Master Your Firewall: 6 Expert-Backed Steps to Boost Security, Performance, and Compliance
 In today’s evolving threat landscape, firewall audits are more than just a best practice—they're a critical line of defense. Regular audits ensure your firewall configurations are aligned with organizational security policies, eliminate inefficiencies, and reduce exposure to cyber risks. Just as importantly, they help organizations maintain compliance with regulatory standards such as PCI DSS, HIPAA, SOX, and GDPR, avoiding costly penalties and reputational damage. Beyond compliance, effective firewall audits offer operational clarity and control, giving IT and security teams complete visibility into traffic flows and rule configurations.
In today’s evolving threat landscape, firewall audits are more than just a best practice—they're a critical line of defense. Regular audits ensure your firewall configurations are aligned with organizational security policies, eliminate inefficiencies, and reduce exposure to cyber risks. Just as importantly, they help organizations maintain compliance with regulatory standards such as PCI DSS, HIPAA, SOX, and GDPR, avoiding costly penalties and reputational damage. Beyond compliance, effective firewall audits offer operational clarity and control, giving IT and security teams complete visibility into traffic flows and rule configurations.
A key part of this process lies in maintaining a solid network security policy, which defines who can access your network, what actions are permitted, and how traffic is managed across your infrastructure. However, simply defining rules isn’t enough. As networks scale, applications evolve, and new threats emerge, these rules can become outdated, redundant, or poorly configured. Without routine audits, rule sets often bloat—clogging performance, creating security gaps, and complicating compliance efforts.
To help you stay ahead, this article outlines six essential steps for performing a thorough firewall rule audit—from documentation and identifying redundancies, to reviewing rule order, verifying policy compliance, conducting log analysis, and implementing revisions.
We’ll see how tools like Firewall Analyzer can help simplify and automate the entire firewall audit process. From offering deep visibility into your rule base to identifying unused or risky configurations, it delivers the insights you need to clean up and optimize your firewall policies. By highlighting compliance issues, streamlining rule management, and supporting detailed reporting, Firewall Analyzer empowers your team to maintain a security posture that is both robust and audit-ready—all while reducing manual effort and minimizing the risk of misconfigurations.
Key Topics:
- Why do you Need Firewall Rule Audits?
- Enhanced Performance
- Improved Security
- Simplified Compliance
- Operation Clarity and Control
- Future-Readiness
- Audit Firewall Rules: A Step-by-Step Guide
- Begin with Documentation
- Identify Redundancies and Unused Rules
- Review Rule Order
- Verify Compliance with Policies
- Log Analysis
- Revisions and Summary
- Simplify Firewall Rule Audits with Firewall Analyzer
- Automated Rule Management
- Comprehensive Rule Visibility
- Smart Optimization Recommendations
- Pre-Change Impact Analysis
- Rule Cleanup
- Built-In Compliance Assurance
- Firewall Rule Audit Checklist
- Pre-Audit Preparation
- Rule Base Review
- Optimization & Cleanup
- Change Management
- Compliance & Reporting
- Building a Strong Firewall Environment: Efficiency, Security & Compliance
- Summary
Why Do You Need Firewall Rule Audits?
 A well-maintained and optimized firewall rule base is not just a best practice—it’s a necessity for maintaining a secure, high-performing, and compliant network.
A well-maintained and optimized firewall rule base is not just a best practice—it’s a necessity for maintaining a secure, high-performing, and compliant network.
Here’s why regular firewall rule audits should be a cornerstone of your network security strategy:
- Enhanced Performance: Firewalls process every incoming and outgoing packet against the rules configured. A bloated or disorganized rule base can slow down this process, leading to latency and system strain. Regular audits help eliminate redundant or obsolete rules, streamlining traffic flow and improving overall firewall efficiency.
- Improved Security: As your network grows, so does the risk of misconfigured or outdated firewall rules going unnoticed. These rules can become blind spots—potentially allowing unauthorized access or leaving the network vulnerable to attacks. By identifying and removing overly permissive, duplicate, or unused rules, audits help close these security gaps and reinforce your network defenses.
- Simplified Compliance: Regulatory standards like PCI DSS, HIPAA, SOX, and GDPR require organizations to maintain well-documented and effective security controls. A clean and auditable rule base makes it significantly easier to demonstrate compliance, pass security assessments, and respond to audits without last-minute scrambles.
