Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
OpenMosix - Part 5: Testing Your Cluster
| Read |
| Read | |
|
Articles:
OpenMosix - Part 3: Using ClusterKnoppix
| Read |
| Read | |
| Read | |
Suggested Articles:
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With Col…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addres…
Network Protocol Analyzers
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…

ManageEngine Firewall Analyzer
Ensuring Compliance and Business Continuity in a…
In the wake of digital transformation, the work landscape as we know it has undergone a dynamic shift. People can now work from home, from the office…
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Featured Subcategories:
WireShark Articles:
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fire…
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emerging…
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enforcemen…
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with the…

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based Po…
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient wa…

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Windows Servers
Windows 2012 Server NIC Teaming – Load Balancing/Failo…
NIC Teaming, also known as Windows Load Balancing or Failover (LBFO), is an extremely useful feature supported by Windows Server 2012 that allows the aggr…
Windows Servers
How to Install/Enable Telnet Client for Windows Server…
IT professionals frequently need connectivity and management tools. The Telnet Client is one of the most basic tools for such activities. Using this tool…
Windows Servers
Configuring Local Group Policy for Windows 2003
Windows 2003 Group Policies allow the administrators to efficiently manage a group of people accessing a resource. Group policies can be used to control b…
Windows Servers
Configuring Windows Server Roaming Profiles
Windows roaming profiles allow the mobile users of a company to always work with their personal settings from any network computer in a domain. Roaming pr…
Popular Topics
SASE & SD-WAN Networks
Converged SASE Backbone – How Leading SASE Provider, C…
Global connectivity is top of mind for many IT teams at organizations of all sizes. We are currently in the middle of a dramatic shift in business and tec…
Windows Servers
How to Install and Configure SNMP for Windows Server 2…
Simple Network Management Protocol (SNMP) is a UDP protocol that uses port 161 to monitor and collect detailed information on any network device supportin…
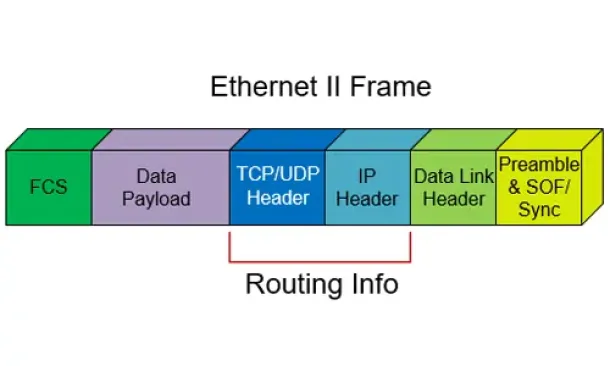
Routing
Routed Protocols
We all understand that TCP/IP, IPX-SPX are protocols which are used in a Local Area Network (LAN) so computers can communicate between with each other and…
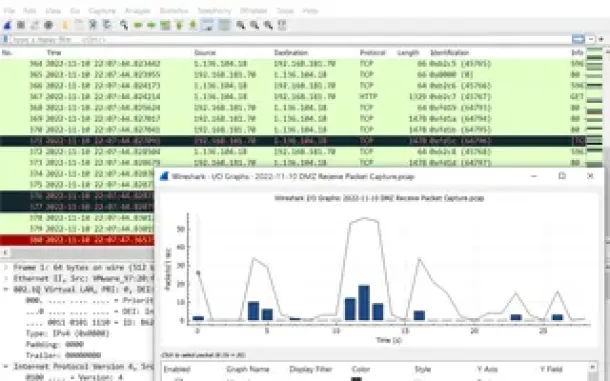
Network Fundamentals
The Importance of a Network Analyzer – Packet Sniffer…
Network Analyzers, also known as Packet Sniffers, are amongst the most popular network tools found inside any Network Engineer’s toolkit. A Network Analyz…
Cisco Switches
Cisco Nexus 7000 Series Module Shutdown and Removal Pr…
This article explains the procedure that should be followed to correctly shutdown/powerdown a Cisco Nexus 7000 series module and remove it from the chassi…
Cisco Routers
Configuring Cisco SSL VPN AnyConnect (WebVPN) on Cisco…
Our Web SSL VPN article written back in 2011 introduced this new wave of VPN services. This article extends the topic by covering the installation a…
Cisco Routers
Cisco GRE and IPSec - GRE over IPSec - Selecting and C…
GRE Tunnels are very common amongst VPN implementations thanks to their simplicity and ease of configuration. With broadcasting and multicasting support…
Cisco CallManager-CCME
Cisco Small Business SPA500 IP Phone Series Administra…
Firewall.cx readers can now access and freely download the Cisco Small Business Administration Guide for Cisco SPA500 series IP phones. The Adminis…



















