Network Fundamentals: Top Picks
Network Fundamentals
Hubs & Repeaters
Network hubs were once the primary method of interconnecting network devices to create a local area network (LAN). Hubs were inexpensive, easy to ins…
Network Fundamentals
Network Switches & Bridges
Network Switches are the evolution of Hubs and Repeaters, and enable the creation of networks by connecting multiple devices together. They are criti…
Network Fundamentals
Network Unicast - Its role and Importance
Unicast is a communication method used in computer networking where data is sent from a single sender to a specific destination device. In this…
Network Fundamentals
Network Broadcast
The term "Broadcast" is used very frequently in the networking world . You will see it in most networking books and articles, or see it happening on…
Featured Subcategories:
Netflow Articles:
Netflow
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
Netflow
Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
Netflow
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
Netflow
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
Network Protocols:
IP Protocol
IP Protocol - Part 2: The Internet Protocol (IP)…
This article examines the Internet Protocol (IP) and its position within the OSI Model. We take a look at the IP Header and all fields contained with…
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 3: TCP Header Lengt…
The third field under close examination is the TCP Header length. There really isn't that much to say about the Header length other than to explain w…
Domain Name System (DNS)
The DNS Protocol - Part 3: DNS Query Message Form…
This section will deal with the analysis of the DNS packets by examining how DNS messages are formatted and the options and variables they contain. T…
Domain Name System (DNS)
The DNS Protocol - Part 4: DNS Response Message F…
The previous article covered the DNS Query message formats. In the article we analysed them in great detail and showed how various options are select…
Subnetting
IP Subnetting - Part 4: Routing Between Subnets
Routing and Communication between subnets is the main topic here. This article analyses communications between subnets. We provide examples on differ…
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 6: TCP Options
The TCP Options (MSS, Window Scaling, Selective Acknowledgements, Timestamps, Nop) are located at the end of the TCP Header which is also why they ar…
IP Protocol
IP Protocol - Part 1: Binary & The Internet Proto…
To understand the Internet Protocol, we need to learn and understand Binary. It is very important to know and understand Binary because part of the I…
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 7: TCP Data Payload…
Finally, the last page of our incredible TCP Analysis. As most of you would expect, this section is dedicated to the DATA section that follows the TC…
STP/ICMP Protocols:
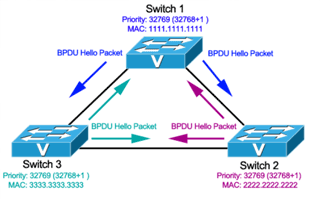
Spanning Tree Protocol (STP)
Spanning Tree Protocol – Part 3: Bridge ID, Prior…
In this article we will examine the Spanning Tree Bridge ID structure, explain why it has increments of 4096, how VLAN information is embedded (for P…

Spanning Tree Protocol (STP)
Spanning Tree Protocol – Part 1: Understand STP P…
One of the most used terms in network is LAN (Local Area Network). It’s a form of network that we encounter in our daily lives, at home, at work, stu…
ICMP Protocol
ICMP Protocol - Part 1: Introduction
The Internet Control Message Protocol (ICMP), is a very popular protocol and actually part of an Internet Protocol (IP) implementation. Because IP wa…
ICMP Protocol
ICMP Protocol - Part 5: Source Quench Message Ana…
The ICMP - Source Quench message is one that can be generated by either a gateway or host. You won't see any such message pop up on your workstation…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
InterVLAN Routing - Routing between VLAN Networks
This article deals with the popular topic of InterVLAN routing, which is used to allow routing & communication between VLAN networks. Our article anal…

VLAN Networks
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…
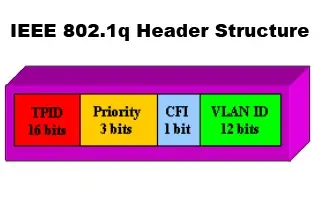
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…

