Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
MS Server Articles:
Windows Servers
Windows 2003 DHCP Server Installation & Configura…
DHCP (Dynamic Host Configuration Protocol) is a protocol that allows clients on a network to request network configuration settings from a server run…
Windows Servers
Simple Guide on Installing & Configuring a Window…
A Windows Active Directory Certification Authority server (AD CA), also known as a Certificate Authority, is an essential service to every organizati…
Windows Servers
Free Webinar: Scripting & Automation in Hyper-V w…
System Center Virtual Machine Manager (SCVMM) provides some great automation benefits for those organizations that can afford the hefty price tag. Ho…
Windows Servers
Configuring Local Group Policy for Windows 2003
Windows 2003 Group Policies allow the administrators to efficiently manage a group of people accessing a resource. Group policies can be used to cont…
Featured Subcategories:
Virtualization & VM Backup Articles:
How to Enable or Disable SSH on VMware ESXi via W…
SSH access to VMware’s ESXi server is by disabled by default however there are many reasons where SSH might be required. VMware and System administra…
How to Fix VMware ESXi Virtual Machine 'Invalid S…
In this article, we'll show you how to deal with VMs which are reported to have an Invalid Status as shown in the screenshot below. This is a co…
FREE Webinar - Fast Track your IT Career with VMw…
Everyone who attends the webinar has a chance of winning a VMware VCP course (VMware Install, Config, Manage) worth $4,500!
Climbing the career ladd…
How to Enable SNMP on VMware ESXi Host & Configur…
In this article we will show you how to enable SNMP on your VMware ESXi host, configure SNMP Community string and configure your ESXi firewall to all…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Linux - Unix
Installation and Configuration of Linux DHCP Server
For a cable modem or a DSL connection, the service provider dynamically assigns the IP address to your PC. When you install a DSL or a home cable router b…
Linux - Unix
Linux BIND DNS - Part 6: Linux BIND - DNS Caching
In the previous articles, we spoke about the Internet Domain Hierarchy and explained how the ROOT servers are the DNS servers, which contain all the infor…
Linux - Unix
Critical 15 Year-old Linux Security Hole (Ghost) Revea…
Security researchers at qualys.com yesterday released information on a critical 15 year-old Linux security hole which affects millions of Linux systems da…
Linux - Unix
How To Secure Your Linux Server or Workstation - Linux…
Below are some of the most common recommendations and method to effectively secure a Linux Server or Workstation.
Boot Disk
One of the foremost requisit…
Popular Topics
Cisco Switches
Forcing A Cisco Catalyst Switch To Use 3rd Party SFP M…
Many companies are seeking for Cisco SFP alternatives to help cut down the costs on these expensive modules.
A frequent customer problem with Cisco's new…
Cisco Routers
How To Configure Router On A Stick - 802.1q Trunk To C…
Router-on-a-stick is a term frequently used to describe a setup up that consists of a router and switch connected using one Ethernet link configured as an…
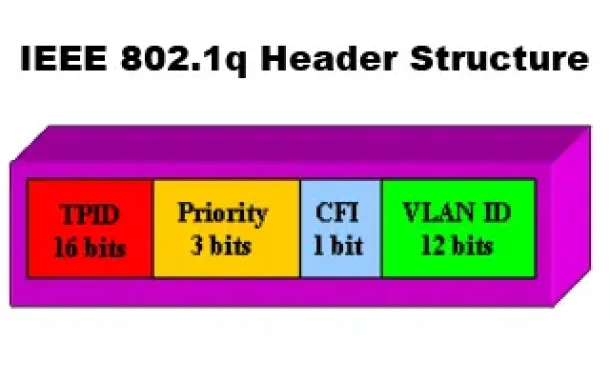
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…
Windows Workstations (XP, 7, 8, 10, 11)
Configuring Windows 7 To Provide Secure Wireless Acces…
Not many people are aware that Windows 7 has built-in capabilities that allow it to be transformed into a perfectly working access point so that wireless…


















