MS Server Articles:
Windows Servers
Windows 2012 Server Foundation, Essential, Standa…
FREE Hyper-V & VMware Virtualization Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Windows Server 2012 Edi…
Windows Servers
Free Webinar: Troubleshooting & Fixing Microsoft…
Users working with Hyper-V Virtualization would be interested to know that Altaro is hosting a free webinar on the 25th of February 2016 at 4pm CET /…
Windows Servers
How to Install Windows 2012 Hyper-V via Server Ma…
Our previous article covered the basic concepts of Virtualization and Windows Server 2012 Hyper-V. This article takes a closer look at Microsof…
Windows Servers
Simple Guide on Installing & Configuring a Window…
A Windows Active Directory Certification Authority server (AD CA), also known as a Certificate Authority, is an essential service to every organizati…
Featured Subcategories:
Virtualization & VM Backup Articles:
How to Fix VMware ESXi Virtual Machine 'Invalid S…
In this article, we'll show you how to deal with VMs which are reported to have an Invalid Status as shown in the screenshot below. This is a co…
How to Enable or Disable SSH on VMware ESXi via W…
SSH access to VMware’s ESXi server is by disabled by default however there are many reasons where SSH might be required. VMware and System administra…
Understanding Deduplication. Complete Guide to De…
When considering your VM backup solution, key features such as deduplication are incredibly important. This is not simply from a cost perspective but…
Differences Between VMware vSphere, vCenter, ESXi…
In this article we will cover the differences between VMware ESXi, vSphere and vCenter while also explain the features supported by each vSphere edit…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Linux - Unix
Advanced Linux Commands
Now that you're done learning some of the Basic Linux commands and how to use them to install Linux Software, it's time we showed you some of the other wa…
Linux - Unix
Linux BIND DNS - Part 3: Configuring The db.192.168.0…
The db.192.168.0 zone data file is the second file we need to create and configure for our BIND DNS server. As outlined in the DNS-BIND Introduction, this…
Linux - Unix
Understanding, Administering Linux Groups and User Acc…
In a multi-user environment like Linux, every file is owned by a user and a group. There can be others as well who may be allowed to work with the file. W…
Linux - Unix
Installation and Configuration of Linux DHCP Server
For a cable modem or a DSL connection, the service provider dynamically assigns the IP address to your PC. When you install a DSL or a home cable router b…
Popular Topics
Cisco Routers
Configuring Dynamic NAT (NAT Overload) On A Cisco Rout…
NAT (Network Address Translation) is a method that allows the translation (modification) of IP addresses while packets/datagrams are traversing the networ…
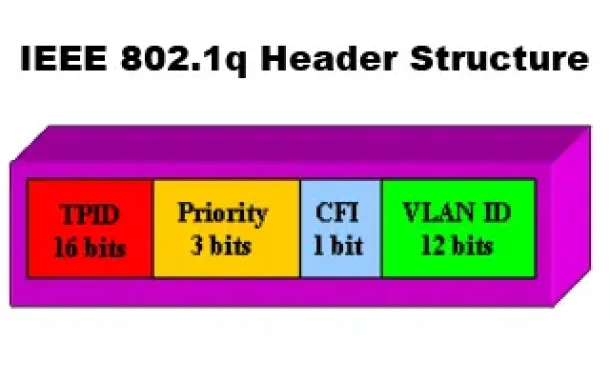
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…
Cisco Switches
Complete Guide to DHCP Snooping, How it Works, Concept…
This article covers popular Layer 2 & Layer 3 network attacks with a focus on DHCP Starvation Attacks, Man-in-the-Middle attacks, unintentional rogue…
Cisco Switches
Installation and Setup of Cisco SG500-52P - 500 Series…
The SG500 series Cisco switches are the next step up from the already popular SG300 Layer-3 switches. Cisco introduced the SG Small Business series switch…


















