Suggested Articles:

ManageEngine Firewall Analyzer
Achieving Modern Compliance: Navigate PCI DSS v4…
In an era where cyber threats are growing in both volume and sophistication, failing to meet security compliance standards is no longer just a legal…
Network Protocol Analyzers
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…

ManageEngine Firewall Analyzer
Discover the Ultimate Firewall Management Tool: 7…
Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectively…
Network Protocol Analyzers
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
Featured Subcategories:
WireShark Articles:
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fire…
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emerging…
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall PAN-OS…
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, saf…
Windows Servers
Easy, Fast & Reliable Hyper-V & VMware Backup with Alt…
As more companies around the world adopt the virtualization technology to increase efficiency and productivity, Microsoft’s Hyper-V virtualization platfor…
Windows Servers
Simple Guide on Installing & Configuring a Windows 201…
A Windows Active Directory Certification Authority server (AD CA), also known as a Certificate Authority, is an essential service to every organization’s…
Windows Servers
The Importance of a Hyper-V & VMware Server Backup Too…
Using Hyper-V Server virtualization technology, you can virtualize your physical environment to reduce the cost of physical hardware. As part of IT best p…
Windows Servers
Download Altaro Free VM Backup & Win a PlayStation 4 P…
We have some exciting news for you today!
Altaro has launched a great contest in celebration of SysAdmin Day on 27th July!
They will be giving away Amaz…
Popular Topics
SASE & SD-WAN Networks
Configuring A SASE Unified Network: Data centers, Remo…
This article explores the need for Secure Access Service Edge (SASE) in today’s organizations. We show how one of the most advanced SASE platforms availab…
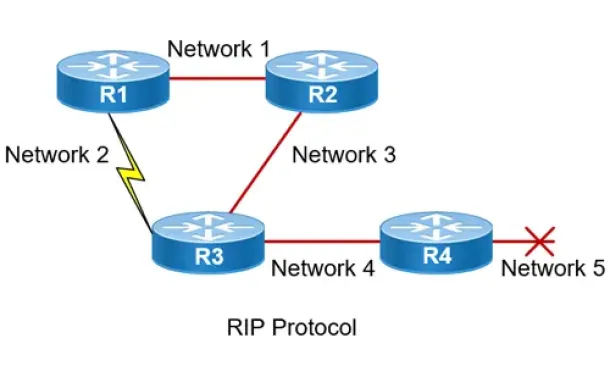
Routing
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…
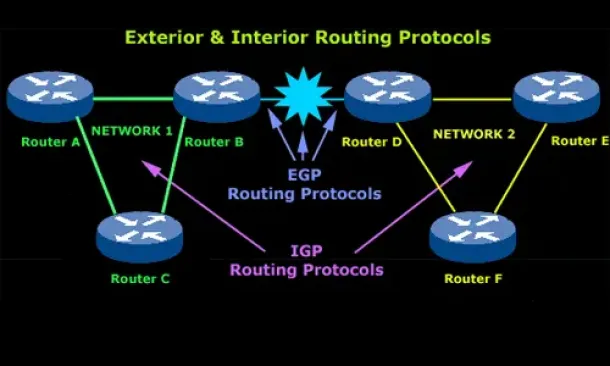
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchange…
Network Protocol Analyzers
Advanced Network Protocol Analyzer Review: Colasoft Ca…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review, the…
Cisco CallManager-CCME
Cisco Unity Express Installation & Setup - ISM-SRE-300…
Unity Express is a popular add-on for Cisco Unified Communication Manager Express (CallManager Express) and Cisco Unified Communication Manager (CUCM), ad…
Cisco Routers
Configuring Site to Site IPSec VPN Tunnel Between Cisc…
Site-to-Site IPSec VPN Tunnels are used to allow the secure transmission of data, voice and video between two sites (e.g offices or branches). The VPN tun…
Cisco Routers
Configuring Static Route Tracking using IP SLA (Basic)
In today's network environment, redundancy is one of the most important aspects, whether its on the LAN side or on the WAN side. In this topic we will be…
Cisco Firewalls
Cisco ASA Firepower Threat Defense (FTD): Download and…
One Appliance – One Image is what Cisco is targeting for its Next Generation Firewalls. With this vision, Cisco has created a unified software image named…



















