Suggested Articles:

ManageEngine Firewall Analyzer
Discover the Ultimate Firewall Management Tool: 7…
Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectively…
Network Protocol Analyzers
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…

ManageEngine Firewall Analyzer
Master Your Firewall: 6 Expert-Backed Steps to Bo…
In today’s evolving threat landscape, firewall audits are more than just a best practice—they're a critical line of defense. Regular audits ensure yo…

EventLog Analyzer
Event Log Monitoring System: Implementation, Chal…
An event log monitoring system, often referred to as an event log management, is a critical component to IT security & Management, that helps org…
Featured Subcategories:
WireShark Articles:
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
The Benefits of Palo Alto Networks Firewall Single Pas…
What makes Palo Alto Networks Next-Generation Firewall (NGFW) so different from its competitors is its Platform, Process and Architecture. Palo Alto Netwo…
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enforcemen…
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with the…
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall PAN-OS…
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, saf…

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo Alt…
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our co…
Windows Servers
Download Altaro Free VM Backup & Win a PlayStation 4 P…
We have some exciting news for you today!
Altaro has launched a great contest in celebration of SysAdmin Day on 27th July!
They will be giving away Amaz…
Windows Servers
Free Hyper-V eBook - Create, Manage and Troubleshoot Y…
With the introduction of Hyper-V on the Windows Server platform, virtualization has quickly become the de facto standard for all companies seeking to cons…
Windows Servers
Windows 2012 Server Foundation, Essential, Standard &…
FREE Hyper-V & VMware Virtualization Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Windows Server 2012 Editions…
Windows Servers
Hyper-V Best Practices - Replica, Cluster, Backup Advi…
Hyper-V has proven to be a very cost effective solution for server consolidation. Evidence of this is also the fact that companies are beginning to move f…
Popular Topics
Virtualization & VM Backup
FREE Webinar - Fast Track your IT Career with VMware C…
Everyone who attends the webinar has a chance of winning a VMware VCP course (VMware Install, Config, Manage) worth $4,500!
Climbing the career ladder in…
Virtualization & VM Backup
The Backup Bible. A Free Complete Guide to Disaster Re…
The Free Backup Bible Complete Edition written by backup expert and Microsoft MVP Eric Siron, is comprised of 200+ pages of actionable content divided int…
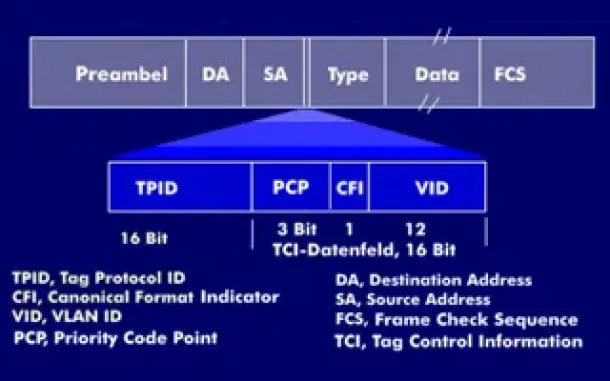
VLAN Networks
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…
Windows Servers
Windows 2003 DHCP Server Installation & Configuration
DHCP (Dynamic Host Configuration Protocol) is a protocol that allows clients on a network to request network configuration settings from a server running…
Cisco Routers
Cisco Router Modes
One of the greatest perhaps features of Cisco routers is that most commands used in the IOS software they run on, are identical across multiple platforms…
Cisco CallManager-CCME
How To Stop CallManager (CUCM) 7, 8, 9, 10.5 with MGCP…
Cisco Unified CallManager (CUCM) and its Voice Gateway relies on the telecommunication provider (telco) to send the correct call details for every incomin…
Cisco Wireless
Configuring Cisco WLC Link Aggregation (LAG) with Port…
Cisco Wireless Controllers (WLC) support the configuration of Link Aggregation (IEEE 802.3ad - LAG) which bundles the controller ports into a single port…
Cisco Switches
Cisco Catalyst 4500 Series Zero-Downtime IOS Upgrade P…
The Supervisor Engine is the heart of the Cisco Catalyst 4500 and 6500 series switches. It is the equivalent of an engine in a car. Every packet that ente…



