- Operational Clarity and Control: Firewall rule audits bring transparency to rule sets, helping network administrators better understand rule logic, dependencies, and potential conflicts. This clarity is essential for effective policy management and quicker troubleshooting.
- Future-Readiness: Regular rule audits prepare your infrastructure for scaling, cloud migrations, or network restructuring by ensuring your security policies remain aligned with business goals and technical requirements.
In short, firewall rule audits are vital for maintaining a secure, efficient, and resilient network—today and into the future.
Grab your free download now to see how Firewall Analyzer streamlines your firewall rule audit process, effectively detects and resolves security vulnerabilities plus compliance concerns.
Audit Firewall Rules : A Step-by-Step Guide
Conducting effective firewall rule audits is crucial for maintaining network security. By adhering to these six key practices, you can ensure a successful firewall rule audit, helping to keep your defenses strong and alert.
Step 1: Begin with Documentation
Appropriate documentation is crucial for comprehending the current firewall configuration and identifying which rules may require review or modification. This initial step lays the foundation for the audit by providing insights into the firewall’s performance. Start by compiling a list of all existing firewall rules, including those that manage inbound and outbound traffic, as well as rules that control access between various network segments.
Step 2. Identify Redundancies and Unused Rules
Having duplicate rules can cause confusion and slow down the firewall’s performance, while unused rules just take up space. By getting rid of or combining these unnecessary and outdated rules, you can make the firewall work better and more securely. So, go through the list to spot any duplicate or unused rules.
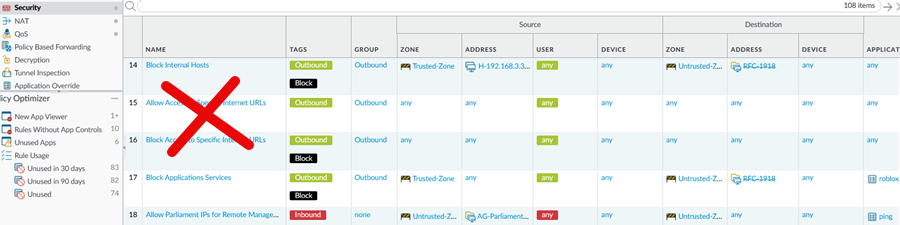
Step 3. Review Rule Order
Firewalls handle rules in a top-to-bottom sequence. It’s important to place specific rules before general ones to avoid conflicts and ensure that traffic is filtered correctly. Properly ordered rules help prevent unauthorized access or the blocking of legitimate traffic, reducing the risk of security problems and interruptions in operations.
Step 4. Verify Compliance with Policies
Following security policies and regulations is essential for keeping a strong security stance and avoiding legal problems. Make sure your firewall rules align with your organization's security policies and industry standards. This means checking that the rules enforce proper access controls and data protection measures, as well as conducting regular security audits.
Step 5. Log Analysis
Log analysis helps you see how effectively the rules are working and spot any changes needed to improve protection against new threats. Looking at these logs can uncover patterns or unusual behavior that may signal potential security risks. Be sure to review firewall logs to identify any strange or suspicious activities.
Step 6. Revisions and Summary
After analyzing the logs, make changes to the firewall rules as needed. This could mean adding new rules, changing existing ones, or getting rid of old rules. Regular updates keep the firewall effective for security and performance, helping to fix any issues and respond to new threats. Finally, summarize the audit process, main findings, actions taken, and suggestions in a detailed report, which will also help with future audits and improvements.
Simplify Firewall Rule Audits with ManageEngine Firewall Analyzer
Managing firewall rules manually can be tedious, error-prone, and time-consuming—especially in complex network environments. ManageEngine Firewall Analyzer takes the guesswork out of the equation by automating and streamlining the firewall rule audit process. It’s an intelligent, all-in-one solution that helps uncover inefficiencies, tighten security, and ensure compliance. Here’s how it makes a difference:
1. Automated Rule Management:
Manually managing firewall rules across multiple devices can be complex and error-prone—especially in dynamic IT environments where configurations change frequently. ManageEngine Firewall Analyzer simplifies this process by automating rule management tasks. Whether you’re adding new rules, modifying existing ones, or retiring obsolete entries, the tool ensures changes are applied consistently across your entire firewall infrastructure. This automation reduces the chances of human error, minimizes configuration drift, and helps maintain a well-structured and orderly rule base. By removing the manual overhead, your IT and security teams can focus on higher-value tasks without compromising control or accuracy.
