Suggested Articles:
Network Protocol Analyzers
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
OpManager - Network Monitoring & Management
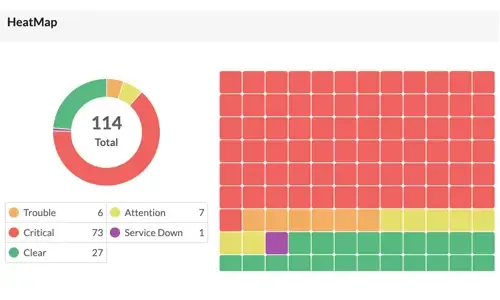
Boost Network Security and Efficiency with Intell…
Network alerts are vital for maintaining your network's health, efficiency, and security, ensuring seamless daily operations. They act as an early wa…

ManageEngine Firewall Analyzer
Challenges & Solutions to Managing Firewall Rules…
In today's interconnected digital landscape, where businesses rely heavily on networked systems and the internet for their operations, the importance…
Network Protocol Analyzers
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…
Featured Subcategories:
WireShark Articles:
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo Alt…
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our co…
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fire…
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emerging…
Windows Servers
How to Install and Configure Windows 2012 DNS Server R…
Our previous article covered introduction to the Domain Name System (DNS) and explained the importance of the DNS Server role within the network infrastru…
Windows Servers
The Importance of a Hyper-V & VMware Server Backup Too…
Using Hyper-V Server virtualization technology, you can virtualize your physical environment to reduce the cost of physical hardware. As part of IT best p…
Windows Servers
Free Webinar & eBook on Microsoft Licensing for Virtua…
Microsoft Licensing for Virtual environments can become a very complicated topic, especially with all the misconceptions and false information out there…
Windows Servers
Windows 2016 Server Licensing Explained – Free Webinar
With Windows 2016 Server already making its way into data centers Windows 2016 Server Licensing is becoming a very hot topic. Windows 2016 Server is jam-p…
Popular Topics
SASE & SD-WAN Networks
Configuring A SASE Unified Network: Data centers, Remo…
This article explores the need for Secure Access Service Edge (SASE) in today’s organizations. We show how one of the most advanced SASE platforms availab…
Windows Servers
How to Install Desktop Icons (Computer, User’s Files…
One of the first things IT Administrators and IT Managers notice after a fresh installation of Windows 2012 Server is that there are no Desktop Icons apar…

VLAN Networks
Static VLANs
VLANs are usually created by the network administrator, assigning each port of every switch to a VLAN. Depending on the network infrastructure and securit…
SASE & SD-WAN Networks
Key Features of a True Cloud-Native SASE Service. Sett…
Secure Access Service Edge (SASE) is an architecture widely regarded as the future of enterprise networking and security. In previous articles we talked a…
Cisco Routers
Cisco Router Modes
One of the greatest perhaps features of Cisco routers is that most commands used in the IOS software they run on, are identical across multiple platforms…
Cisco CallManager-CCME
CallManager Express & UC500 Series: Changing Backgroun…
Cisco's CallManager Express (Cisco router platform & UC520, UC540 & UC560) offers a number of customisation features aimed to allow the CCME admin…
Cisco Routers
How and Why You Should Verify IOS Images On Cisco Rout…
Chances are we’ve all needed to upgrade our Cisco’s device IOS software at some point. While upgrading the IOS software on a Cisco device is considered to…
Cisco CallManager-CCME
How to Register Cisco IP Phones & Connect CallManager…
This article shows how to connect Cisco's Unified CallManager with a CallManager Express system (including UC520, UC540 and UC560) via H323 gateway, allow…



















