Event Log Monitoring System: Implementation, Challenges & Standards Compliance. Enhance Your Cybersecurity Posture
 An event log monitoring system, often referred to as an event log management, is a critical component to IT security & Management, that helps organizations strengthen their cybersecurity posture. It’s a sophisticated software solution designed to capture, analyze, and interpret a vast array of event logs generated by various components within an organization's IT infrastructure such as firewalls (Cisco ASA, Palo Alto etc), routers, switches, wireless controllers, Windows servers, Exchange server and more.
An event log monitoring system, often referred to as an event log management, is a critical component to IT security & Management, that helps organizations strengthen their cybersecurity posture. It’s a sophisticated software solution designed to capture, analyze, and interpret a vast array of event logs generated by various components within an organization's IT infrastructure such as firewalls (Cisco ASA, Palo Alto etc), routers, switches, wireless controllers, Windows servers, Exchange server and more.
These event logs can include data on user activities, system events, network traffic, and security incidents and more. By centralizing and scrutinizing these logs in real-time, event log monitoring systems play a pivotal role in enhancing an organization's security posture, enabling proactive threat detection, and facilitating compliance with regulatory requirements.
Key Topics:
- Event Log Categories
- Benefits of an Event Log Monitoring System
- Challenges When Implementing an Event Log Monitoring System
- Advantages of a Mandate-Compliant Event Log Management Tool
- How to Ensure Your Event Log Management System Stays Updated
- Open-source Log Analyzers vs. Commercial Log Analyzers
Event Log Categories
Event Log Monitoring Systems empowers organizations to identify and respond to potential security threats, operational issues, and compliance breaches promptly, making it an indispensable tool for maintaining the integrity and reliability of modern digital ecosystems.
All logs contain the following basic information:
- A timestamp.
- Details about the user or IP that performed the action.
- The action or type of event.
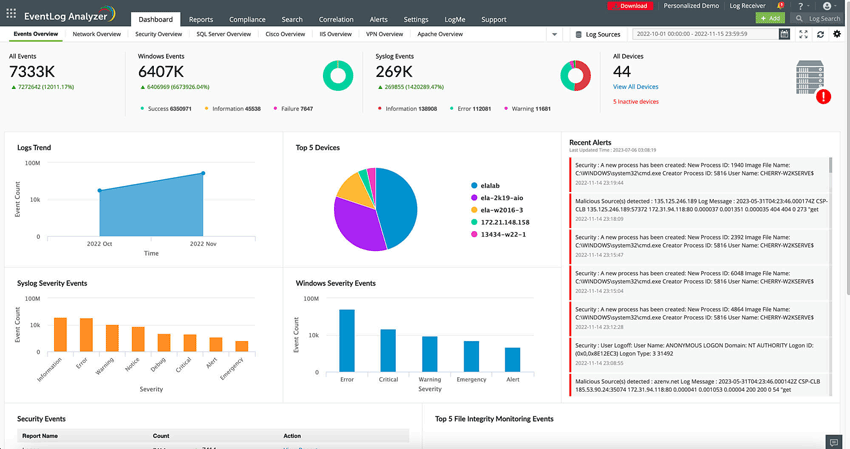 EventLog Analyzer (click to enlarge)
EventLog Analyzer (click to enlarge)
Logs are categorized based on the source generating them. They can be the following:
- Windows event logs: The logs of Microsoft Windows devices are known as events or event logs. They store information regarding the system, security, and the applications stored in the Windows OS. They can be viewed and analyzed using the built-in Event Viewer tool.
- Syslog messages: Syslog messages are generated by routers, switches, firewalls, and Linux or Unix systems. They contain details regarding the system's operations, like kernel messages, hardware events, and boot messages.
- Application logs: All applications, such as IIS web server applications or databases, generate application logs. Application logs maintain records of the events that occur within an application.
Benefits of an Event Log Monitoring System
 Though Windows devices have the built-in Event Viewer, it is used to analyze the logs generated by that specific system. For gaining visibility into what's happening in a network, it is essential to centralize the logs from various devices and then perform analysis. Central event log monitoring systems can help enterprises with this requirement.
