Suggested Articles:

OpManager - Network Monitoring & Management
Optimizing Cisco Router Performance: Best Practic…
Effective monitoring and management of Cisco routers and network devices are essential for ensuring a robust and efficient network infrastructure. In…

EventLog Analyzer
Event Log Monitoring System: Implementation, Chal…
An event log monitoring system, often referred to as an event log management, is a critical component to IT security & Management, that helps org…

ManageEngine Firewall Analyzer
Ensuring Compliance and Business Continuity in a…
In the wake of digital transformation, the work landscape as we know it has undergone a dynamic shift. People can now work from home, from the office…

ManageEngine Firewall Analyzer
7 Essential Firewall Management Strategies for Ma…
A firewall appliance is a fundamental pillar of network security, acting as the first line of defense against cyber threats. However, its strength…
Featured Subcategories:
WireShark Articles:
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall PAN-OS…
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, saf…

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on P…
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a P…
Windows Servers
Introduction to Windows DNS – The Importance of DNS fo…
The Domain Name System (DNS) is perhaps one of the most important services for Active Directory. DNS provides name resolution services for Active Director…
Windows Servers
Hyper-V Best Practices - Replica, Cluster, Backup Advi…
Hyper-V has proven to be a very cost effective solution for server consolidation. Evidence of this is also the fact that companies are beginning to move f…
Windows Servers
Windows 2012 Server Foundation, Essential, Standard &…
FREE Hyper-V & VMware Virtualization Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Windows Server 2012 Editions…
Windows Servers
Free Webinar & eBook on Microsoft Licensing for Virtua…
Microsoft Licensing for Virtual environments can become a very complicated topic, especially with all the misconceptions and false information out there…
Popular Topics
Network Protocol Analyzers
How to Perform TCP SYN Flood DoS Attack & Detect it wi…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and correct…
Virtualization & VM Backup
5 Most Critical Microsoft M365 Vulnerabilities Reveale…
Microsoft 365 is an incredibly powerful software suite for businesses, but it is becoming increasingly targeted by people trying to steal your data. The g…
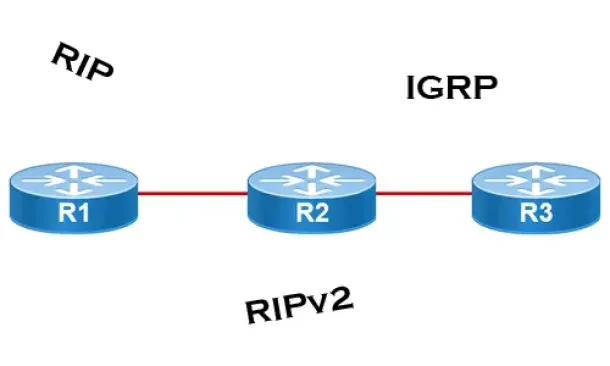
Routing
Distance Vector Routing Protocols
Distance Vector routing protocols use frequent broadcasts (255.255.255.255 or FF:FF:FF:FF) of their entire routing table every 30 sec. on all their interf…
SASE & SD-WAN Networks
WAN Optimization vs SD WAN Networks. Today’s Challenge…
Enterprises have been successfully running WAN optimization appliances at their many distributed sites for years. The devices have done a good job of help…
Cisco Switches
VLAN Security Tips - Best Practices
This article focuses on VLAN Security and its implementation within the business network environment. We provide tips and Cisco CLI commands that will hel…
Cisco Routers
Understanding MPLS IP VPNs, Security Attacks and VPN E…
What Are MPLS Networks?
Multi-Protocol Label Switching (MPLS) networks are the next-generation of networks designed to allow customers create end-to-end…
Cisco CallManager-CCME
IP Phone 7900 Series (7940, 7941, 7942, 7960, 7961, 79…
This article explains how to reset your Cisco 7940, 7941, 7942, 7960, 7961, 7962 & 7920 IP phone to factory defaults, and how to upgrade its firmware…
Cisco Routers
Cisco Router Basic ISDN Configuration
Configuration of ISDN interfaces on Cisco routers are usually considered a straight-forward process, however there are some details which can cause your I…



















