Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
|
Articles:
802.3 Fast Ethernet (100 Mbit/Sec) Model
| Read |
|
Articles:
Migrating From Ethernet To Fast Ethernet
| Read |
| Read | |
| Read | |
|
Articles:
The Novell Proprietary Frame Format
| Read |
|
Articles:
The IEEE 802.3 SNAP Frame Format
| Read |
|
Articles:
The Ethernet II Frame Format
| Read |
|
Articles:
The IEEE 802.3 Frame Format
| Read |
|
Articles:
Manchester Signal Encoding
| Read |
|
Articles:
IEEE 802.3 Interframe Spacing
| Read |
| Read | |
|
Articles:
Propagation Delay
| Read |
|
Articles:
Late Ethernet Collisions
| Read |
|
Articles:
Early Ethernet Collisions
| Read |
|
Articles:
Introduction to Ethernet Collisions
| Read |
|
Articles:
What is CSMA/CD ?
| Read |
Suggested Articles:
Network Fundamentals
The Importance of a Network Analyzer – Packet Sni…
Network Analyzers, also known as Packet Sniffers, are amongst the most popular network tools found inside any Network Engineer’s toolkit. A Network A…
Network Cabling
USB Direct Cable Connection, USB Versions, Specif…
Today, Serial and Parallel Direct Cable Connections are considered obsolete methods of transferring data between computers. The fact is that even USB…
Ethernet Protocol, CSMA/CD, Collisions
The IEEE 802.3 SNAP Frame Format
While the original 802.3 specification worked well, the IEEE realized that some upper layer protocols required an Ethertype to work properly. For exa…

Network Fundamentals
Network Data Transmission
Network data transmission refers to the process of sending and receiving information between two or more devices connected to a network. It is a crit…
Featured Subcategories:
Netflow Articles:
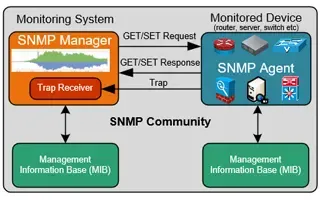
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
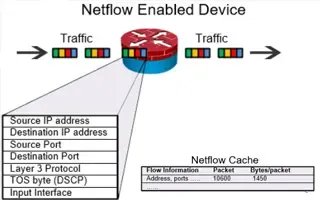
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Stati…
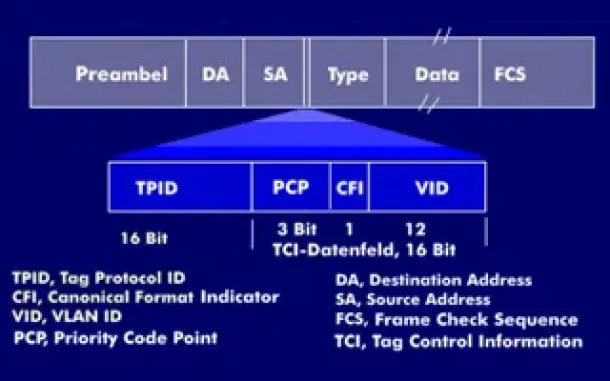
VLAN Networks
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…

VLAN Networks
InterVLAN Routing - Routing between VLAN Networks
This article deals with the popular topic of InterVLAN routing, which is used to allow routing & communication between VLAN networks. Our article anal…

VLAN Networks
VTP Protocol - In-Depth Analysis
The previous article introduced the VTP protocol, we examined how it can be used within a network, to help manage VLANs and ease the administrative overhe…
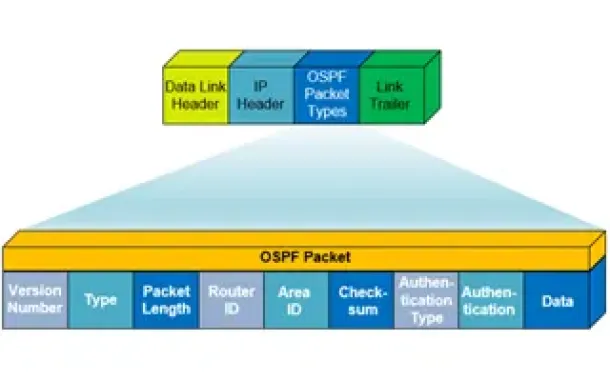
Routing
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
Routing
Link State Routing Protocols
Link State routing protocols do not view networks in terms of adjacent routers and hop counts, but they build a comprehensive view of the overall network…
Routing
Hybrid Routing Protocols - Advantages and Disadvantage…
Hybrid routing protocols are a combination of distance-vector and link-state routing protocols, and are used to provide a more efficient and scalabl…
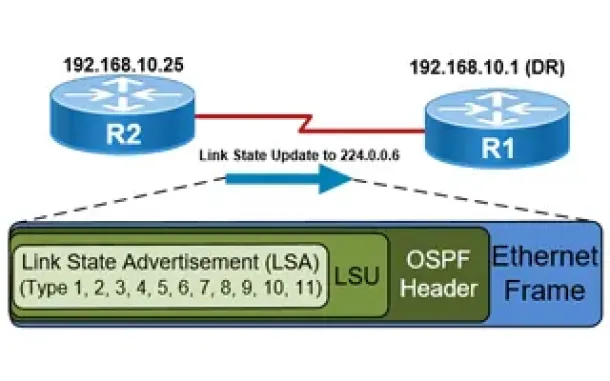
Routing
OSPF - Part 5: Analysis of OSPF Link State Update (LSU…
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router recei…
Cisco Routers
How To Configure ISDN Internet Dialup On A Cisco Router
Some time ago, when broadband and ADSL wasn't available, analog and digital (ISDN) modems were the only way to connect to the Internet. Even though today…
Cisco Firewalls
Cisco ASA5500 (5505, 5510, 5520, etc) Series Firewall…
The Cisco ASA 5500 series security appliances have been around for quite some time and are amongst the most popular hardware firewalls available in the ma…
Cisco Routers
How to Capture Packets on your Cisco Router with Embed…
If you’re tired of setting up SPAN sessions to capture network traffic transiting your network and Cisco router, it’s time to start using Cisco’s Embedded…
Cisco Switches
Resolving Cisco Switch & Router ‘DHCP Server Pool Exha…
In previous articles, we showed how it is possible to configure a Cisco router or Catalyst switch to provide DHCP server services to network clients. Ever…



















