Suggested Articles:
Network Protocol Analyzers
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…

EventLog Analyzer
Event Log Monitoring System: Implementation, Chal…
An event log monitoring system, often referred to as an event log management, is a critical component to IT security & Management, that helps org…

ManageEngine Firewall Analyzer
7 Essential Firewall Management Strategies for Ma…
A firewall appliance is a fundamental pillar of network security, acting as the first line of defense against cyber threats. However, its strength…
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With Col…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addres…
Featured Subcategories:
WireShark Articles:
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
How to Register a Palo Alto Firewall and Activate Supp…
This article explains how to register and activate your Palo Alto Firewall Appliance to obtain technical support, RMA hardware replacement, product update…

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based Po…
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient wa…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
Part 1 of our Windows 2003 DHCP Server Advanced Configuration article explained the creation and configuration of DHCP Scope options and how to configure…
Windows Servers
Free Webinar: Troubleshooting & Fixing Microsoft Hyper…
Users working with Hyper-V Virtualization would be interested to know that Altaro is hosting a free webinar on the 25th of February 2016 at 4pm CET / 10am…
Windows Servers
Understanding, Creating, Configuring & Applying Window…
This article explains what Group Policies are and shows how to configure Windows Server 2012 Active Directory Group Policies. Our next article will cover…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
In this article, we will cover more advanced DHCP features and topics such as server options, superscopes, multicast scopes, dynamic DNS, DHCP database ba…
Popular Topics
Network Protocol Analyzers
How to Detect SYN Flood Attacks with Capsa Network Pro…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and inspect…
SASE & SD-WAN Networks
Complete Guide to SD-WAN. Technology Benefits, SD-WAN…
SD-WAN is the answer for enterprises and organizations seeking to consolidate network functions and services while at the same time simplify their WAN inf…
Routing
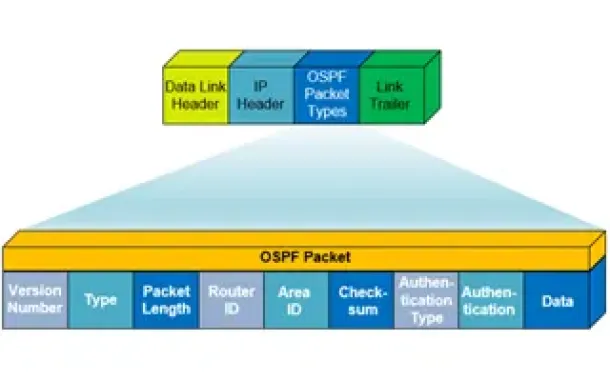
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
Windows Servers
Guide to Windows Server 2016 Hyper-V Hypervisor: New V…
One of Windows Server 2016 highlights is the newer Hyper-V server that not only extends the hypervisor’s features and capabilities but also introduces a n…
Cisco CallManager-CCME
Introduction to Cisco Unified Communication Manager Ex…
We have been hearing about VoIP for many years now and while some have never worked with it, it has become today's standard in IP Communications and Priva…
Cisco Routers
How To Configure ISDN Internet Dialup On A Cisco Router
Some time ago, when broadband and ADSL wasn't available, analog and digital (ISDN) modems were the only way to connect to the Internet. Even though today…
Cisco Routers
How and Why You Should Verify IOS Images On Cisco Rout…
Chances are we’ve all needed to upgrade our Cisco’s device IOS software at some point. While upgrading the IOS software on a Cisco device is considered to…
Cisco Firewalls
Cisco ASA 5500 Series Firewall Modules & Cards – Conte…
Cisco’s Adaptive Security Appliance (ASA) Firewalls are one of the most popular and proven security solutions in the industry. Since the introduction of t…



















