Achieving Modern Compliance: Navigate PCI DSS v4.0 with Firewall Analyzer
 In an era where cyber threats are growing in both volume and sophistication, failing to meet security compliance standards is no longer just a legal issue—it’s a business risk with potentially catastrophic consequences. According to IBM’s 2023 Cost of a Data Breach Report, the global average cost of a data breach has surged to $4.45 million, marking a 15% increase over the past three years. This figure encompasses detection, escalation, breach response, and long-term remediation efforts—but the financial impact doesn’t stop there.
In an era where cyber threats are growing in both volume and sophistication, failing to meet security compliance standards is no longer just a legal issue—it’s a business risk with potentially catastrophic consequences. According to IBM’s 2023 Cost of a Data Breach Report, the global average cost of a data breach has surged to $4.45 million, marking a 15% increase over the past three years. This figure encompasses detection, escalation, breach response, and long-term remediation efforts—but the financial impact doesn’t stop there.
Key Topics:
- Core Risks of Non-Compliance
- Data Security
- Customer Trust
- Operational Continuity
- Ongoing Compliance
- Streaming Compliance with PCI DSS by using Firewall Anazyer
- What is PCI DSS Compliance?
- Key Steps to Achieving PCI DSS Compliance
- Scope Determination
- Gap Identification
- Issue Resolution – Remediation
- Documentation and Evidence Collection
- Regular Audits and Continuous Monitoring
- PCI DSS v4.0: A Significant Evolution in Payment Security
- The Significance of Firewalls Under PCI DSS v4.0
- Summary
Core Risks of Non-Compliance
Non-compliance with data protection regulations, such as the EU’s General Data Protection Regulation (GDPR), can lead to penalties of up to €20 million or 4% of global annual turnover, whichever is greater. Similar regulatory frameworks exist globally, including CCPA in California, APRA CPS 234 in Australia, and PCI DSS for organizations handling payment card data—all carrying hefty financial and reputational risks for violations.
From a technical standpoint, one of the most critical metrics revealed by the IBM report is the average time to identify and contain a breach: 277 days. That’s over nine months of potential data leakage, operational downtime, security compliance standards, and customer attrition. During this time, IT departments are often forced into reactive firefighting mode, diverting resources from strategic initiatives to breach mitigation and forensics.
ManageEngine Firewall Analyzer - Limited time Free Download
Beyond fines and recovery costs, non-compliance undermines core areas of business resilience:
- Data Security: Weak or outdated controls expose sensitive systems and assets—such as PII, PHI, and cardholder data—to exploitation. Endpoint vulnerabilities, unpatched software, misconfigured cloud environments, and lack of encryption are common culprits.
- Customer Trust: In today’s privacy-conscious market, trust is currency. A single incident of exposed credentials or stolen payment data can erode years of brand loyalty, especially if poor compliance practices are to blame.
- Operational Continuity: Regulatory investigations and forced shutdowns can disrupt service availability. For organizations dependent on 24/7 uptime—like finance, healthcare, and e-commerce—this can translate to significant revenue loss.
- Ongoing Compliance: Achieving compliance isn't a one-off event—it requires continuous monitoring, periodic audits, incident response planning, and employee training. Integrating these practices into your InfoSec program helps future-proof your organization against emerging threats and evolving standards.
In short, compliance is not just a checkbox—it’s a cornerstone of sound IT governance and cyber risk management. Companies that ignore this reality not only fall behind technically but also leave themselves open to escalating risks that can cripple their business from the inside out.
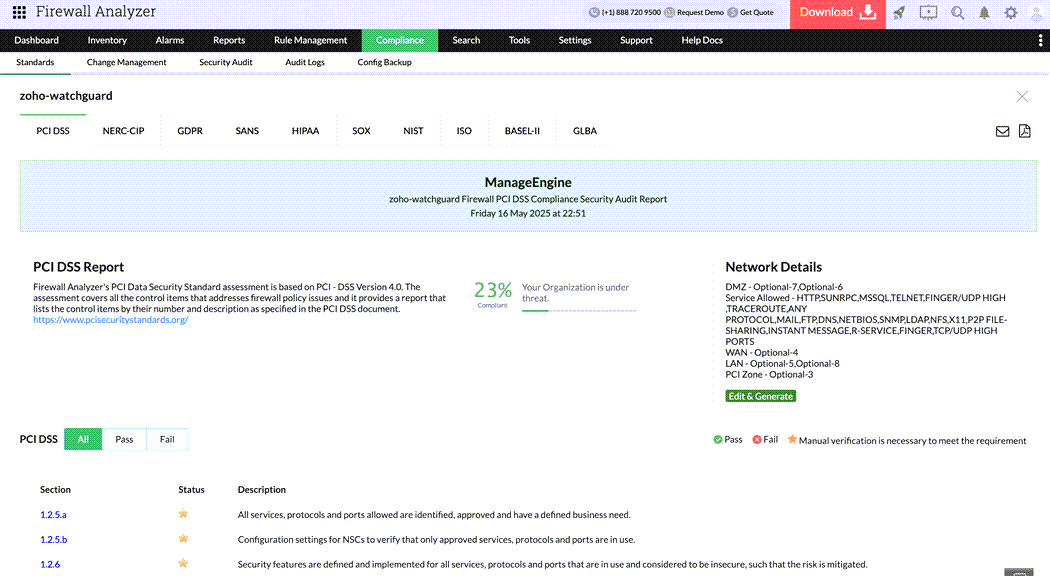
Streamlining Compliance with PCI DSS by using Firewall Analyzer
The Payment Card Industry Data Security Standard (PCI DSS) provides a comprehensive framework of security best practices for any organization that stores, processes, or transmits credit card data. Its goal is to ensure that cardholder information is protected at every stage—from acceptance and processing to storage and transmission.
