Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
Are Cloud-Based Services Overhyped?
| Read |
|
Articles:
What if it Rains in the Cloud?
| Read |
| Read | |
| Read | |
|
Articles:
Email Security - Can't Live Without It!
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
OpManager - Network Monitoring & Management
Boost Network Security and Efficiency with Intell…
Network alerts are vital for maintaining your network's health, efficiency, and security, ensuring seamless daily operations. They act as an early wa…
Network Protocol Analyzers
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…

ManageEngine Firewall Analyzer
Achieving Modern Compliance: Navigate PCI DSS v4…
In an era where cyber threats are growing in both volume and sophistication, failing to meet security compliance standards is no longer just a legal…

OpManager - Network Monitoring & Management
AIOps for Modern IT Operations: Automating Monito…
The days of relying solely on static monitoring dashboards and manual firefighting are long gone. Today’s environments demand automation-first operat…
Featured Subcategories:
WireShark Articles:
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on P…
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a P…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall PAN-OS…
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, saf…
Windows Servers
Free Webinar: Migrating from Hyper-V to VMware
If your organization is planning to migration from a Hyper-V virtualization environment to VMware then this FREE webinar is just for you.
Aimed toward Hy…
Windows Servers
The Importance of a Comprehensive Backup Strategy for…
People and companies usually adopt a backup strategy suited to the needs of their working environment. As such, there is no absolute right or wrong method…
Windows Servers
How to Install Desktop Icons (Computer, User’s Files…
One of the first things IT Administrators and IT Managers notice after a fresh installation of Windows 2012 Server is that there are no Desktop Icons apar…
Windows Servers
Configuring Windows Server Roaming Profiles
Windows roaming profiles allow the mobile users of a company to always work with their personal settings from any network computer in a domain. Roaming pr…
Popular Topics
Routing
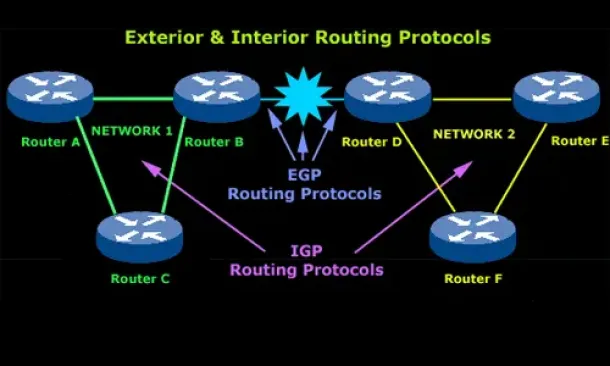
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchange…
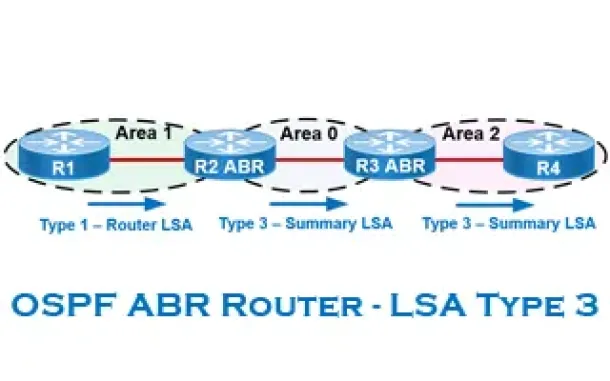
Routing
OSPF - Part 6: OSPF LSA Types - Purpose and Function o…
Our previous article explained the purpose of Link State Update (LSU) packets and examined the Link State Advertisement (LSA) information contained within…
Windows Servers
Installing Windows Server 2012 Active Directory via Se…
This article serves as an Active Directory tutorial covering installation and setup of a Windows 2012 Domain Controller using Windows Server Manager (GUI)…
SASE & SD-WAN Networks
The Need for a Converged SASE Platform. Converging Net…
The digital transformation is pushing applications to the cloud, the 2020-2022 pandemic shifted employees to work from home, and the number of resulting n…
Cisco Routers
How To Secure Your Cisco Router Using Cisco AutoSecure…
In today’s complex network environments securing your network routers can be a daunting task, especially when there are so many CLI commands and parameter…
Cisco Switches
Basic & Advanced Catalyst Layer 3 Switch Configuration…
This article covers basic and advanced configuration of Cisco Catalyst Layer-3 switches such as the Cisco Catalyst 3560G, 3560E, 3560-X, 3750, 3750E, 3750…
Cisco Firewalls
Upgrading - Uploading AnyConnect Secure Mobility Clien…
This article will show how to download and upload the newer AnyConnect 4.x VPN clients to your Cisco ASA Firewall appliance (5500 & 5500-X Series) and…
Cisco Switches
Installation and Setup of Cisco SG500-52P - 500 Series…
The SG500 series Cisco switches are the next step up from the already popular SG300 Layer-3 switches. Cisco introduced the SG Small Business series switch…



















