Suggested Articles:
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With Col…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addres…

ManageEngine Firewall Analyzer
Ensuring Compliance and Business Continuity in a…
In the wake of digital transformation, the work landscape as we know it has undergone a dynamic shift. People can now work from home, from the office…
Network Protocol Analyzers
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
OpManager - Network Monitoring & Management
Ensuring Enterprise Network Readiness for Mobile…
Demands for Enterprise networks to properly support mobile users is on a continuous rise making it more than ever necessary for IT departments to pro…
Featured Subcategories:
WireShark Articles:
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo Alt…
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our co…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enforcemen…
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with the…

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based Po…
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient wa…
Windows Servers
Windows 2012 Server Foundation, Essential, Standard &…
FREE Hyper-V & VMware Virtualization Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Windows Server 2012 Editions…
Windows Servers
How to Install and Configure Windows 2012 DNS Server R…
Our previous article covered introduction to the Domain Name System (DNS) and explained the importance of the DNS Server role within the network infrastru…
Windows Servers
How to Install Windows Server 2012 from USB Flash – IS…
Most would remember the days we had to have a CDROM or DVDROM in order to proceed with the installation of an operating system. Today, it is very common i…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
In this article, we will cover more advanced DHCP features and topics such as server options, superscopes, multicast scopes, dynamic DNS, DHCP database ba…
Popular Topics
Windows Servers
The Importance of a Comprehensive Backup Strategy for…
People and companies usually adopt a backup strategy suited to the needs of their working environment. As such, there is no absolute right or wrong method…
VLAN Networks
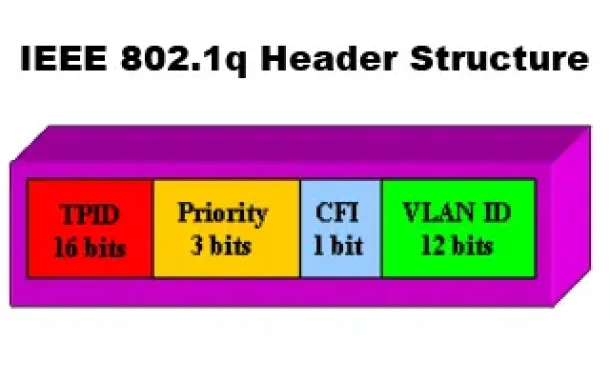
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…
Network Fundamentals
Controlling Broadcasts and Multicasts
The first step in controlling broadcast and multicast traffic is to identify which devices are involved in a broadcast or multicast storm. The following p…
Windows Servers
How to Install Windows Server 2012 from USB Flash – IS…
Most would remember the days we had to have a CDROM or DVDROM in order to proceed with the installation of an operating system. Today, it is very common i…

Cisco Data Center (Nexus/UCS)
Introduction to Cisco Nexus Switches – Nexus Product F…
This article introduces the Cisco Nexus product family (Nexus 9000, Nexus 7000, Nexus 5000, Nexus 3000, Nexus 2000, Nexus 1000V and MDS 9000). We explain…
Cisco Switches
Spanning Tree BPDU Guard and Errdisable Interface Auto…
Running Spanning Tree Protocol (STP) in a large network environment can be a challenging task especially when features/enhancements such as BPDU Filter an…
Cisco Switches
Complete Guide to DHCP Snooping, How it Works, Concept…
This article covers popular Layer 2 & Layer 3 network attacks with a focus on DHCP Starvation Attacks, Man-in-the-Middle attacks, unintentional rogue…
Cisco Routers
Cisco 880W (881W, 886W, 887W, 888W) Multiple - Dual SS…
This article shows how to configure the embedded or integrated access point in a Cisco 880W series router (e.g Cisco 887W, Cisco 886W, Cisco 881W, Cisco 8…



