2. Comprehensive rule visibility:
Understanding your firewall rule base is the first step toward optimizing it. Firewall Analyzer offers a detailed, centralized view of all your firewall rules—regardless of vendor or device. It highlights rules that are unused, redundant, overly permissive, or outdated, giving you the insight needed to assess and improve your security posture.
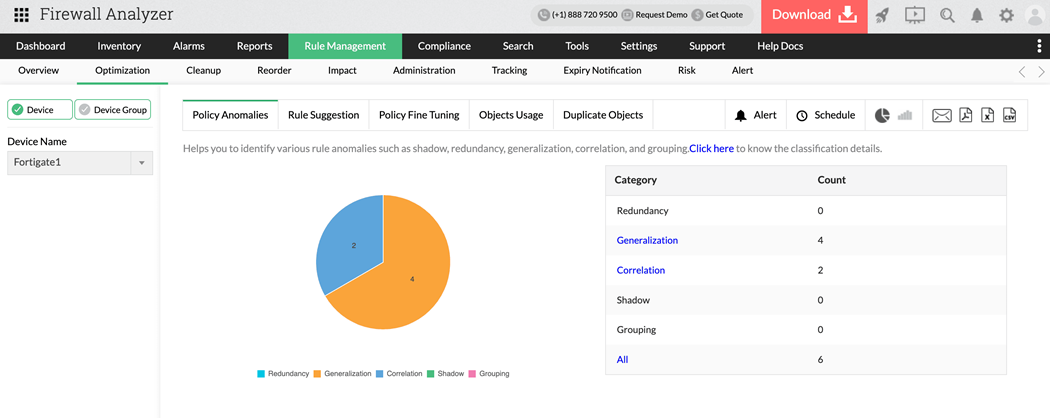
This visibility extends across multiple devices and policies, helping you quickly identify inefficiencies or potential risks that may have otherwise gone unnoticed. With intuitive dashboards and visual reports, the tool makes it easier to audit rule sets, spot anomalies, and maintain clarity even in highly complex environments.
3. Smart Optimization recommendations:
Over time, firewall rule sets can become chaotic, with rules stacked in inefficient or conflicting sequences. Firewall Analyzer uses intelligent analysis to assess how rules are used and how they interact with traffic. Based on real-time usage data and rule complexity, it recommends an optimal sequence that prioritizes frequently hit rules and groups similar policies together. This reordering reduces packet processing time and enhances overall firewall performance.
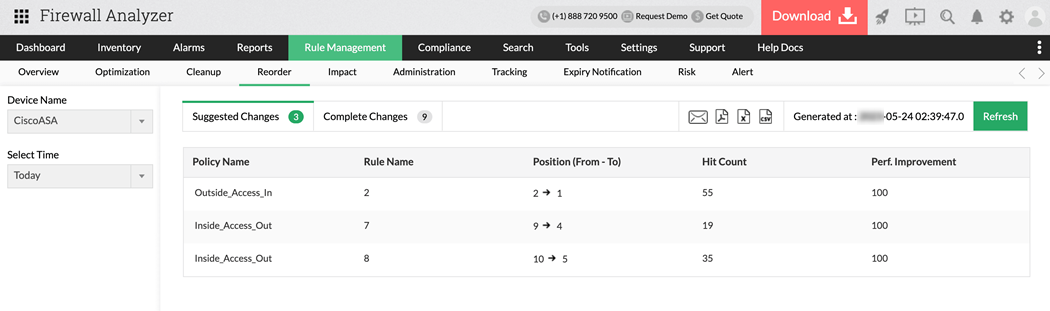
You get more than just data—you get actionable recommendations that help your network run faster and smarter, all while maintaining or improving your security standards.
4. Pre-Change Impact Analysis:
Every new rule introduced into a firewall carries the risk of unintended consequences—such as shadowing existing rules, opening unexpected access paths, or creating conflicts. Firewall Analyzer’s impact analysis feature helps you avoid these pitfalls by simulating the effect of a new rule before it’s deployed. It evaluates how proposed changes interact with existing policies, identifies potential issues, and provides a preview of the outcome.
