Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
Introduction to Routing Protocols
| Read |
| Read | |
|
Articles:
Interior Gateway Protocol - IGRP
| Read |
| Read | |
|
Articles:
Routing Information Protocol - RIP
| Read |
| Read | |
|
Articles:
Link State Routing Protocols
| Read |
|
Articles:
Distance Vector Routing Protocols
| Read |
| Read | |
|
Articles:
Routed Protocols
| Read |
Suggested Articles:

Network Fundamentals
Hubs & Repeaters
Network hubs were once the primary method of interconnecting network devices to create a local area network (LAN). Hubs were inexpensive, easy to ins…
The OSI Model
The OSI Model: Layer 1 - Physical Layer
The Physical layer has two responsibilities: it sends bits and receives bits. Bits come only in values of 1 or 0. The Physical layer communicates dir…
Subnetting
IP Subnetting - Part 3: Subnet Mask Bits & Analys…
So we have covered to some depth the subnetting topic, but there is still much to learn ! We are going to explain here the available subnet masks and…

Network Fundamentals
Need for Speed – The Data Tsunami & Advancements…
A long-long time ago (not long ago in earth time) 100 Mbps was THE technology. 100 Mbps uplinks bundled with ether-channel was the ultimate uplink te…
Featured Subcategories:
Netflow Articles:
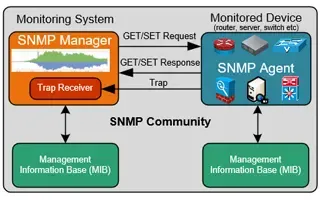
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
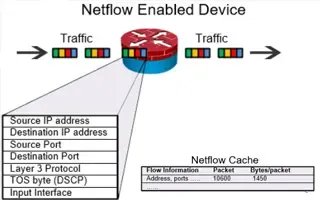
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
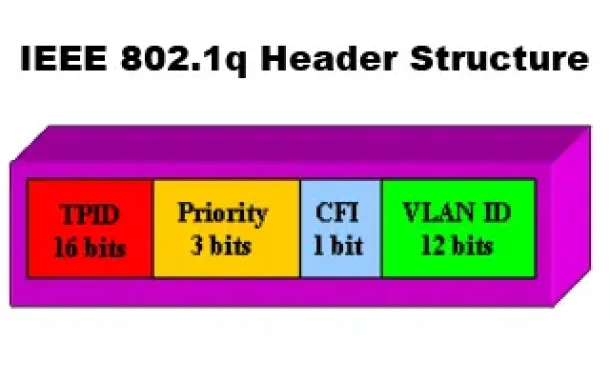
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…

VLAN Networks
The VLAN Concept - Introduction to VLANs
We hear about them everywhere, vendors around the world are constantly trying to push them into every type of network and as a result, the Local Area Netw…

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Stati…
Routing
Enhanced Interior Gateway Routing Protocol - EIGRP
Enhanced Interior Gateway Routing Protocol (EIGRP), similar to IGRP, is a Cisco proprietary routing protocol that is used to exchange routing information…
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informati…
Routing
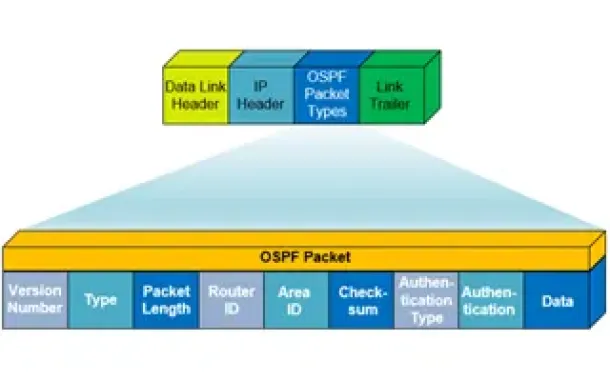
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
Routing
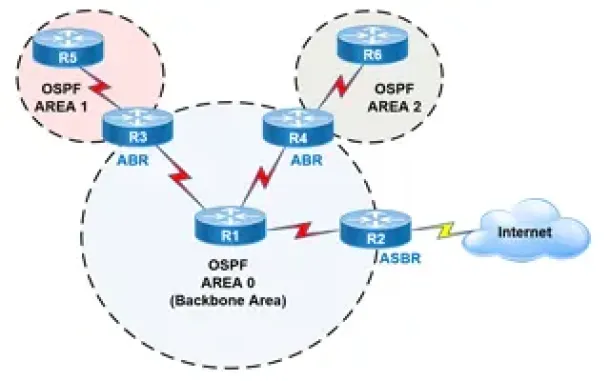
OSPF - Part 2: How OSPF Protocol Works & Basic Concept…
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose (N…
Windows Servers
Creating Windows Users and Groups with Windows 2003
In a Windows server environment, it is very important that only authenticated users are allowed to log in for security reasons. To fulfill this requiremen…
Windows Servers
Troubleshooting Windows Server 2012 R2 Crashes. Analys…
There are umpteen reasons why your Windows Server 2012 R2 decides to present you with a Blue Screen of Death (BSOD) or the stop screen. As virtual machine…
Windows Servers
Configuring Windows Server Roaming Profiles
Windows roaming profiles allow the mobile users of a company to always work with their personal settings from any network computer in a domain. Roaming pr…
Virtualization & VM Backup
SysAdmin Day 2020 - Get your Free Amazon Voucher & Gif…
SysAdmin Day has arrived, and with it, gratitude for all the unsung heroes that 2020 has needed. Your hard work has made it possible for all of us to keep…



















