Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
Are Cloud-Based Services Overhyped?
| Read |
|
Articles:
What if it Rains in the Cloud?
| Read |
| Read | |
| Read | |
|
Articles:
Email Security - Can't Live Without It!
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
EventLog Analyzer
Detecting Windows Server Security Threats with Ad…
Windows Servers stand as prime targets for hackers and malicious actors due to their widespread usage and historical vulnerabilities. These systems o…

OpManager - Network Monitoring & Management
Elevate your network management: Maximizing effic…
As technology evolves, so do our networks. Today's sprawling network infrastructures are intricate ecosystems, demanding more from IT teams than ever…

EventLog Analyzer
Event Log Monitoring System: Implementation, Chal…
An event log monitoring system, often referred to as an event log management, is a critical component to IT security & Management, that helps org…
Network Protocol Analyzers
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
Featured Subcategories:
WireShark Articles:
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtual…
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fire…
Palo Alto Networks
The Benefits of Palo Alto Networks Firewall Single Pas…
What makes Palo Alto Networks Next-Generation Firewall (NGFW) so different from its competitors is its Platform, Process and Architecture. Palo Alto Netwo…

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…
Windows Servers
Windows 2012 Server Foundation, Essential, Standard &…
FREE Hyper-V & VMware Virtualization Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Windows Server 2012 Editions…
Windows Servers
Windows Server 2016 Licensing Made Easy – Understand Y…
This article describes the new Windows Server 2016 Licensing model (per-core licensing) Microsoft has implemented for its new server-based operating syste…
Windows Servers
How to Install Windows 2012 Hyper-V via Server Manager…
Our previous article covered the basic concepts of Virtualization and Windows Server 2012 Hyper-V. This article takes a closer look at Microsoft’s H…
Windows Servers
Hyper-V Best Practices - Replica, Cluster, Backup Advi…
Hyper-V has proven to be a very cost effective solution for server consolidation. Evidence of this is also the fact that companies are beginning to move f…
Popular Topics
Windows Servers
Windows 2003 DHCP Server Installation & Configuration
DHCP (Dynamic Host Configuration Protocol) is a protocol that allows clients on a network to request network configuration settings from a server running…

Network Fundamentals
Network Unicast - Its role and Importance
Unicast is a communication method used in computer networking where data is sent from a single sender to a specific destination device. In this meth…
SASE & SD-WAN Networks
Converged SASE Backbone – How Leading SASE Provider, C…
Global connectivity is top of mind for many IT teams at organizations of all sizes. We are currently in the middle of a dramatic shift in business and tec…
Virtualization & VM Backup
FREE Webinar - Fast Track your IT Career with VMware C…
Everyone who attends the webinar has a chance of winning a VMware VCP course (VMware Install, Config, Manage) worth $4,500!
Climbing the career ladder in…
Cisco Services & Technologies
WEB SSL VPN - The Next Wave Of Secure VPN Services
Fifteen years ago Virtual Private Networks (VPN) access was a fairly new concept to most businesses. While large corporations already had a good head-star…
Cisco Routers
Installing Security Device Manager (SDM) on a Cisco Ro…
For years now, Cisco has been developing its Security Device Manager (SDM) software. This web-based software is designed to help the less experienced user…
Cisco Switches
Download The Complete Cisco Catalyst Switching Portfol…
The Cisco Catalyst Switching Portfolio is perhaps one of the most useful Cisco PDF files, containing all Catalyst series products. The portfolio co…
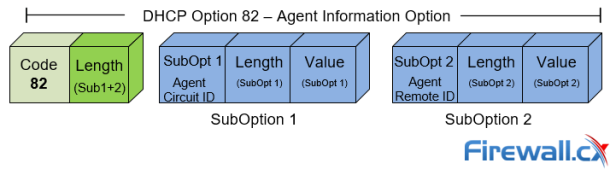
Cisco Switches
DHCP Option 82 Message Format, Analysis. DHCP Snooping…
This article provides in-depth analysis of DHCP Option 82 (DHCP Relay Agent) which is one of the +180 DHCP Options available to the DHCP protocol and used…



















