Suggested Articles:
Cisco Routers
How To Fix Cisco Configuration Professional (CCP)…
Our previous article covered how to fix the Cisco Configuration Professional display/window problem where the CCP application is displayed in about o…
Cisco CallManager-CCME
Secure CallManager Express Communications - Encry…
In this article we discuss about the security and encryption of Cisco Unified Communications Manager Express (CUCME) which is an integral part of Cis…
Cisco Routers
How To Configure Dynamic DNS Server On A Cisco Ro…
Hosting your own webserver or email server would normaly require a static IP address from your ISP. This ensures that your services are always reacha…
Cisco Routers
How To Configure ISDN Internet Dialup On A Cisco…
Some time ago, when broadband and ADSL wasn't available, analog and digital (ISDN) modems were the only way to connect to the Internet. Even though t…
Featured Subcategories:
Data Center Articles:

Join Australia’s First Official Cisco Data Center…
It’s a reality – Australia now has its own Official Cisco Data Center User Group (DCUG) and it’s growing fast! Originally inspired by Cisco Champions…
Complete Guide to Nexus Checkpoint & Rollback Fea…
The Cisco NX-OS checkpoint feature provides the capability to capture at any time a snapshot (backup) of the Cisco Nexus configuration…
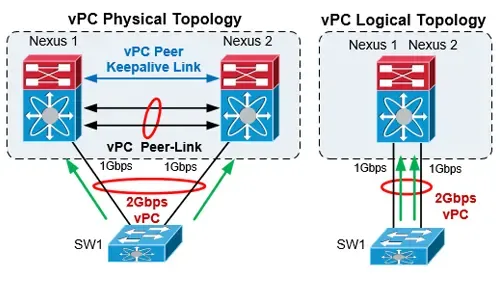
The Complete Cisco Nexus vPC Guide. Features & Ad…
Cisco virtual Port Channel (vPC) is a virtualization technology, launched in 2009, which allows links that are physically connected to two different…

NEXUS NX-OS: Useful Commands, CLI Scripting, Hint…
Whether you’re new to Cisco Nexus switches or have been working with them for years this article will show how to get around the Nexus NX-OS usi…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Cisco Switches
Cisco Catalyst 4500 Series Zero-Downtime IOS Upgrade P…
The Supervisor Engine is the heart of the Cisco Catalyst 4500 and 6500 series switches. It is the equivalent of an engine in a car. Every packet that ente…
Cisco Switches
End-of-Sale and End-of-Life Announcement for the Cisco…
Cisco announces the end-of-sale and end-of-life dates for the Cisco Catalyst 3750G, 3560G, 3750-E, and 3560-E Series Switches. The last day to order the a…
Cisco Switches
How to Disable or Enable the Password Recovery Procedu…
Our previous article shows how to perform a password recovery on the Cisco Catalyst switches. This article will now explain how to disable or enable the C…
Cisco Switches
Forcing A Cisco Catalyst Switch To Use 3rd Party SFP M…
Many companies are seeking for Cisco SFP alternatives to help cut down the costs on these expensive modules.
A frequent customer problem with Cisco's new…
Cisco Firewalls
Cisco ASA Firepower Threat Defense (FTD): Download and…
One Appliance – One Image is what Cisco is targeting for its Next Generation Firewalls. With this vision, Cisco has created a unified software image named…
Cisco Firewalls
Converting Cisco Firepower from Platform mode to Appli…
This article explains how to configure a Cisco Firepower 2100 series device to operate in Appliance mode. We’ll show you how to switch from Platform mode…
Cisco Firewalls
Cisco ASA 5500-X Series Firewall with IPS, ASA CX & Fi…
The Cisco ASA Firewall 5500-X series has evolved from the previous ASA 5500 Firewall series, designed to protect mission critical corporate networks and d…
Cisco Firewalls
Cisco ASA 5500 Series Firewall Modules & Cards – Conte…
Cisco’s Adaptive Security Appliance (ASA) Firewalls are one of the most popular and proven security solutions in the industry. Since the introduction of t…
Popular Topics

Virtualization & VM Backup
Ultimate Guide: Install Windows 11 on VMware ESXi – Ea…
In this article, we’ll show you how to setup or install Microsoft Windows 11 on VMware’s ESXi servers and bypass the Trusted Platform Module version 2.0 (…
SASE & SD-WAN Networks
Key Features of a True Cloud-Native SASE Service. Sett…
Secure Access Service Edge (SASE) is an architecture widely regarded as the future of enterprise networking and security. In previous articles we talked a…
Virtualization & VM Backup
The Backup Bible. A Free Complete Guide to Disaster Re…
The Free Backup Bible Complete Edition written by backup expert and Microsoft MVP Eric Siron, is comprised of 200+ pages of actionable content divided int…
Virtualization & VM Backup
How to Enable or Disable SSH on VMware ESXi via Web GU…
SSH access to VMware’s ESXi server is by disabled by default however there are many reasons where SSH might be required. VMware and System administrators…



