Though Windows devices have the built-in Event Viewer, it is used to analyze the logs generated by that specific system. For gaining visibility into what's happening in a network, it is essential to centralize the logs from various devices and then perform analysis. Central event log monitoring systems can help enterprises with this requirement.
An event log monitoring system provides real-time visibility and an analysis of Windows event logs to identify potential security issues, detect anomalies, troubleshoot problems, and ensure the overall security and performance of all the relevant devices within the IT infrastructure.
1. Troubleshooting and problem resolution. Windows event logs capture information regarding Windows system events, errors, and warning messages. By analyzing these logs, IT teams can quickly identify and rectify system and security issues while understanding the source of any problem.
2. Performance optimization. Windows event logs offer visibility into system performance metrics, such as the resource utilization, response times, and error rates. By monitoring and analyzing these logs, organizations can measure and optimize the performance of their IT infrastructure, ensuring quicker response times.
3. Forensic analysis. Windows event logs serve as a valuable information repository for forensic inquiries. When facing a security incident or breach, an organization can analyze these logs to follow Windows events, monitor user actions, and establish a comprehensive view of the chronological event sequence.
For example, a log for event ID 4740 is generated when an account is locked out due to multiple failed login attempts. It includes information about the locked account and the source IP address. A log for event ID 5157 is generated when network packets are dropped or blocked by Windows Filtering Platform due to firewall rules or other security policies.
4. Compliance and auditing. Many regulations, frameworks, and industry standards require organizations to maintain detailed records of system events and activities. An event log monitoring system helps organizations meet compliance requirements by capturing and storing Windows event logs in a centralized, secure manner in accordance with the respective compliance mandates.
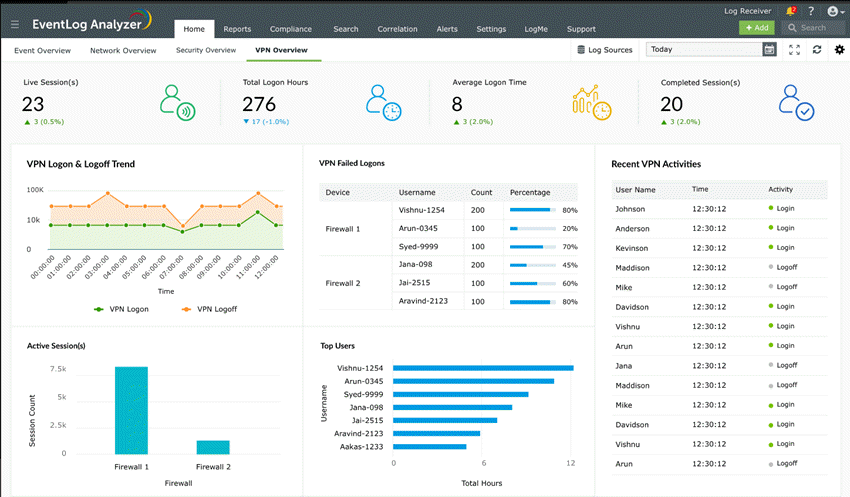 EventLog Analyzer reports on VPN users (click to enlarge)
EventLog Analyzer reports on VPN users (click to enlarge)
Challenges When Implementing an Event Log Monitoring System
Implementing an event log monitoring system can be highly beneficial for an organization, but it also comes with several challenges. Some of the common challenges organizations might face include:
-
Volume of Data: Log files can generate an enormous amount of data. Managing and storing this data can be a significant challenge, as it may require substantial storage resources.
-
Data Retention: Balancing the need for historical data with storage limitations can be tricky. Deciding how long to retain logs is crucial for compliance and investigation purposes.
-
Log Management and Analysis: Effectively managing and analyzing logs can be complex. Organizations need to invest in tools and personnel to ensure that logs are efficiently collected, stored, and analyzed.
-
Security and Privacy: Logs often contain sensitive information, and their storage and access must be carefully controlled to protect against unauthorized access or data breaches.
