Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
MS Server Articles:
Windows Servers
How to Enable & Configure Shadow Copy for Shared…
When you shadow copy a disk volume, you are actually generating a snapshot of the changes made to the folders and files within the disk volume at a c…
Windows Servers
Free Webinar: Migrating from Hyper-V to VMware
If your organization is planning to migration from a Hyper-V virtualization environment to VMware then this FREE webinar is just for you.
Aimed towa…
Windows Servers
How to Enable ‘Web Server’ Certificate Template O…
In this article we will show you how to enable the ‘Web Server’ certificate template option on a Windows Certification Authority (Windows CA) Server…
Windows Servers
How to Install and Configure SNMP for Windows Ser…
Simple Network Management Protocol (SNMP) is a UDP protocol that uses port 161 to monitor and collect detailed information on any network device supp…
Featured Subcategories:
Virtualization & VM Backup Articles:
World Backup Day with Free Amazon Voucher and Pri…
Celebrate World Backup Day and WIN with Altaro!
We all remember how grateful we were to have backup software when facing so many data loss mishaps…
SysAdmin Day 2020 - Get your Free Amazon Voucher…
SysAdmin Day has arrived, and with it, gratitude for all the unsung heroes that 2020 has needed. Your hard work has made it possible for all of us to…
The Backup Bible. A Free Complete Guide to Disast…
The Free Backup Bible Complete Edition written by backup expert and Microsoft MVP Eric Siron, is comprised of 200+ pages of actionable content divide…

Ultimate Guide: Install Windows 11 on VMware ESXi…
In this article, we’ll show you how to setup or install Microsoft Windows 11 on VMware’s ESXi servers and bypass the Trusted Platform Module version…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Linux - Unix
Linux BIND DNS - Part 5: Configure Secondary (Slave) D…
Setting up a Secondary (or Slave) DNS sever is much easier than you might think. All the hard work is done when you setup the Master DNS server by creatin…
Linux - Unix
Linux VIM / Vi Editor - Tutorial - Basic & Advanced Fe…
When you are using Vim, you want to know three things - getting in, moving about and getting out. Of course, while doing these three basic operations, you…
Linux - Unix
Linux BIND DNS - Part 2: Configuring db.domain Zone D…
It's time to start creating our zone files. We'll follow the standard format, which is given in the DNS RFCs, in order to keep everything neat and less co…
Linux - Unix
Installation and Configuration of Linux DHCP Server
For a cable modem or a DSL connection, the service provider dynamically assigns the IP address to your PC. When you install a DSL or a home cable router b…
Popular Topics
Cisco Routers
MPLS Case Study: Why Route Summarization is not Recomm…
MPLS generates Implicit Null label (The Implicit NULL label is the label that has a value of 3) for directly connected interfaces and for the summary rout…
Cisco Switches
End-of-Sale and End-of-Life Announcement for the Cisco…
Cisco announces the end-of-sale and end-of-life dates for the Cisco Catalyst 3750G, 3560G, 3750-E, and 3560-E Series Switches. The last day to order the a…
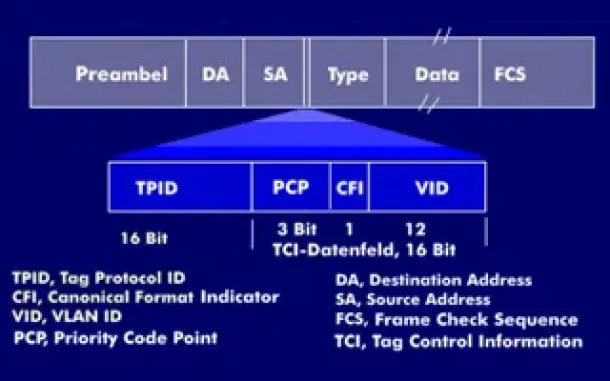
VLAN Networks
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…
Cisco Routers
Cisco Type 7 Password Decrypt / Decoder / Crack Tool
The Firewall.cx Cisco Password Decoder Tool (see below) provides readers with the ability to decrypt 'Type 7' cisco passwords.
For security reasons, we d…


















