Suggested Articles:
Network Cabling
USB Direct Cable Connection, USB Versions, Specif…
Today, Serial and Parallel Direct Cable Connections are considered obsolete methods of transferring data between computers. The fact is that even USB…
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 2: TCP Sequence & A…
This page will closely examine the Sequence and Acknowledgement numbers. The very purpose of their existence is related directly to the fact that the…
Subnetting
IP Subnetting - Part 3: Subnet Mask Bits & Analys…
So we have covered to some depth the subnetting topic, but there is still much to learn ! We are going to explain here the available subnet masks and…
ICMP Protocol
ICMP Protocol - Part 5: Source Quench Message Ana…
The ICMP - Source Quench message is one that can be generated by either a gateway or host. You won't see any such message pop up on your workstation…
Featured Subcategories:
Netflow Articles:
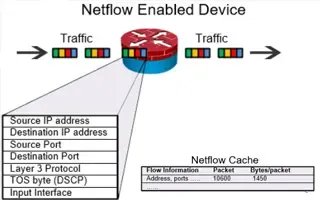
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
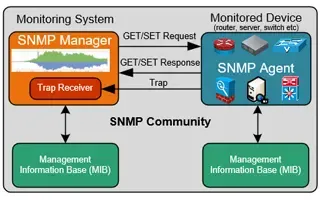
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
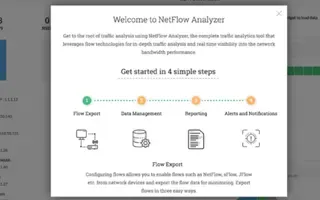
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
Static VLANs
VLANs are usually created by the network administrator, assigning each port of every switch to a VLAN. Depending on the network infrastructure and securit…
VLAN Networks
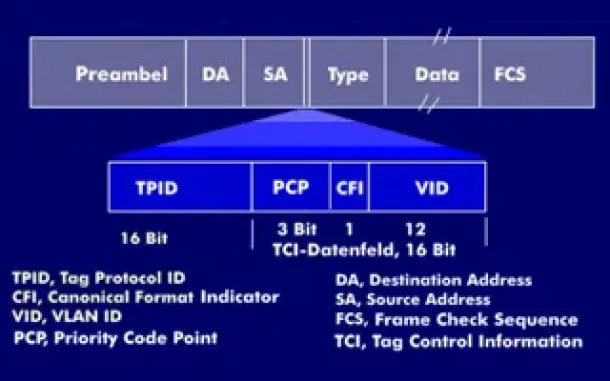
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…
VLAN Networks
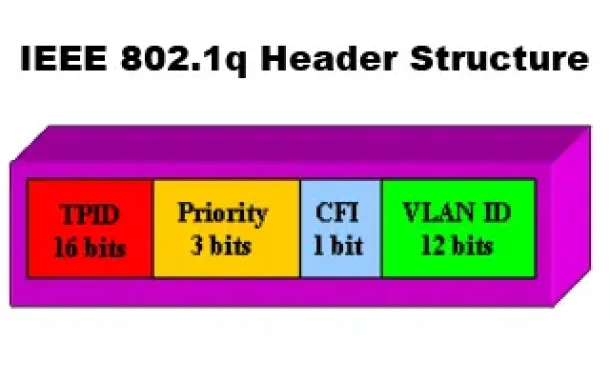
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…
Routing
