Firepower from Platform mode to Appli…
This article explains how to configure a Cisco Firepower 2100 series device to operate in Appliance mode. We’ll show you how to switch from Platform mode…
Cisco Firewalls
Demystifying Cisco AnyConnect 4.x Licensing. Plus, Plu…
In late 2014, Cisco announced the new licensing model for the latest AnyConnect Secure Mobility client v4.x. With this new version, Cisco introduced a num…
Cisco Firewalls
Cisco ASA 5500 Series Firewall Modules & Cards – Conte…
Cisco’s Adaptive Security Appliance (ASA) Firewalls are one of the most popular and proven security solutions in the industry. Since the introduction of t…
Cisco Firewalls
Upgrading - Uploading AnyConnect Secure Mobility Clien…
This article will show how to download and upload the newer AnyConnect 4.x VPN clients to your Cisco ASA Firewall appliance (5500 & 5500-X Series) and…
Popular Topics
SASE & SD-WAN Networks
The Need for a Converged SASE Platform. Converging Net…
The digital transformation is pushing applications to the cloud, the 2020-2022 pandemic shifted employees to work from home, and the number of resulting n…
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on P…
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a P…



















