Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
|
Articles:
Website History
| Read |
|
Articles:
Site Awards
| Read |
|
Articles:
Meet The Firewall.cx Team!
| Read |
Suggested Articles:

ManageEngine Firewall Analyzer
Master Your Firewall: 6 Expert-Backed Steps to Bo…
In today’s evolving threat landscape, firewall audits are more than just a best practice—they're a critical line of defense. Regular audits ensure yo…

ManageEngine Firewall Analyzer
Challenges & Solutions to Managing Firewall Rules…
In today's interconnected digital landscape, where businesses rely heavily on networked systems and the internet for their operations, the importance…
EventLog Analyzer
Detecting Windows Server Security Threats with Ad…
Windows Servers stand as prime targets for hackers and malicious actors due to their widespread usage and historical vulnerabilities. These systems o…
Network Protocol Analyzers
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
Featured Subcategories:
WireShark Articles:
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall PAN-OS…
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, saf…
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtual…
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fire…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
Windows Servers
Active Directory Tombstone Lifetime Modification
Tombstone is a container object that contains the deleted objects from Active Directory. Actually when an object is deleted from Active Directory, it is n…
Windows Servers
How to Install Windows 2012 Hyper-V via Server Manager…
Our previous article covered the basic concepts of Virtualization and Windows Server 2012 Hyper-V. This article takes a closer look at Microsoft’s H…
Windows Servers
How to Install and Configure Windows 2012 DNS Server R…
Our previous article covered introduction to the Domain Name System (DNS) and explained the importance of the DNS Server role within the network infrastru…
Windows Servers
Creating Windows Users and Groups with Windows 2003
In a Windows server environment, it is very important that only authenticated users are allowed to log in for security reasons. To fulfill this requiremen…
Popular Topics
SASE & SD-WAN Networks
Complete Guide to SD-WAN. Technology Benefits, SD-WAN…
SD-WAN is the answer for enterprises and organizations seeking to consolidate network functions and services while at the same time simplify their WAN inf…
SASE & SD-WAN Networks
Understanding Secure Access Service Edge (SASE) and ho…
Software Defined Wide Area Networking (SD-WAN) is changing the way that businesses connect to the cloud. With SD-WAN, organizations can move away from clo…
Windows Servers
Creating a Virtual Machine in Windows Hyper-V. Configu…
Our previous articles covered basic concepts of Virtualization along with the installation and monitoring of Windows 2012 Hyper-V. This article takes the…
Windows Servers
How to Easily Change Network Card Profile / Network Lo…
Network Location Awareness (NLA) is a feature offered on Windows Server 2012 R2 and all Windows workstation editions from Windows 8.1 and above, including…
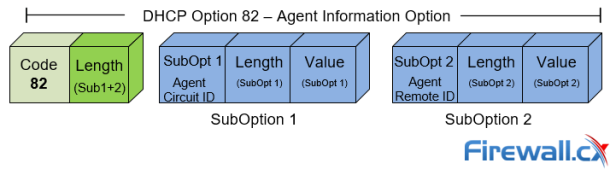
Cisco Switches
DHCP Option 82 Message Format, Analysis. DHCP Snooping…
This article provides in-depth analysis of DHCP Option 82 (DHCP Relay Agent) which is one of the +180 DHCP Options available to the DHCP protocol and used…
Cisco Routers
Cisco VPN Client Configuration - Setup for IOS Router
Remote VPN access is an extremely popular service amongst Cisco routers and ASA Firewalls. The flexibility of having remote access to our corporate networ…
Cisco Switches
Spanning Tree BPDU Guard and Errdisable Interface Auto…
Running Spanning Tree Protocol (STP) in a large network environment can be a challenging task especially when features/enhancements such as BPDU Filter an…
Cisco CallManager-CCME
How To Stop CallManager (CUCM) 7, 8, 9, 10.5 with MGCP…
Cisco Unified CallManager (CUCM) and its Voice Gateway relies on the telecommunication provider (telco) to send the correct call details for every incomin…



















