Suggested Articles:
Network Protocol Analyzers
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…

ManageEngine Firewall Analyzer
Discover the Ultimate Firewall Management Tool: 7…
Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectively…
Network Protocol Analyzers
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
Featured Subcategories:
WireShark Articles:
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall PAN-OS…
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, saf…
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enforcemen…
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with the…
Windows Servers
How to Install and Configure SNMP for Windows Server 2…
Simple Network Management Protocol (SNMP) is a UDP protocol that uses port 161 to monitor and collect detailed information on any network device supportin…
Windows Servers
Windows 2016 Server Licensing Explained – Free Webinar
With Windows 2016 Server already making its way into data centers Windows 2016 Server Licensing is becoming a very hot topic. Windows 2016 Server is jam-p…
Windows Servers
Guide to Windows Server 2016 Hyper-V Hypervisor: New V…
One of Windows Server 2016 highlights is the newer Hyper-V server that not only extends the hypervisor’s features and capabilities but also introduces a n…
Windows Servers
How to Easily Change Network Card Profile / Network Lo…
Network Location Awareness (NLA) is a feature offered on Windows Server 2012 R2 and all Windows workstation editions from Windows 8.1 and above, including…
Popular Topics
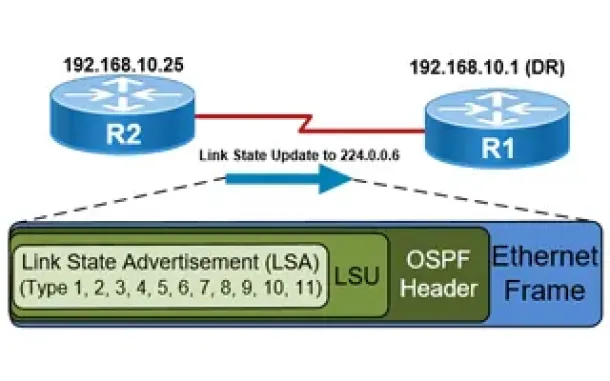
Routing
OSPF - Part 5: Analysis of OSPF Link State Update (LSU…
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router recei…
Network Fundamentals
Firewall Topologies
In this section we are going to talk about the different ways a firewall can be set up. Depending on your needs, you can have a very simple firewall setup…
SASE & SD-WAN Networks
Converged SASE Backbone – How Leading SASE Provider, C…
Global connectivity is top of mind for many IT teams at organizations of all sizes. We are currently in the middle of a dramatic shift in business and tec…
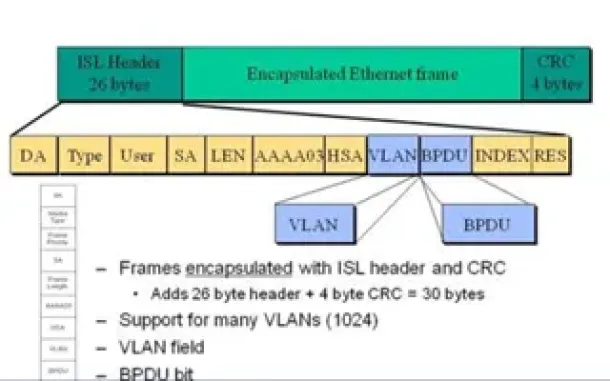
VLAN Networks
VLAN InterSwitch Link (ISL) Protocol Analysis
Deciding whether to use ISL or IEEE 802.1q to power your trunk links can be quite confusing if you cannot identify the advantages and disadvantages of eac…
Cisco Routers
How To Fix Cisco Configuration Professional (CCP) 'Jav…
Our previous article covered how to fix the Cisco Configuration Professional display/window problem where the CCP application is displayed in about one th…
Cisco Wireless
Understanding, Configuring & Tweaking Web-based Cisco…
Cisco Aironet Access Points, just like most Cisco devices, provide a web interface from which we are able to configure the device. It is often we are pres…
Cisco Firewalls
Converting Cisco Firepower from Platform mode to Appli…
This article explains how to configure a Cisco Firepower 2100 series device to operate in Appliance mode. We’ll show you how to switch from Platform mode…
Cisco CallManager-CCME
Cisco CallManager Express CME v8.8 & v9.0 GUI Web Inte…
Cisco's CallManager Express GUI interface is an important part of the CallManager Express product as it provides the ability to administer CME via a web b…



















