Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
Are Cloud-Based Services Overhyped?
| Read |
|
Articles:
What if it Rains in the Cloud?
| Read |
| Read | |
| Read | |
|
Articles:
Email Security - Can't Live Without It!
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…

OpManager - Network Monitoring & Management
AIOps for Modern IT Operations: Automating Monito…
The days of relying solely on static monitoring dashboards and manual firefighting are long gone. Today’s environments demand automation-first operat…

ManageEngine Firewall Analyzer
Master Your Firewall: 6 Expert-Backed Steps to Bo…
In today’s evolving threat landscape, firewall audits are more than just a best practice—they're a critical line of defense. Regular audits ensure yo…
OpManager - Network Monitoring & Management
Ensuring Enterprise Network Readiness for Mobile…
Demands for Enterprise networks to properly support mobile users is on a continuous rise making it more than ever necessary for IT departments to pro…
Featured Subcategories:
WireShark Articles:
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enforcemen…
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with the…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based Po…
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient wa…
Windows Servers
The Importance of a Hyper-V & VMware Server Backup Too…
Using Hyper-V Server virtualization technology, you can virtualize your physical environment to reduce the cost of physical hardware. As part of IT best p…
Windows Servers
Simple Guide on Installing & Configuring a Windows 201…
A Windows Active Directory Certification Authority server (AD CA), also known as a Certificate Authority, is an essential service to every organization’s…
Windows Servers
Understanding, Creating, Configuring & Applying Window…
This article explains what Group Policies are and shows how to configure Windows Server 2012 Active Directory Group Policies. Our next article will cover…
Windows Servers
Windows Server Group Policy Link Enforcement, Inherita…
Our previous article explained what Group Policy Objects (GPO) are and showed how group policies can be configured to help control computers and users wit…
Popular Topics
Network Protocol Analyzers
How to Detect SYN Flood Attacks with Capsa Network Pro…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and inspect…
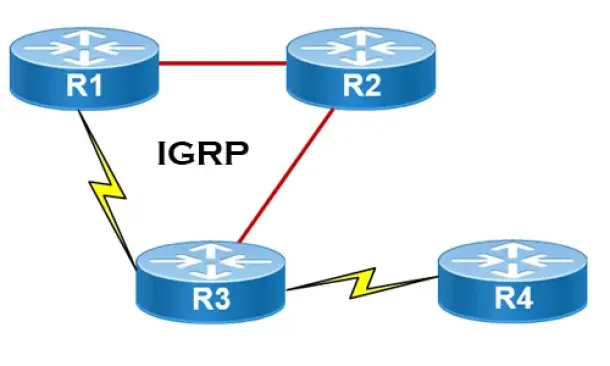
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informati…
Network Protocol Analyzers
Detect Brute-Force Attacks with nChronos Network Secur…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/database…
Windows Servers
Configuring Domain Group Policy for Windows 2003
Windows 2003 Group Policies allow the administrators to manage a group of people accessing a resource efficiently. The group policies can be used to contr…
Cisco Routers
Disabling Cisco Router Password Recovery Service
Most Cisco engineers are aware of the classic Password-Recovery service Cisco equipment have. If the device's credentials are lost, then performing the Pa…
Cisco CallManager-CCME
Connecting & Configuring SPA8000 with UC500, 520, 540…
When it comes to connecting multiple analog phones to VoIP systems like Cisco’s Unified Communication Manager Express (CallManager Express) or UC500 serie…
Cisco CallManager-CCME
How To Stop CallManager (CUCM) 7, 8, 9, 10.5 with MGCP…
Cisco Unified CallManager (CUCM) and its Voice Gateway relies on the telecommunication provider (telco) to send the correct call details for every incomin…
Cisco CallManager-CCME
Secure CallManager Express Communications - Encrypted…
In this article we discuss about the security and encryption of Cisco Unified Communications Manager Express (CUCME) which is an integral part of Cisco UC…



















