Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
Are Cloud-Based Services Overhyped?
| Read |
|
Articles:
What if it Rains in the Cloud?
| Read |
| Read | |
| Read | |
|
Articles:
Email Security - Can't Live Without It!
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
Network Protocol Analyzers
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…

EventLog Analyzer
Event Log Monitoring System: Implementation, Chal…
An event log monitoring system, often referred to as an event log management, is a critical component to IT security & Management, that helps org…
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With Col…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addres…
Network Protocol Analyzers
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
Featured Subcategories:
WireShark Articles:
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…
Palo Alto Networks
How to Register a Palo Alto Firewall and Activate Supp…
This article explains how to register and activate your Palo Alto Firewall Appliance to obtain technical support, RMA hardware replacement, product update…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall PAN-OS…
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, saf…
Windows Servers
How to Install and Configure SNMP for Windows Server 2…
Simple Network Management Protocol (SNMP) is a UDP protocol that uses port 161 to monitor and collect detailed information on any network device supportin…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
In this article, we will cover more advanced DHCP features and topics such as server options, superscopes, multicast scopes, dynamic DNS, DHCP database ba…
Windows Servers
Windows 2016 Server Licensing Explained – Free Webinar
With Windows 2016 Server already making its way into data centers Windows 2016 Server Licensing is becoming a very hot topic. Windows 2016 Server is jam-p…
Windows Servers
Guide to Windows Server 2016 Hyper-V Hypervisor: New V…
One of Windows Server 2016 highlights is the newer Hyper-V server that not only extends the hypervisor’s features and capabilities but also introduces a n…
Popular Topics
Routing
Hybrid Routing Protocols - Advantages and Disadvantage…
Hybrid routing protocols are a combination of distance-vector and link-state routing protocols, and are used to provide a more efficient and scalabl…
SASE & SD-WAN Networks
SASE and VPNs: Reconsidering your Mobile Remote Access…
The Virtual Private Network (VPN) has become the go to security solution for keeping communications between networks and endpoints secure. After all, VPNs…
Routing
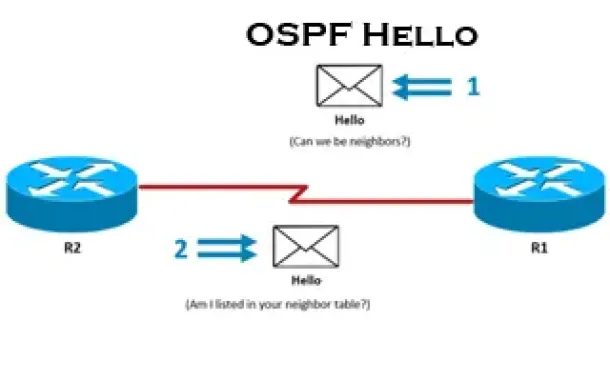
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Proce…
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll examine…
Windows Servers
How to Install Windows Server 2012 from USB Flash – IS…
Most would remember the days we had to have a CDROM or DVDROM in order to proceed with the installation of an operating system. Today, it is very common i…
Cisco Data Center (Nexus/UCS)
Complete Guide to Nexus Checkpoint & Rollback Feature…
The Cisco NX-OS checkpoint feature provides the capability to capture at any time a snapshot (backup) of the Cisco Nexus configuration befo…
Cisco Switches
VLAN Security Tips - Best Practices
This article focuses on VLAN Security and its implementation within the business network environment. We provide tips and Cisco CLI commands that will hel…
Cisco Firewalls
Cisco ASA 5500 Series Firewall Modules & Cards – Conte…
Cisco’s Adaptive Security Appliance (ASA) Firewalls are one of the most popular and proven security solutions in the industry. Since the introduction of t…
Cisco Routers
How To Secure Your Cisco Router Using Cisco AutoSecure…
In today’s complex network environments securing your network routers can be a daunting task, especially when there are so many CLI commands and parameter…



