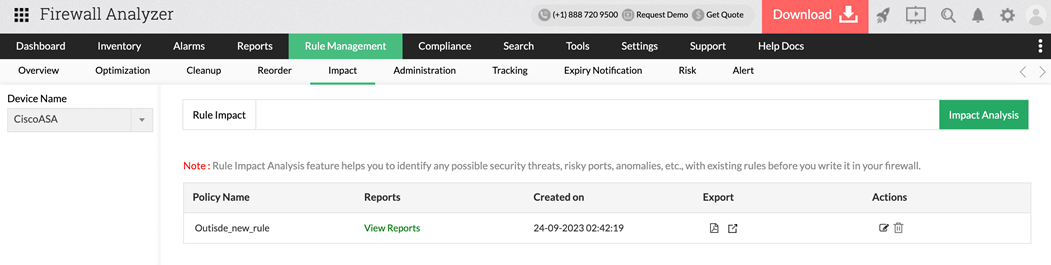
This proactive approach ensures that every change is deliberate and secure, reducing the risk of misconfigurations that could compromise network protection.
5. Rule Cleanup:
Outdated and unused rules are not just clutter—they’re a security liability. Over time, these unnecessary entries accumulate, increasing the complexity of firewall management and creating blind spots that attackers can exploit. Firewall Analyzer continuously scans your rule base to identify rules, objects, and interfaces that are no longer in use. It then offers clear, actionable cleanup suggestions to help you safely remove or archive them.
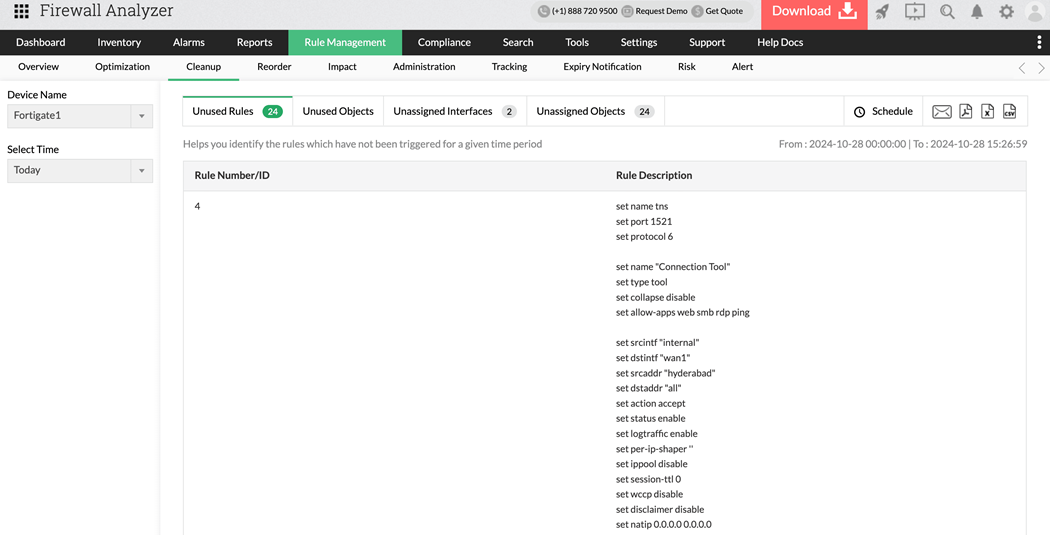
Regular rule cleanup keeps your firewall lean and efficient, reduces processing overhead, and strengthens your network’s overall security posture.
6. Built-In Compliance Assurance:
Keeping up with industry regulations like PCI DSS, HIPAA, SOX, and GDPR requires ongoing attention to firewall configurations and documentation. Firewall Analyzer simplifies compliance management with built-in tools that automatically check your firewall rule base against key compliance requirements. It provides detailed audit reports, change logs, and rule violation alerts, helping you prepare for internal and external audits with confidence.
