Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
Linux File & Folder Permissions
| Read |
|
Articles:
Advanced Linux Commands
| Read |
|
Articles:
Installing Software On Linux
| Read |
|
Articles:
The Linux Command Line
| Read |
|
Articles:
The Linux File System
| Read |
|
Articles:
Why Use Linux?
| Read |
MS Server Articles:
Windows Servers
Installation and Configuration of Fine-Grained Pa…
Microsoft introduced Fine-Grained Password Policy for the first time in Windows Server 2008 and the policy has been part of every Windows Server sinc…
Windows Servers
Simple Guide on Installing & Configuring a Window…
A Windows Active Directory Certification Authority server (AD CA), also known as a Certificate Authority, is an essential service to every organizati…
Windows Servers
New Upcoming Features in Hyper-V vNext - Free Tr…
With the release of Hyper-V vNext just around the corner, Altaro has organized a Free webinar that will take you right into the new Hyper-V vNext rel…
Windows Servers
Active Directory Tombstone Lifetime Modification
Tombstone is a container object that contains the deleted objects from Active Directory. Actually when an object is deleted from Active Directory, it…
Featured Subcategories:
Virtualization & VM Backup Articles:

8 Critical Features to Have in a VM Backup Soluti…
Businesses that rely on virtual machines for their day-to-day operations should think twice about securing their infrastructure. Modern use of virtua…
World Backup Day with Free Amazon Voucher and Pri…
Celebrate World Backup Day and WIN with Altaro!
We all remember how grateful we were to have backup software when facing so many data loss mishaps…
How to Fix VMware ESXi Virtual Machine 'Invalid S…
In this article, we'll show you how to deal with VMs which are reported to have an Invalid Status as shown in the screenshot below. This is a co…
Understanding Deduplication. Complete Guide to De…
When considering your VM backup solution, key features such as deduplication are incredibly important. This is not simply from a cost perspective but…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Linux - Unix
Linux BIND DNS - Part 2: Configuring db.domain Zone D…
It's time to start creating our zone files. We'll follow the standard format, which is given in the DNS RFCs, in order to keep everything neat and less co…
Linux - Unix
Installing & Configuring Linux Webmin - Linux Web-Base…
For many engineers and administrators, maintaining a Linux system can be a daunting task, especially if there’s limited time or experience. Wo…
Linux - Unix
Updating Your Linux Server - How to Update Linux Works…
Like any other software, an operating system needs to be updated. Updates are required not only because of the new hardware coming into the market, but al…
Linux - Unix
The Linux File System
A file system is nothing more than the way the computer stores and retrieves all your files. These files include your documents, programs, help files, gam…
Popular Topics
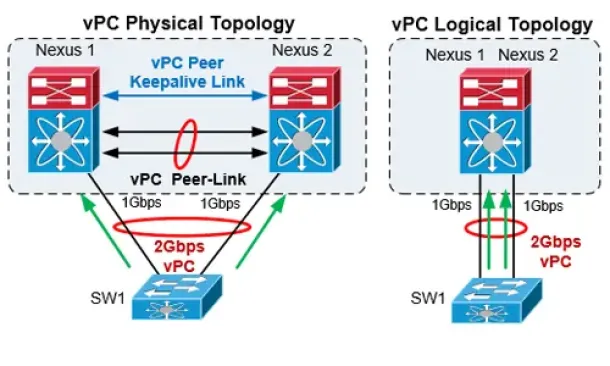
Cisco Data Center (Nexus/UCS)
The Complete Cisco Nexus vPC Guide. Features & Advanta…
Cisco virtual Port Channel (vPC) is a virtualization technology, launched in 2009, which allows links that are physically connected to two different Cisco…
Windows Workstations (XP, 7, 8, 10, 11)
Configuring Windows 7 To Provide Secure Wireless Acces…
Not many people are aware that Windows 7 has built-in capabilities that allow it to be transformed into a perfectly working access point so that wireless…
Cisco Routers
How To Fix Cisco Configuration Professional (CCP) Disp…
Cisco Configuration Professional (CCP) is Cisco’s latest GUI administration tool used to administer Cisco routers. CCP is basically the next step up from…
Cisco Routers
Configuring Cisco SSL VPN AnyConnect (WebVPN) on Cisco…
Our Web SSL VPN article written back in 2011 introduced this new wave of VPN services. This article extends the topic by covering the installation a…


















