Suggested Articles:
Cisco CallManager-CCME
CallManager Express GUI Software Installation & C…
Cisco CallManager Express, also known as CME or CCME, runs on both Cisco ISR Routers and UC500 platform, including UC520, UC540 and UC560.
CallManag…
Cisco Switches
Basic & Advanced Catalyst Layer 3 Switch Configur…
This article covers basic and advanced configuration of Cisco Catalyst Layer-3 switches such as the Cisco Catalyst 3560G, 3560E, 3560-X, 3750, 3750E…
Cisco Routers
Disabling Cisco Router Password Recovery Service
Most Cisco engineers are aware of the classic Password-Recovery service Cisco equipment have. If the device's credentials are lost, then performing t…
Cisco Routers
How To Configure Router On A Stick - 802.1q Trunk…
Router-on-a-stick is a term frequently used to describe a setup up that consists of a router and switch connected using one Ethernet link configured…
Featured Subcategories:
Data Center Articles:

Join Australia’s First Official Cisco Data Center…
It’s a reality – Australia now has its own Official Cisco Data Center User Group (DCUG) and it’s growing fast! Originally inspired by Cisco Champions…

NEXUS NX-OS: Useful Commands, CLI Scripting, Hint…
Whether you’re new to Cisco Nexus switches or have been working with them for years this article will show how to get around the Nexus NX-OS usi…
Complete Guide to Nexus Checkpoint & Rollback Fea…
The Cisco NX-OS checkpoint feature provides the capability to capture at any time a snapshot (backup) of the Cisco Nexus configuration…
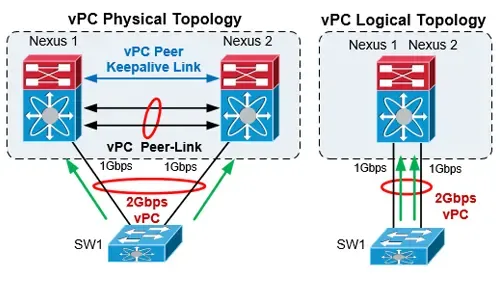
The Complete Cisco Nexus vPC Guide. Features & Ad…
Cisco virtual Port Channel (vPC) is a virtualization technology, launched in 2009, which allows links that are physically connected to two different…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Cisco Switches
End-of-Sale and End-of-Life Announcement for the Cisco…
Cisco announces the end-of-sale and end-of-life dates for the Cisco Catalyst 3750G, 3560G, 3750-E, and 3560-E Series Switches. The last day to order the a…
Cisco Switches
Resolving Cisco Switch & Router ‘DHCP Server Pool Exha…
In previous articles, we showed how it is possible to configure a Cisco router or Catalyst switch to provide DHCP server services to network clients. Ever…
Cisco Switches
Installation of a Cisco Catalyst 4507R-E Layer 3 Switch
Driven by our thirst for technical material and experience, we thought it would be a great idea to start presenting various installations of Cisco equipme…
Cisco Switches
Cisco Nexus 7000 Series Module Shutdown and Removal Pr…
This article explains the procedure that should be followed to correctly shutdown/powerdown a Cisco Nexus 7000 series module and remove it from the chassi…
Cisco Firewalls
Cisco ASA 5500 Series Firewall Modules & Cards – Conte…
Cisco’s Adaptive Security Appliance (ASA) Firewalls are one of the most popular and proven security solutions in the industry. Since the introduction of t…
Cisco Firewalls
Understand & Configure NAT Reflection, NAT Loopback, H…
This article examines the concept of NAT Reflection, also known as NAT Loopback or Hairpinning, and shows how to configure a Cisco ASA Firewall running AS…
Cisco Firewalls
Cisco ASA5500 (5505, 5510, 5520, etc) Series Firewall…
The Cisco ASA 5500 series security appliances have been around for quite some time and are amongst the most popular hardware firewalls available in the ma…
Cisco Firewalls
Upgrading - Uploading AnyConnect Secure Mobility Clien…
This article will show how to download and upload the newer AnyConnect 4.x VPN clients to your Cisco ASA Firewall appliance (5500 & 5500-X Series) and…
Popular Topics
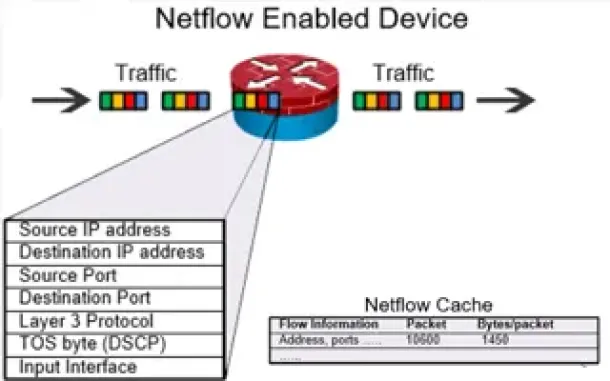
Netflow
Complete Guide to Netflow: How Netflow & its Component…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive into the…

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on P…
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a P…
SASE & SD-WAN Networks
MPLS vs. SD-WAN vs. Internet vs. Cloud Network. Connec…
The Wide Area Network (WAN) is the backbone of the business. It ties together the remote locations, headquarters and data centers into an integrated netwo…

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…



















