Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
ISDN Layers, Protocols & Components
| Read |
|
Articles:
Introduction To The ISDN Protocol
| Read |
|
Articles:
Introduction To Protocols
| Read |
|
Articles:
File Transfer Protocol - FTP
| Read |
|
Articles:
Trivial File Transport Protocol - TFTP
| Read |
|
Articles:
IPSec - Internet Protocol Security
| Read |
Suggested Articles:
Network Cabling
Direct Cable Connection
From the early PC days, Direct Cable Connection (DCC) was the most popular way to transfer data from one PC to another. Of course, it might seem a bi…
Ethernet Protocol, CSMA/CD, Collisions
Late Ethernet Collisions
Late collisions, on the other hand, are not normal and are usually the result of out of spec. cabling or a malfunctioning adapter. A late collision i…
Domain Name System (DNS)
The DNS Protocol - Part 4: DNS Response Message F…
The previous article covered the DNS Query message formats. In the article we analysed them in great detail and showed how various options are select…
Network Cabling
CAT5, CAT5e, CAT6 UTP X-Over / Cross-over Cable
The cross-over (or crossover) CAT5 UTP cable has to be one of the most used cables after the classic straight-thru cable. The cross-over cable allows…
Featured Subcategories:
Netflow Articles:

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
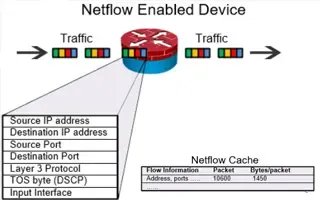
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
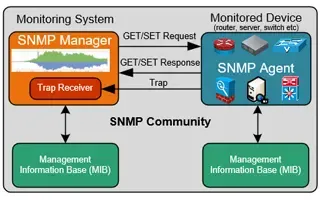
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
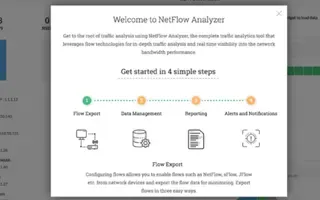
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
Dynamic VLANs
Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of their…

VLAN Networks
The VLAN Concept - Introduction to VLANs
We hear about them everywhere, vendors around the world are constantly trying to push them into every type of network and as a result, the Local Area Netw…

VLAN Networks
VTP Introduction & Modes
The invention of VLANs was very much welcomed by all engineers and administrators, allowing them to extend, redesign and segment their existing network wi…

VLAN Networks
InterVLAN Routing - Routing between VLAN Networks
This article deals with the popular topic of InterVLAN routing, which is used to allow routing & communication between VLAN networks. Our article anal…
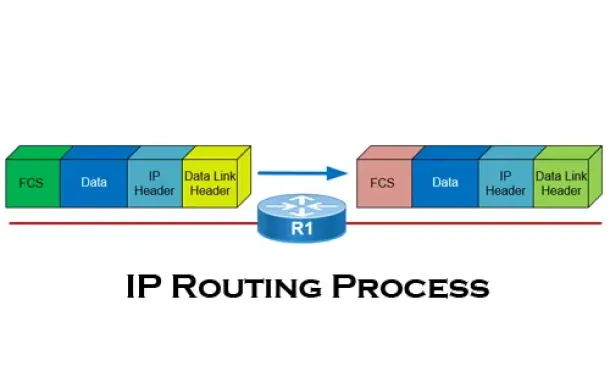
Routing
The IP Routing Process - Step-by-Step Analysis
We are going to analyse what happens when routing occurs on a network (IP routing process). When I was new to the networking area, I thought that all you…
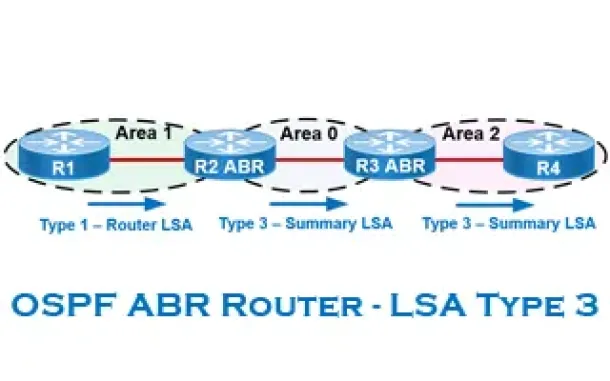
Routing
OSPF - Part 6: OSPF LSA Types - Purpose and Function o…
Our previous article explained the purpose of Link State Update (LSU) packets and examined the Link State Advertisement (LSA) information contained within…
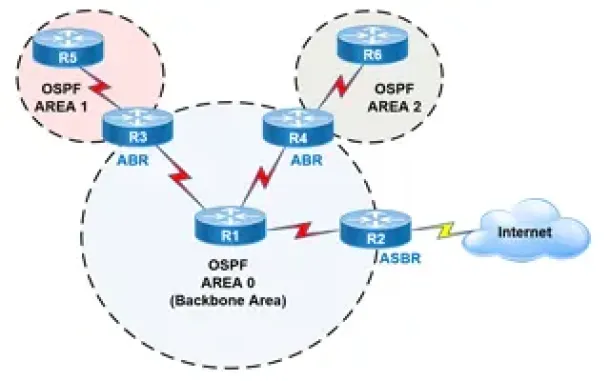
Routing
OSPF - Part 2: How OSPF Protocol Works & Basic Concept…
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose (N…
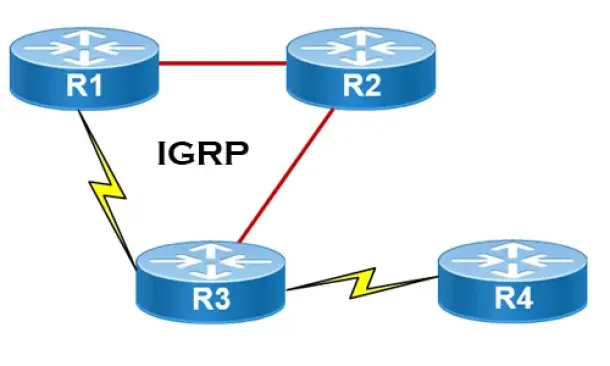
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informati…
Cisco Wireless
Cisco WLC Interfaces, Ports & Their Functionality. Und…
Our previous article introduced Cisco’s popular Wireless ControllerCisco’s popular Wireless Controller (WLC) devices and examined their benefits to enterp…
Cisco Routers
Configuring Dynamic NAT (NAT Overload) On A Cisco Rout…
NAT (Network Address Translation) is a method that allows the translation (modification) of IP addresses while packets/datagrams are traversing the networ…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
Part 1 of our Windows 2003 DHCP Server Advanced Configuration article explained the creation and configuration of DHCP Scope options and how to configure…
SASE & SD-WAN Networks
SASE and VPNs: Reconsidering your Mobile Remote Access…
The Virtual Private Network (VPN) has become the go to security solution for keeping communications between networks and endpoints secure. After all, VPNs…



















