All-in-one protection for Microsoft 365
All-in-one protection for Microsoft 365


OpManager: Network & DC Monitoring
Monitor & Manage Network, Datacenters, endpoints & more.
Latest Articles
Master Your Firewall: 6 Expert-Backed Steps to Boost Security, Performance, and Compliance
 In today’s evolving threat landscape, firewall audits are more than just a best practice—they're a critical line of defense. Regular audits ensure your firewall configurations are aligned with organizational security policies, eliminate inefficiencies, and reduce exposure to cyber risks. Just as importantly, they help organizations maintain compliance with regulatory standards such as PCI DSS, HIPAA, SOX, and GDPR, avoiding costly penalties and reputational damage. Beyond compliance, effective firewall audits offer operational clarity and control, giving IT and security teams complete visibility into traffic flows and rule configurations.
In today’s evolving threat landscape, firewall audits are more than just a best practice—they're a critical line of defense. Regular audits ensure your firewall configurations are aligned with organizational security policies, eliminate inefficiencies, and reduce exposure to cyber risks. Just as importantly, they help organizations maintain compliance with regulatory standards such as PCI DSS, HIPAA, SOX, and GDPR, avoiding costly penalties and reputational damage. Beyond compliance, effective firewall audits offer operational clarity and control, giving IT and security teams complete visibility into traffic flows and rule configurations.
A key part of this process lies in maintaining a solid network security policy, which defines who can access your network, what actions are permitted, and how traffic is managed across your infrastructure. However, simply defining rules isn’t enough. As networks scale, applications evolve, and new threats emerge, these rules can become outdated, redundant, or poorly configured. Without routine audits, rule sets often bloat—clogging performance, creating security gaps, and complicating compliance efforts.
To help you stay ahead, this article outlines six essential steps for performing a thorough firewall rule audit—from documentation and identifying redundancies, to reviewing rule order, verifying policy compliance, conducting log analysis, and implementing revisions.
We’ll see how tools like Firewall Analyzer can help simplify and automate the entire firewall audit process. From offering deep visibility into your rule base to identifying unused or risky configurations, it delivers the insights you need to clean up and optimize your firewall policies. By highlighting compliance issues, streamlining rule management, and supporting detailed reporting, Firewall Analyzer empowers your team to maintain a security posture that is both robust and audit-ready—all while reducing manual effort and minimizing the risk of misconfigurations.
Key Topics:
- Why do you Need Firewall Rule Audits?
- Enhanced Performance
- Improved Security
- Simplified Compliance
- Operation Clarity and Control
- Future-Readiness
- Audit Firewall Rules: A Step-by-Step Guide
- Begin with Documentation
- Identify Redundancies and Unused Rules
- Review Rule Order
- Verify Compliance with Policies
- Log Analysis
- Revisions and Summary
- Simplify Firewall Rule Audits with Firewall Analyzer
- Automated Rule Management
- Comprehensive Rule Visibility
- Smart Optimization Recommendations
- Pre-Change Impact Analysis
- Rule Cleanup
- Built-In Compliance Assurance
- Firewall Rule Audit Checklist
- Pre-Audit Preparation
- Rule Base Review
- Optimization & Cleanup
- Change Management
- Compliance & Reporting
- Building a Strong Firewall Environment: Efficiency, Security & Compliance
- Summary
Why Do You Need Firewall Rule Audits?
 A well-maintained and optimized firewall rule base is not just a best practice—it’s a necessity for maintaining a secure, high-performing, and compliant network.
A well-maintained and optimized firewall rule base is not just a best practice—it’s a necessity for maintaining a secure, high-performing, and compliant network.
Here’s why regular firewall rule audits should be a cornerstone of your network security strategy:
- Enhanced Performance: Firewalls process every incoming and outgoing packet against the rules configured. A bloated or disorganized rule base can slow down this process, leading to latency and system strain. Regular audits help eliminate redundant or obsolete rules, streamlining traffic flow and improving overall firewall efficiency.
- Improved Security: As your network grows, so does the risk of misconfigured or outdated firewall rules going unnoticed. These rules can become blind spots—potentially allowing unauthorized access or leaving the network vulnerable to attacks. By identifying and removing overly permissive, duplicate, or unused rules, audits help close these security gaps and reinforce your network defenses.
