Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
Are Cloud-Based Services Overhyped?
| Read |
|
Articles:
What if it Rains in the Cloud?
| Read |
| Read | |
| Read | |
|
Articles:
Email Security - Can't Live Without It!
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Network Protocol Analyzers
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…

OpManager - Network Monitoring & Management
Maximizing Network Security: A Deep Dive into OpM…
In the rapidly evolving landscape of cyber threats, network security has never been more crucial. With the frequency and sophistication of cyberattac…

EventLog Analyzer
Unlock Deep Visibility & Insight into Windows Ser…
This article explores the exciting new features of Windows Server 2022 and emphasizes the critical role of analyzing Windows Server logs. You'll also…
Featured Subcategories:
WireShark Articles:
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fire…
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emerging…

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo Alt…
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our co…
Windows Servers
The Importance of a Comprehensive Backup Strategy for…
People and companies usually adopt a backup strategy suited to the needs of their working environment. As such, there is no absolute right or wrong method…
Windows Servers
Troubleshooting Windows Server 2012 R2 Crashes. Analys…
There are umpteen reasons why your Windows Server 2012 R2 decides to present you with a Blue Screen of Death (BSOD) or the stop screen. As virtual machine…
Windows Servers
Windows Server 2012 File Server Resources Manager (FSR…
The Windows Server 2008 first carried FSRM or Fie Server Resources Manager, which allowed administrators to define the file types that users could save to…
Windows Servers
How to Easily Change Network Card Profile / Network Lo…
Network Location Awareness (NLA) is a feature offered on Windows Server 2012 R2 and all Windows workstation editions from Windows 8.1 and above, including…
Popular Topics
Windows Servers
Windows Server 2012 File Server Resources Manager (FSR…
The Windows Server 2008 first carried FSRM or Fie Server Resources Manager, which allowed administrators to define the file types that users could save to…

Network Fundamentals
Securing Your Home Network
In today's world, securing your home network is more important than ever. With the increasing number of cyberattacks, data breaches, and online frauds, pr…
Windows Servers
Free Webinar & eBook on Microsoft Licensing for Virtua…
Microsoft Licensing for Virtual environments can become a very complicated topic, especially with all the misconceptions and false information out there…
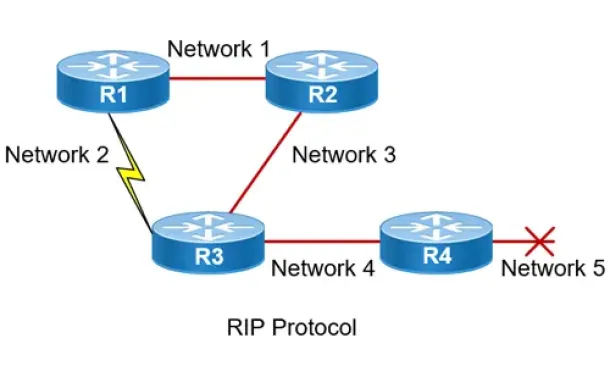
Routing
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…
Cisco CallManager-CCME
CallManager Express & UC500 Series: Changing Backgroun…
Cisco's CallManager Express (Cisco router platform & UC520, UC540 & UC560) offers a number of customisation features aimed to allow the CCME admin…
Cisco Switches
Complete Guide to DHCP Snooping, How it Works, Concept…
This article covers popular Layer 2 & Layer 3 network attacks with a focus on DHCP Starvation Attacks, Man-in-the-Middle attacks, unintentional rogue…
Cisco Wireless
Cisco WLC Interfaces, Ports & Their Functionality. Und…
Our previous article introduced Cisco’s popular Wireless ControllerCisco’s popular Wireless Controller (WLC) devices and examined their benefits to enterp…
Cisco Routers
Enabling & Configuring SSH on Cisco Routers. Restrict…
This article shows how to configure and setup SSH for remote management of Cisco IOS Routers. We’ll show you how to check if SSH is supported by your IOS…



















