Suggested Articles:
Ethernet Protocol, CSMA/CD, Collisions
Troubleshooting techniques for Fast Ethernet
This page will primarily discuss problems unique to Fast Ethernet.
The Collision Domain
Incompatible Ethernet Jabber
Auto-negotiation Priorities…
Network Cabling
USB Direct Cable Connection, USB Versions, Specif…
Today, Serial and Parallel Direct Cable Connections are considered obsolete methods of transferring data between computers. The fact is that even USB…
The OSI Model
The OSI Model: Layer 6 - Presentation Layer
The Presentation Layer gets its name from its purpose: It presents data to the Application layer. It's basically a translator and provides coding and…
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 7: TCP Data Payload…
Finally, the last page of our incredible TCP Analysis. As most of you would expect, this section is dedicated to the DATA section that follows the TC…
Featured Subcategories:
Netflow Articles:

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
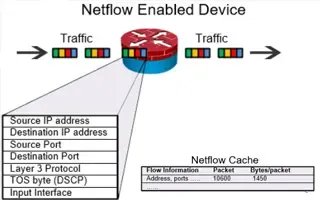
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
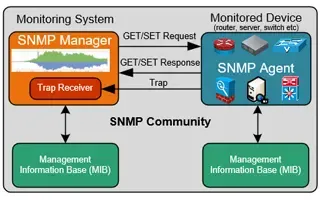
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
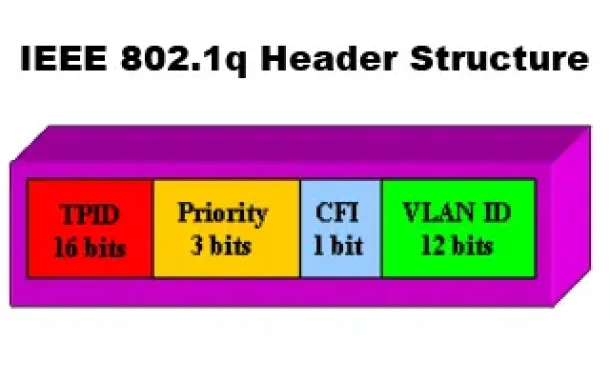
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…

VLAN Networks
VTP Introduction & Modes
The invention of VLANs was very much welcomed by all engineers and administrators, allowing them to extend, redesign and segment their existing network wi…

VLAN Networks
Dynamic VLANs
Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of their…

VLAN Networks
InterVLAN Routing - Routing between VLAN Networks
This article deals with the popular topic of InterVLAN routing, which is used to allow routing & communication between VLAN networks. Our article anal…
Routing
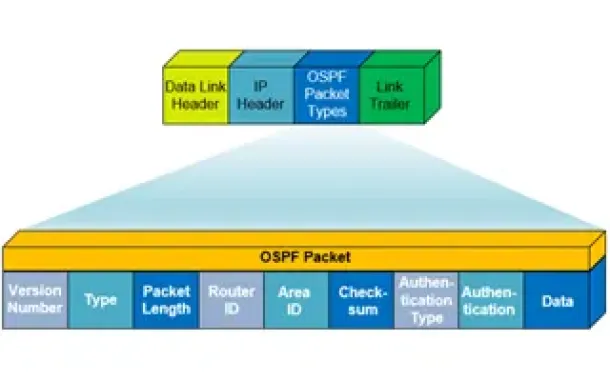
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
Routing
Distance Vector Routing Protocols
Distance Vector routing protocols use frequent broadcasts (255.255.255.255 or FF:FF:FF:FF) of their entire routing table every 30 sec. on all their interf…
Routing
Link State Routing Protocols
Link State routing protocols do not view networks in terms of adjacent routers and hop counts, but they build a comprehensive view of the overall network…
Routing
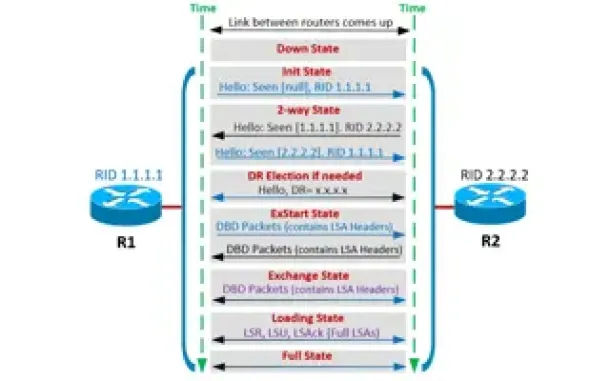
OSPF - Part 4: OSPF Neighbor States – OSPF Neighbor Fo…
This is the third article of our OSPF series which analyzes the different OSPF States routers go through during the OSPF discovery and neighbor forming pr…
Cisco Routers
Configuring NAT Overload On A Cisco Router
NAT (Network Address Translation) is a method that allows the translation (modification) of IP addresses while packets/datagrams are traversing the networ…
Windows Servers
Hyper-V Best Practices - Replica, Cluster, Backup Advi…
Hyper-V has proven to be a very cost effective solution for server consolidation. Evidence of this is also the fact that companies are beginning to move f…
Cisco Routers
Disabling Cisco Router Password Recovery Service
Most Cisco engineers are aware of the classic Password-Recovery service Cisco equipment have. If the device's credentials are lost, then performing the Pa…
Cisco Routers
How To Configure Router On A Stick - 802.1q Trunk To C…
Router-on-a-stick is a term frequently used to describe a setup up that consists of a router and switch connected using one Ethernet link configured as an…



