- Simplified Compliance: Regulatory standards like PCI DSS, HIPAA, SOX, and GDPR require organizations to maintain well-documented and effective security controls. A clean and auditable rule base makes it significantly easier to demonstrate compliance, pass security assessments, and respond to audits without last-minute scrambles.
- Operational Clarity and Control: Firewall rule audits bring transparency to rule sets, helping network administrators better understand rule logic, dependencies, and potential conflicts. This clarity is essential for effective policy management and quicker troubleshooting.
- Future-Readiness: Regular rule audits prepare your infrastructure for scaling, cloud migrations, or network restructuring by ensuring your security policies remain aligned with business goals and technical requirements.
In short, firewall rule audits are vital for maintaining a secure, efficient, and resilient network—today and into the future.
Grab your free download now to see how Firewall Analyzer streamlines your firewall rule audit process, effectively detects and resolves security vulnerabilities plus compliance concerns.
Audit Firewall Rules : A Step-by-Step Guide
Optimizing Cisco Router Performance: Best Practices for Effective Monitoring & Network Management
 Effective monitoring and management of Cisco routers and network devices are essential for ensuring a robust and efficient network infrastructure. In this article, we explore the key features and best practices for effectively monitoring and managing Cisco routers and other network devices in real-time. By incorporating these strategies into your IT management plan, you can enhance efficiency, boost performance, and ensure the smooth operation of your entire network infrastructure.
Effective monitoring and management of Cisco routers and network devices are essential for ensuring a robust and efficient network infrastructure. In this article, we explore the key features and best practices for effectively monitoring and managing Cisco routers and other network devices in real-time. By incorporating these strategies into your IT management plan, you can enhance efficiency, boost performance, and ensure the smooth operation of your entire network infrastructure.
Key Topics
- In-depth Real-time Monitoring your Network Device Performance
- Real-time Monitoring Hardware Metrics
- Analyze Network Traffic to Understand Usage Patterns
- Effectively Manager Configuration Changes
- Visualize Network Paths and Pinpoint Network Issues
- Monitor and Manage Your Routers and other Devices with a Comprehensive Management Solution
Routers are the backbone of every network, playing a crucial role in directing traffic and ensuring that data reaches its destination efficiently. They connect various parts of a network and optimize performance by selecting the best possible route for every data packet. With a significant 34.7% market share, Cisco stands out as the leader in the router market, making its devices a common and vital part of modern network infrastructure.
Despite their importance, managing these routers can be challenging. Traditionally, network administrators must connect to each router manually using console cables and retrieve data via Secure Shell (SSH) or Telnet. This process is not only time-consuming but also prone to errors, especially in large enterprise environments where hundreds of devices require regular monitoring and maintenance.
Modern IT operations management software offers an effective solution to these challenges. By automating monitoring and management tasks, such software provides a single-pane view of the entire infrastructure, simplifying operations and reducing manual workloads. This automated approach enables organizations to quickly identify issues, streamline routine tasks, and maintain optimal network performance.
Take a peak at the market's leading IT infrastructure management & performance monitoring solution
In-Depth Real-Time Monitoring Your Network Device Performance
7 Essential Firewall Management Strategies for Maximum Security

A firewall appliance is a fundamental pillar of network security, acting as the first line of defense against cyber threats. However, its strength is only as good as its configuration, monitoring, and ongoing maintenance. A poorly managed firewall is like a high-security vault with a weak lock—inviting trouble. Simply deploying a firewall isn’t enough; effective management is essential to ensure it remains a robust safeguard rather than a security blind spot.
Proper firewall administration involves real-time traffic monitoring, rule-set optimization, and timely updates to block evolving threats while allowing legitimate access. Without these crucial practices, even the most advanced firewall can become a liability, leaving your network exposed to exploitation.
To fortify your cybersecurity posture, here are seven essential best practices for effective firewall management.
Key Topics:
- Routing Testing and Patch Management
- Firewall Policy Optimization
- Monitor Firewall Performance
- Log Monitoring and Alerts
- Backup Firewall Rule Sets & Configuration
- Policy Decision-Making
- Periodical Reviewing of Firewall Access Controls
- Summary
Download your copy of the industry's leading Firewall Management Platform.
