Suggested Articles:

ManageEngine Firewall Analyzer
Ensuring Compliance and Business Continuity in a…
In the wake of digital transformation, the work landscape as we know it has undergone a dynamic shift. People can now work from home, from the office…

ManageEngine Firewall Analyzer
Challenges & Solutions to Managing Firewall Rules…
In today's interconnected digital landscape, where businesses rely heavily on networked systems and the internet for their operations, the importance…

ManageEngine Firewall Analyzer
Discover the Ultimate Firewall Management Tool: 7…
Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectively…
Network Protocol Analyzers
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
Featured Subcategories:
WireShark Articles:
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fire…
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emerging…
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Windows Servers
Simple Guide on Installing & Configuring a Windows 201…
A Windows Active Directory Certification Authority server (AD CA), also known as a Certificate Authority, is an essential service to every organization’s…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
Part 1 of our Windows 2003 DHCP Server Advanced Configuration article explained the creation and configuration of DHCP Scope options and how to configure…
Windows Servers
Troubleshooting Windows Server 2012 R2 Crashes. Analys…
There are umpteen reasons why your Windows Server 2012 R2 decides to present you with a Blue Screen of Death (BSOD) or the stop screen. As virtual machine…
Windows Servers
How to Install/Enable Telnet Client for Windows Server…
IT professionals frequently need connectivity and management tools. The Telnet Client is one of the most basic tools for such activities. Using this tool…
Popular Topics
Windows Servers
Windows 2003 DNS Server Installation & Configuration
DNS is used for translating host names to IP addresses and the reverse, for both private and public networks (i.e.: the Internet). DNS does this by using…
SASE & SD-WAN Networks
MPLS vs. SD-WAN vs. Internet vs. Cloud Network. Connec…
The Wide Area Network (WAN) is the backbone of the business. It ties together the remote locations, headquarters and data centers into an integrated netwo…
Network Protocol Analyzers
How to Use Multi-Segment Analysis to Troubleshoot Netw…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troubleshoot as…
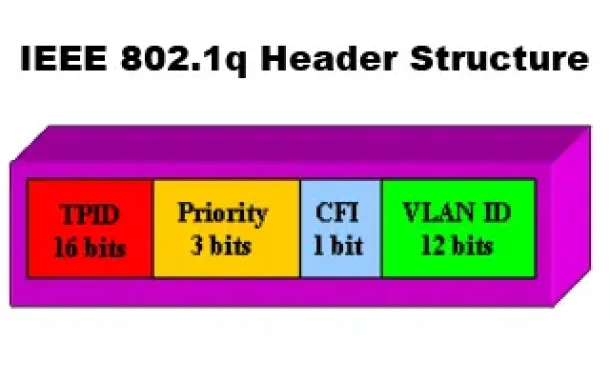
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…
Cisco CallManager-CCME
Introduction to Cisco Unified Communication Manager Ex…
We have been hearing about VoIP for many years now and while some have never worked with it, it has become today's standard in IP Communications and Priva…
Cisco Routers
How to Restrict Cisco IOS Router VPN Client to Layer-4…
In our article Cisco VPN Client Configuration - Setup for IOS Router we explained how to setup up a Cisco IOS router to support Cisco IPSec VPN clie…
Cisco Services & Technologies
Unified Communications Components - Understanding Your…
What Is Unified Communications (UC)?
Unified communications is a very popular term these days and we see it appearing on almost every vendor as the…
Cisco Wireless
Wireless (Wifi) WEP WPA WPA2 Key Generator
The Firewall.cx Wireless LAN Key Generator will allow the generation of a WEP or WPA ASCII based encryption key and will provide the equivalent HEX or…



















