Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
|
Articles:
IP Subnet Calculator
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
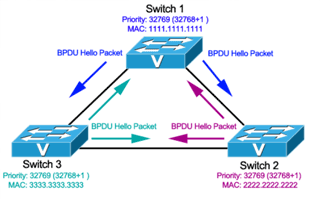
Spanning Tree Protocol (STP)
Spanning Tree Protocol – Part 3: Bridge ID, Prior…
In this article we will examine the Spanning Tree Bridge ID structure, explain why it has increments of 4096, how VLAN information is embedded (for P…
Ethernet Protocol, CSMA/CD, Collisions
Early Ethernet Collisions
In this example, we will refer to an imaginary Ethernet network consisting of Stations A and B and any number of other stations. The status of the ne…
Network Address Translation - NAT
The Network Address Translation Table
After that simple and informative introduction to the NAT concept, it's time to find out more about how it works and this is where the NAT table come…

Network Fundamentals
Next-Gen Firewalls & Topologies. Designing & Buil…
Next-generation firewalls (NGFWs) and DMZ zones are two critical components of network security that work hand in hand to protect an organization's n…
Featured Subcategories:
Netflow Articles:
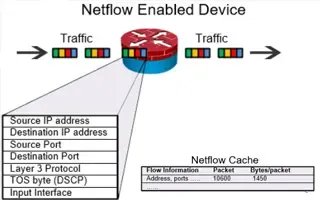
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
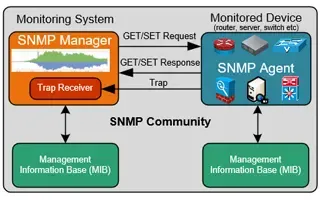
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
VLAN Networks
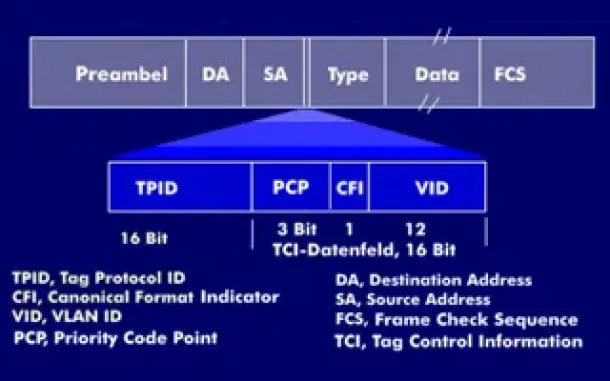
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…

VLAN Networks
Comparing Traditional Flat & VLAN Networks
Designing and building a network is not a simple job. VLANs are no exception to this rule, in fact they require a more sophisticated approach because of t…
VLAN Networks
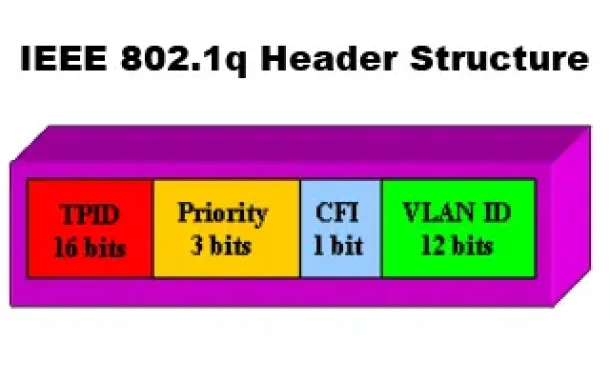
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Stati…
Routing
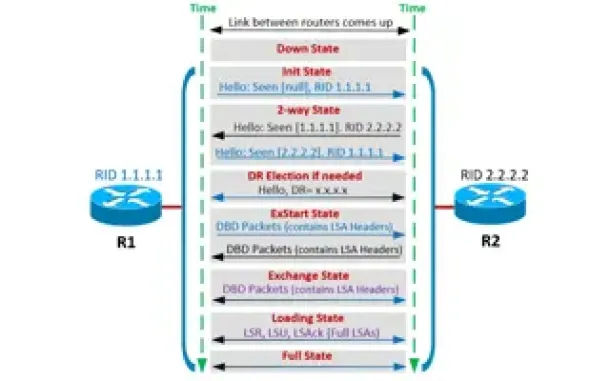
OSPF - Part 4: OSPF Neighbor States – OSPF Neighbor Fo…
This is the third article of our OSPF series which analyzes the different OSPF States routers go through during the OSPF discovery and neighbor forming pr…
Routing
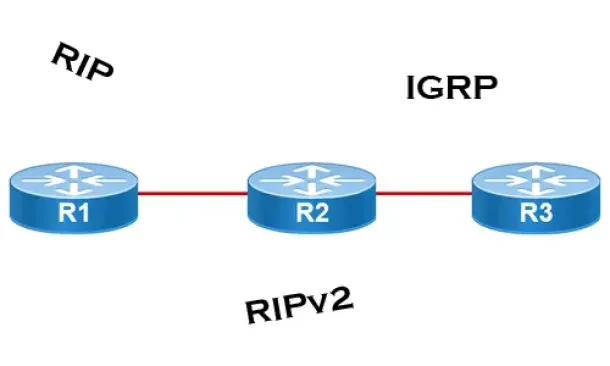
Distance Vector Routing Protocols
Distance Vector routing protocols use frequent broadcasts (255.255.255.255 or FF:FF:FF:FF) of their entire routing table every 30 sec. on all their interf…
Routing
Hybrid Routing Protocols - Advantages and Disadvantage…
Hybrid routing protocols are a combination of distance-vector and link-state routing protocols, and are used to provide a more efficient and scalabl…
Routing
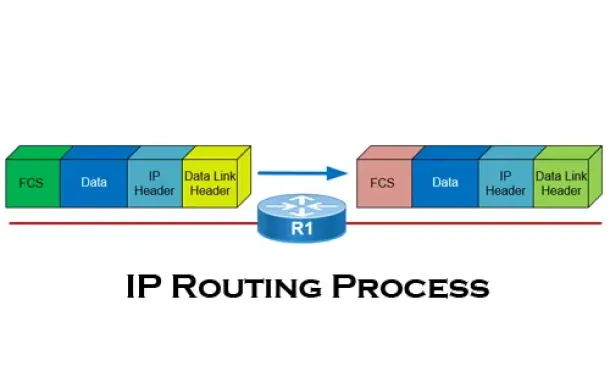
The IP Routing Process - Step-by-Step Analysis
We are going to analyse what happens when routing occurs on a network (IP routing process). When I was new to the networking area, I thought that all you…
Windows Servers
Creating a Virtual Machine in Windows Hyper-V. Configu…
Our previous articles covered basic concepts of Virtualization along with the installation and monitoring of Windows 2012 Hyper-V. This article takes the…
Windows Servers
Creating Windows Users and Groups with Windows 2003
In a Windows server environment, it is very important that only authenticated users are allowed to log in for security reasons. To fulfill this requiremen…
Palo Alto Networks
How to Register a Palo Alto Firewall and Activate Supp…
This article explains how to register and activate your Palo Alto Firewall Appliance to obtain technical support, RMA hardware replacement, product update…
Cisco Firewalls
Cisco ASA Firepower Threat Defense (FTD): Download and…
One Appliance – One Image is what Cisco is targeting for its Next Generation Firewalls. With this vision, Cisco has created a unified software image named…



