Routine Testing and Patch Management
Routine Testing: Your firewall needs regular testing to ensure it is working effectively. The testing includes vulnerability scanning, penetration testing, and compliance audits to identify weaknesses, simulate attacks, and ensure alignment with security standards.
Patch Management:Firewalls may develop vulnerabilities as time passes. Patch management is the process of installing updates and patches to fix these security weaknesses. It is essential to consistently update the software and firmware of your firewall to defend against new threats and maintain peak performance.
Example: Applying the most recent vendor patch when routine testing reveals a new vulnerability in your firewall software can help reduce this risk and improve the security of your network.
How to Protect Your Business with Microsoft 365 Security Tools
 Businesses of all sizes are more and more adopting cloud-based platforms like Microsoft 365 to streamline operations, improve collaboration, and increase productivity. However, this newfound reliance on such software solutions makes these businesses prime targets for cybercriminals.
Businesses of all sizes are more and more adopting cloud-based platforms like Microsoft 365 to streamline operations, improve collaboration, and increase productivity. However, this newfound reliance on such software solutions makes these businesses prime targets for cybercriminals.
With sensitive data stored and shared across the suite, securing your Microsoft 365 environment is essential to protect your business from potential threats.
Fortunately, Microsoft 365 comes with a robust set of built-in security tools designed to safeguard your organization from cyberattacks, data breaches, and other security incidents.
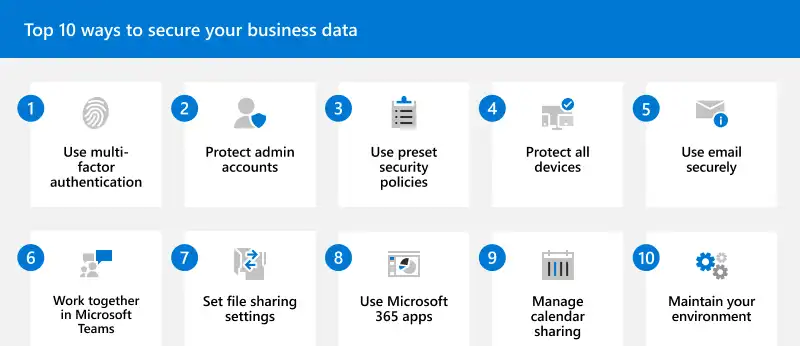
But despite that, we cannot ignore the importance of third-party Microsoft 365 total protection solutions. Without going too much into detail, these solutions enhance the already powerful native security features. But what are these features?
In this article, we’ll explore the key Microsoft 365 security tools you can use to protect your business.
Key Topics:
- Key Microsoft 365 Security Tools
- Best Practices for Leveraging Microsoft 365 Security Tools
- Conclusion
Related Articles:
- Boost Your Microsoft 365 Security with Expert Guidance and Proven Best Practices
- Empowering Users with Cyber Security Awareness Training
Key Microsoft 365 Security Tools to Protect Your Business
Microsoft Defender for Office 365
 One of the most critical security solutions within the Microsoft 365 ecosystem is Microsoft Defender for Office 365. This tool is specifically designed to protect against email-based threats such as phishing, malware, and ransomware, which are common attack vectors targeting businesses.
One of the most critical security solutions within the Microsoft 365 ecosystem is Microsoft Defender for Office 365. This tool is specifically designed to protect against email-based threats such as phishing, malware, and ransomware, which are common attack vectors targeting businesses.
Defender for Office 365 leverages real-time threat intelligence to detect and block malicious activity before it reaches your users.