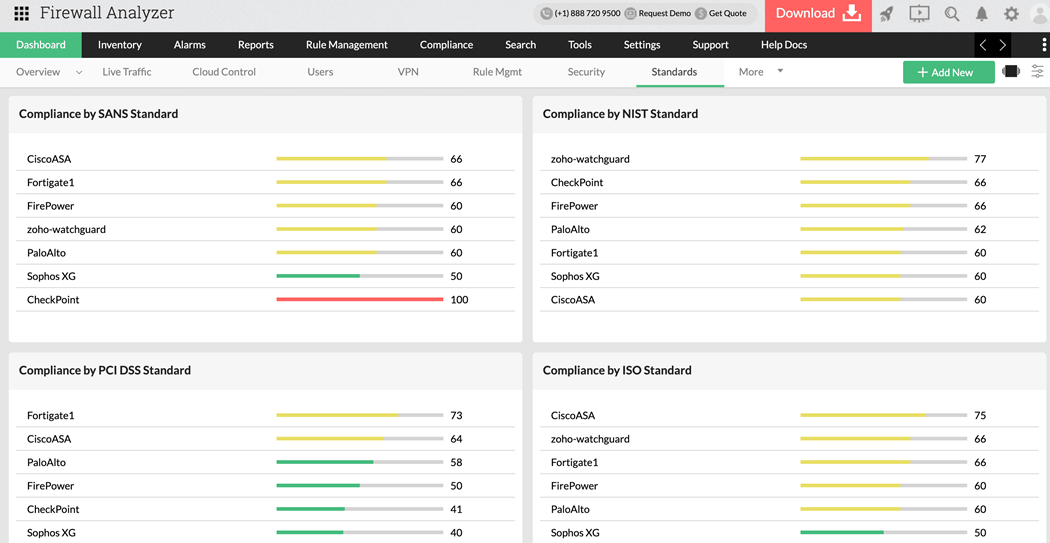
These comprehensive compliance features not only reduce audit preparation time but also help prove due diligence in maintaining a secure and standards-compliant network environment.
Firewall Rule Audit Checklist
Use this checklist to perform a thorough and effective firewall rule audit. The steps below are simplified and accelerated using tools like ManageEngine Firewall Analyzer.
Pre-Audit Preparation
- Collect and back up current firewall configurations.
- Identify key compliance requirements (e.g., PCI DSS, HIPAA, GDPR).
- Define audit scope: which firewalls, zones, or rule sets?
Rule Base Review
- Identify and document all existing firewall rules.
- Detect unused or obsolete rules.
- Highlight redundant, shadowed, or conflicting rules.
- Check for overly permissive rules (e.g., “ANY” source/destination/port).
Optimization & Cleanup
- Reorder rules based on hit count and rule complexity.
- Remove or disable inactive or expired rules.
- Consolidate similar rules where possible.
- Clean up unused objects, interfaces, and address groups.
Change Management
- Perform impact analysis before deploying new rules.
- Document rule changes and justifications.
- Implement version control for configurations.
Compliance & Reporting
- Generate compliance-specific reports (e.g., PCI DSS firewall audit report).
- Maintain audit logs and change history.
- Set up automated alerts for policy violations or risky configurations.
Building a Strong Firewall Environment: Efficiency, Security, and Compliance
Optimizing the firewall rule base through a firewall rule audit isn’t just about boosting performance; it’s also about keeping your network secure and compliant. By keeping track of rules, spotting duplicates, checking the order of the rules, ensuring compliance, analyzing logs, and making needed changes, you can greatly improve your firewall’s effectiveness. ManageEngine’s Firewall Analyzer has the tools to automate and simplify this entire process. This solution simplifies the process of establishing and managing an effective, secure, and compliant firewall setup.
Grab your free download now to see how Firewall Analyzer streamlines your firewall rule audit process, effectively detects and resolves security vulnerabilities plus compliance concerns.
Summary
In an era where cyber threats are growing in scale and sophistication, firewall audits have become a strategic necessity. They go beyond technical housekeeping—playing a vital role in enforcing your network security policy, preserving operational clarity, and ensuring your organization remains aligned with strict regulatory standards like PCI DSS, HIPAA, SOX, and GDPR. By following a structured approach that includes documenting rules, eliminating redundancies, optimizing rule order, verifying compliance, analyzing logs, and applying informed revisions, you can transform your firewall from a static control into a dynamic security asset. And with the support of advanced tools like ManageEngine Firewall Analyzer, IT and security teams can move from reactive to proactive—automating audits, reducing complexity, and gaining full control over their firewall environments. The result? A network that’s not only secure and compliant, but also agile and performance-optimized.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!



