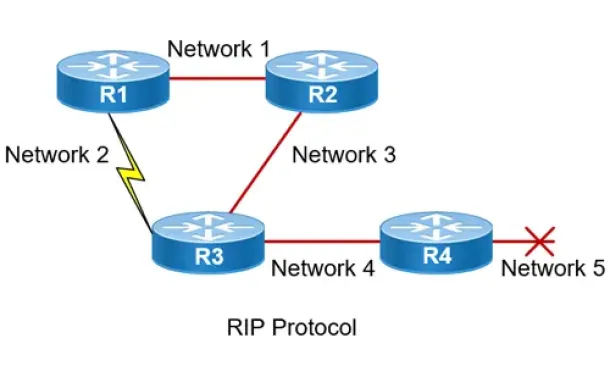
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…
Routing
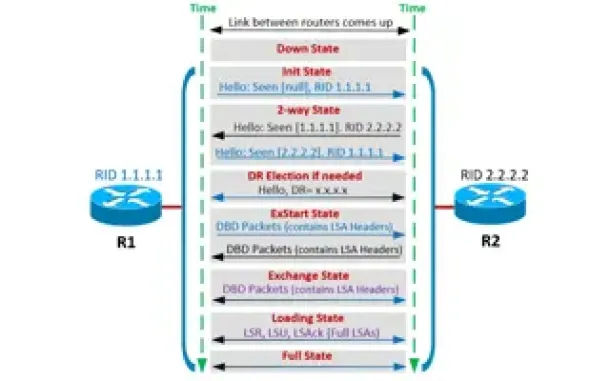
OSPF - Part 4: OSPF Neighbor States – OSPF Neighbor Fo…
This is the third article of our OSPF series which analyzes the different OSPF States routers go through during the OSPF discovery and neighbor forming pr…
Routing
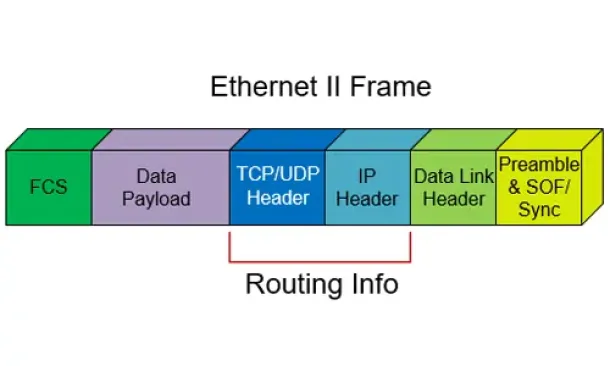
Routed Protocols
We all understand that TCP/IP, IPX-SPX are protocols which are used in a Local Area Network (LAN) so computers can communicate between with each other and…
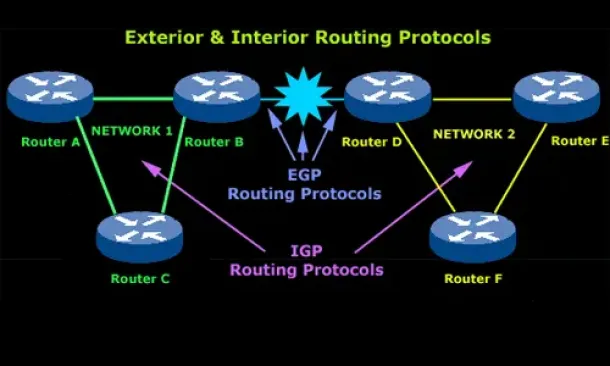
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchange…
Virtualization & VM Backup
5 Most Critical Microsoft M365 Vulnerabilities Reveale…
Microsoft 365 is an incredibly powerful software suite for businesses, but it is becoming increasingly targeted by people trying to steal your data. The g…
Cisco Firewalls
Demystifying Cisco AnyConnect 4.x Licensing. Plus, Plu…
In late 2014, Cisco announced the new licensing model for the latest AnyConnect Secure Mobility client v4.x. With this new version, Cisco introduced a num…
Cisco Routers
Configuring Cisco Dynamic Multipoint VPN (DMVPN) - Hub…
Our DMVPN Introduction article covered the DMVPN concept and deployment designs. We explained how DMVPN combines a number of technologies that give it its…
Windows Servers
Free Webinar: Troubleshooting & Fixing Microsoft Hyper…
Users working with Hyper-V Virtualization would be interested to know that Altaro is hosting a free webinar on the 25th of February 2016 at 4pm CET / 10am…



