Key features include:
Your IP address:
216.73.216.176
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Featured Categories:
Top Picks:
How to Enable or Disable SSH on VMware ESXi via W…
Understanding Deduplication. Complete Guide to De…

8 Critical Features to Have in a VM Backup Soluti…
How to Fix Palo Alto Firewall “Error: Image File…
The Most Common Worst Networking Practices and How To Fix Them
Key Features of a True Cloud-Native SASE Service. Setting the Right Expectations
SASE and VPNs: Reconsidering your Mobile Remote Access and Site-to-Site VPN strategy
Understanding Secure Access Service Edge (SASE) and how it integrates with SD-WAN

VLANs - Access & Trunk Links
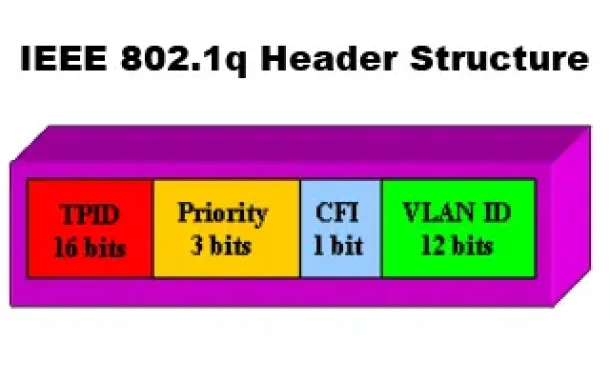
VLANs - IEEE 802.1q Trunk Link Protocol Analysis

VTP Introduction & Modes
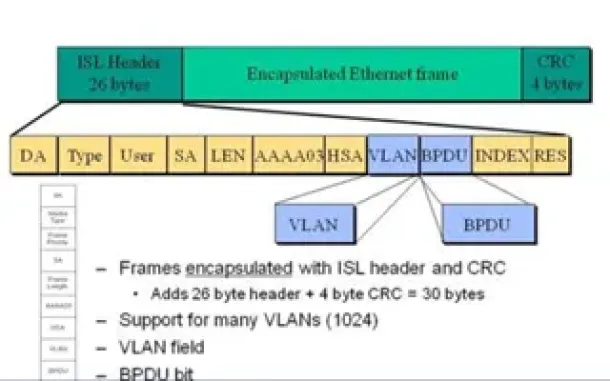
VLAN InterSwitch Link (ISL) Protocol Analysis
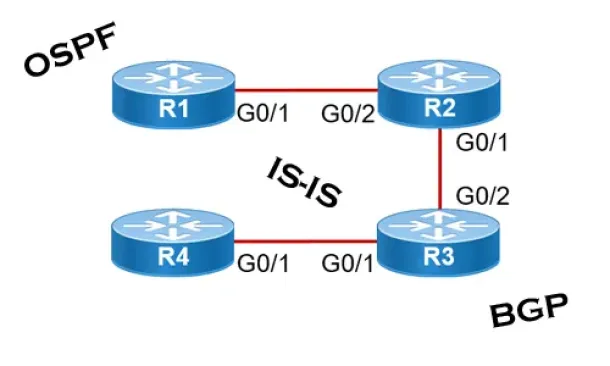
Link State Routing Protocols
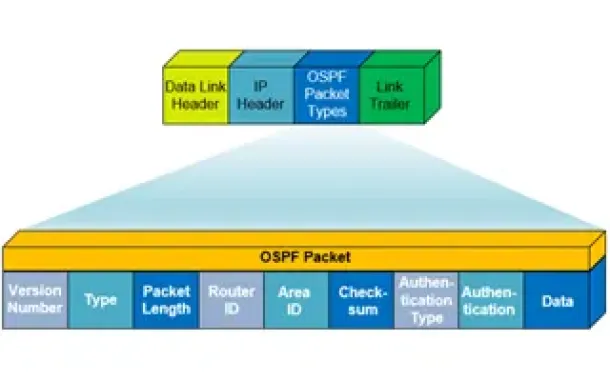
OSPF - Part 1: Introduction, OSPF Packet Structure, OSPF Messages and Characteristics
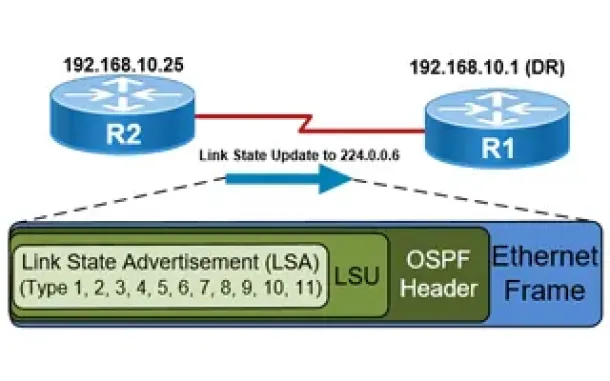
OSPF - Part 5: Analysis of OSPF Link State Update (LSU) - Link State Advertisement (LSA) Packet Structure. Common LSA Types