Suggested Articles:
Network Protocol Analyzers
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
OpManager - Network Monitoring & Management
Network Management Systems Help Businesses Accura…
Accurately monitoring your organization’s business application performance, service provider SLA breaches, network infrastructure traffic, bandwidth…
Network Protocol Analyzers
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
Featured Subcategories:
WireShark Articles:
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fire…
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emerging…

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based Po…
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient wa…
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall PAN-OS…
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, saf…
Windows Servers
How to Enable ‘Web Server’ Certificate Template Option…
In this article we will show you how to enable the ‘Web Server’ certificate template option on a Windows Certification Authority (Windows CA) Server. …
Windows Servers
The Importance of a Comprehensive Backup Strategy for…
People and companies usually adopt a backup strategy suited to the needs of their working environment. As such, there is no absolute right or wrong method…
Windows Servers
Free Webinar: Troubleshooting & Fixing Microsoft Hyper…
Users working with Hyper-V Virtualization would be interested to know that Altaro is hosting a free webinar on the 25th of February 2016 at 4pm CET / 10am…
Windows Servers
Windows 2003 DNS Server Installation & Configuration
DNS is used for translating host names to IP addresses and the reverse, for both private and public networks (i.e.: the Internet). DNS does this by using…
Popular Topics

Network Fundamentals
Network Switches & Bridges
Network Switches are the evolution of Hubs and Repeaters, and enable the creation of networks by connecting multiple devices together. They are critical c…
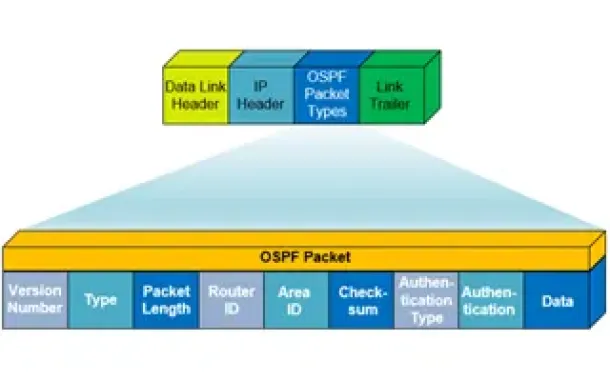
Routing
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
Network Fundamentals
Firewall Topologies
In this section we are going to talk about the different ways a firewall can be set up. Depending on your needs, you can have a very simple firewall setup…
Windows Servers
Understanding, Creating, Configuring & Applying Window…
This article explains what Group Policies are and shows how to configure Windows Server 2012 Active Directory Group Policies. Our next article will cover…
Cisco Routers
How To Configure Router On A Stick - 802.1q Trunk To C…
Router-on-a-stick is a term frequently used to describe a setup up that consists of a router and switch connected using one Ethernet link configured as an…
Cisco Routers
Cisco Router Password Recovery
Password recovery is a fairly frequently used procedure for administrators and engineers. Even though we usually stack our passwords in some word, excel o…
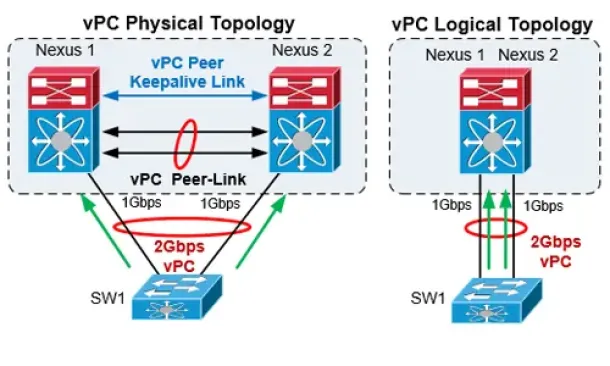
Cisco Data Center (Nexus/UCS)
The Complete Cisco Nexus vPC Guide. Features & Advanta…
Cisco virtual Port Channel (vPC) is a virtualization technology, launched in 2009, which allows links that are physically connected to two different Cisco…
Cisco CallManager-CCME
Cisco Small Business SPA500 IP Phone Series Administra…
Firewall.cx readers can now access and freely download the Cisco Small Business Administration Guide for Cisco SPA500 series IP phones. The Adminis…



