Key Steps to Achieving PCI DSS Compliance
Achieving PCI DSS compliance requires a structured, multi-phase approach that integrates with your organization’s broader cybersecurity strategy. Here’s a closer look at the core steps:
Scope Determination
Organizations must begin by identifying all system components, applications, and personnel involved in handling cardholder data. This process, often called scoping, helps define the boundaries of the Cardholder Data Environment (CDE). Proper network segmentation can help reduce scope—and with it, the cost and complexity of compliance.
Gap Identification
Conducting a gap analysis involves assessing your current security controls against PCI DSS requirements. This step helps uncover vulnerabilities or non-compliant practices—such as weak encryption, outdated software, or improperly configured access controls—that need to be addressed.
Issue Resolution - Remediation
Once gaps are identified, organizations must implement corrective measures. Common actions include:
- Installing and configuring firewalls
- Applying antivirus/malware protection across all systems
- Strengthening access control and authentication
- Encrypting sensitive data both in transit and at rest
These efforts not only align with PCI DSS but also improve your overall security resilience.
Documentation and Evidence Collection
Maintaining up-to-date, comprehensive documentation is critical. This includes security policies, standard operating procedures (SOPs), incident response plans, audit logs, and configuration records. During audits, these documents provide proof of compliance and show due diligence.
Regular Audits and Continuous Monitoring
PCI DSS compliance is an ongoing effort, not a one-time event. Regular internal and external audits, as well as continuous monitoring and testing, help ensure ongoing compliance and readiness for evolving threats. This includes:
- Quarterly vulnerability scans
- Annual penetration tests
- Continuous log analysis and anomaly detection
As the security landscape changes, the PCI DSS standard is regularly revised to maintain a secure payment card environment. We see this with PCI DSS v4.0, which features significant revisions to its framework.
PCI DSS v4.0: A Significant Evolution in Payment Security
As cyber threats continue to evolve, so too must the standards that protect sensitive data. PCI DSS v4.0, the latest version of the framework, introduces major updates designed to reflect current technologies and security practices. These changes revolve around four core objectives:
Adapting to the Evolving Payment Ecosystem
Version 4.0 acknowledges the rise of cloud computing, mobile payments, and hybrid environments. It modernizes security controls to address threats posed by dynamic infrastructures and remote access.
Promoting Continuous Security
Unlike previous versions that focused heavily on point-in-time assessments, v4.0 emphasizes continuous security monitoring and risk management—ensuring businesses remain secure between formal audits.
Enabling Flexibility and Customization
PCI DSS v4.0 allows for customized implementations, giving organizations the flexibility to meet requirements in ways best suited to their infrastructure, provided they can demonstrate equivalent or better security outcomes.
Enhancing Validation Methods
Stronger validation processes ensure organizations not only implement the required controls but also operate them effectively and consistently.
The Significance of Firewalls Under PCI DSS v4.0
Firewalls remain a cornerstone of PCI DSS compliance and are crucial for establishing a protective barrier between trusted internal networks and untrusted external ones, effectively blocking unauthorized access to sensitive data. PCI DSS v4.0 further underscores their importance in securing cardholder data environments (CDEs).
The key firewall requirements in PCI DSS v4.0 are as follows;
1. Implement and Maintain a Firewall Setup to Protect Cardholder Data
- Required firewall setup: Organizations are required to configure and manage a firewall to control connections from untrusted networks to system components within the CDE.
- Review and revise rules: Firewall and router configuration rules require regular review and updates to ensure ongoing adherence to security standards.
- Segmentation: To enforce PCI DSS compliance and mitigate risk, firewalls should be deployed to separate the CDE from the rest of the organization's network.
2. Enhanced Authentication and Access Controls
- Multi-Factor Authentication (MFA) is now a must, especially for administrators and remote access users.
- Access Control Lists (ACLs) must be tightly configured to enforce the principle of least privilege, limiting access to only those who truly need it.
3. Logging and Monitoring
- Event Logging: All access attempts and firewall-related events should be logged. Logs must be protected from unauthorized access and tampering.
- Real-Time Monitoring: Security teams must continuously monitor logs and alerts for anomalies, enabling swift threat detection and response.
4. Routine Testing and Evaluation
- Vulnerability Scans: These should be performed at least quarterly and after any major change to firewall configurations.
- Penetration Testing: Annual testing (or after major network changes) helps ensure your firewall setup can withstand real-world attack scenarios.
PCI DSS v4.0 represents a significant step forward in securing the payment ecosystem. With its emphasis on flexibility, continuous improvement, and stronger validation, organizations now have a more adaptable and effective framework for protecting cardholder data. By properly configuring and managing firewalls—and integrating them into a broader culture of compliance—businesses can reduce their attack surface, maintain regulatory alignment, and earn the trust of customers in an increasingly security-conscious world.
Summary
To support organizations on their PCI DSS v4.0 compliance journey, Firewall Analyzer now fully aligns with the latest standard. This powerful solution helps enterprises build and maintain secure firewall configurations, a core requirement for protecting cardholder data and reducing cybersecurity risks. With preconfigured PCI DSS compliance reports, real-time alerts, and automated firewall rule reviews, Firewall Analyzer simplifies ongoing compliance management and ensures that firewall policies remain robust and up to date. It also maintains detailed firewall log analysis for clear, actionable audit trails, making regulatory audits faster and more efficient.
Start your free trial of Firewall Analyzer today, or contact our team to learn how it can help strengthen your organization’s network security and PCI DSS compliance posture.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!