VLAN Networks
VTP Protocol - In-Depth Analysis
The previous article introduced the VTP protocol, we examined how it can be used within a network, to help manage VLANs and ease the administrative overhe…
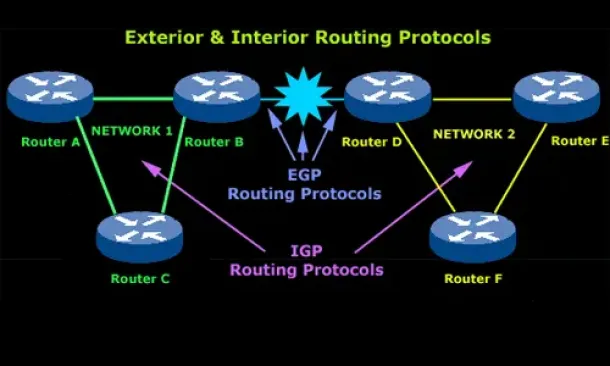
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchange…
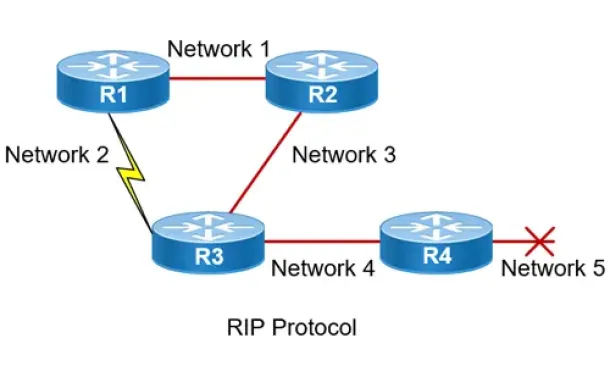
Routing
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…
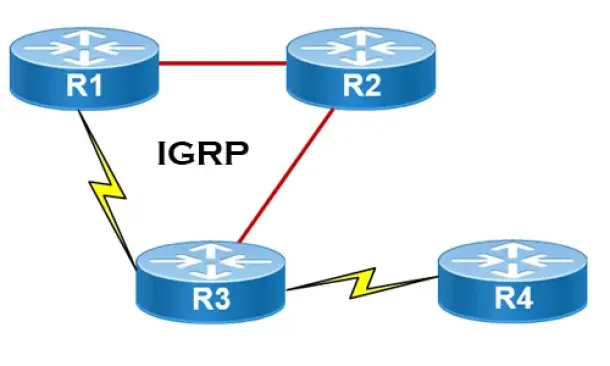
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informati…
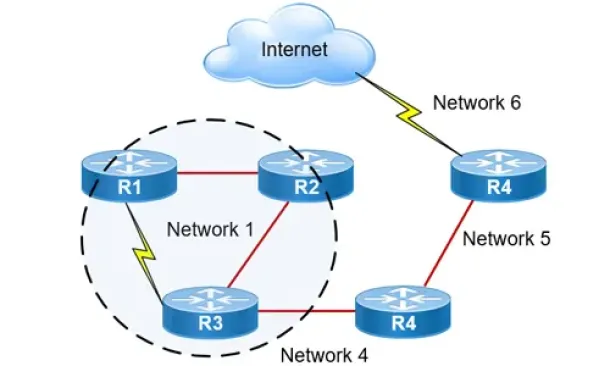
Routing
Hybrid Routing Protocols - Advantages and Disadvantage…
Hybrid routing protocols are a combination of distance-vector and link-state routing protocols, and are used to provide a more efficient and scalabl…
Network Address Translation - NAT
Static NAT - Part 1
Static NAT (also called inbound mapping) is the first mode we're going to talk about and also happens to be the most uncommon between smaller networks.
S…
Network Address Translation - NAT
Network Address Translation (NAT) Overload - Part 2
In our previous article, Network Address Translation (NAT) Overload - Part 1, we explained what NAT Overload is and how it works. This page deals with the…
Network Address Translation - NAT
Network Address Translation (NAT) Concepts
Before we dive into the deep waters of NAT, we need to make sure we understand exactly what NAT does. So let me give you the background of NAT, why it's h…
Network Address Translation - NAT
The Network Address Translation Table
After that simple and informative introduction to the NAT concept, it's time to find out more about how it works and this is where the NAT table comes in…



