-
Log Integrity: Ensuring the integrity of log data is crucial. Any tampering or deletion of logs could undermine the system's credibility and security.
-
Log Format and Compatibility: Different systems generate logs in various formats, and integrating logs from diverse sources can be challenging. Standardizing log formats may be necessary.
-
Alert Fatigue: An overload of alerts generated by log monitoring systems can lead to alert fatigue, making it difficult for security personnel to prioritize and respond to real threats effectively.
-
Tuning and False Positives: Fine-tuning the monitoring system to reduce false positives without missing real threats can be a delicate balance to achieve.
-
Scalability: As an organization grows, the volume of logs can increase significantly. Ensuring the log monitoring system can scale to meet these demands is crucial.
-
Costs: The implementation and ongoing operation of a log monitoring system can be expensive, requiring investment in hardware, software, and skilled personnel.
-
Regulatory Compliance: Meeting specific industry or regional regulatory requirements can add complexity to log monitoring, as the system must capture and report on specific events to remain compliant.
-
Skill Gaps: Organizations may struggle to find or develop the necessary expertise to manage and operate the log monitoring system effectively.
- Achieving real-time monitoring and responses to events can be challenging due to the speed and complexity of modern cyberthreats. Organizations need to implement efficient response mechanisms.
To address these challenges, organizations should carefully plan their log monitoring strategy, invest in appropriate technology and training, and regularly review and update their approach to ensure the system remains effective and efficient.
Advantages of a Mandate-Compliant Event Log Management Tool
Event log management tools ensure that all the important records of events are collected. This is the first step in adhering to compliance mandates. Here are some ways in which a mandate-compliant event log management tool helps your network:
1. Many industry-specific regulations and standards, such as the PCI DSS or the GDPR, mandate the collection, retention, and protection of log data. An event log management system ensures that your organization complies with these mandates, thus preventing penalties. It also helps with internal and external audit processes.
2. If a security incident occurs, an event log manager helps in identifying the key details of the incident, which can provide insights into how it can be prevented in the future.
3. Having a log management system that is compliant with network security and cybersecurity standards facilitates integrations with SIEM tools, enhancing your event log software's capabilities.
4. When it comes to compliance assessments, having a comprehensive and well-organized log of all network events can significantly reduce the time and effort required for audits. Compliance auditors can efficiently access the necessary data, verify adherence to regulatory standards, and ascertain the network's security posture.
5. Finally, a manadate-compliant event log tool can generate detailed reports and summaries, which are invaluable in communicating an organization's compliance status to regulatory authorities or stakeholders, thereby ensuring a smoother and more efficient compliance management process.
How to Ensure Your Event Log Management System Stays Updated
By following the practices listed below, you can ensure that your event log management system remains updated, reliable, and capable of meeting your organization's evolving needs while minimizing the risks associated with outdated software:
- Ensure that all updates to your event log monitoring software are completely compatible with your system and its functions before applying them. Testing them in a simulated environment before going live with them helps you remove bugs and ensure better functioning.
- Schedule all updates and fixes in advance to make them easier to apply in a live environment.
- Ensure that your vendor provides frequent updates so you can detect new attack patterns, correlate logs and data, and do even more.
Open-source Log Analyzers vs. Commercial Log Analyzers
Open-source log analyzers are typically free of cost, making them effective solutions if you have budget constraints. However, while open-source log analyzers do perform the functions that are required of a log management system, commercial event log analyzers offer better vendor support and more advanced features, are more scalable, and can be integrated in different environments with ease.
Commercial event log management systems like ManageEngine EventLog Analyzer are usually preferred over open-source solutions. EventLog Analyzer helps you collect, filter, analyze, correlate, and archive log data, then conduct forensic analysis on it. EventLog Analyzer's advanced log filters combined with its correlation and analysis module ensure that all the important logs are collected and stored while eliminating noisy logs. Event log archiving allows you to store important logs for a predefined duration, while the forensic analysis feature lets you trace suspicious events and the sources of incidents or alerts.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!