Anonymous Browsing – Internet Privacy. Securing Your Online Privacy The Right Way
 Despite what some think, the internet is not private. Anonymous browsing and Internet Privacy are almost non-existent in today's online world. Websites collect personal information on every visit without your knowledge. Despite the free label, services come at a cost, and in many cases, it’s a lack of privacy.
Despite what some think, the internet is not private. Anonymous browsing and Internet Privacy are almost non-existent in today's online world. Websites collect personal information on every visit without your knowledge. Despite the free label, services come at a cost, and in many cases, it’s a lack of privacy.
The primary driver is the advertising industry. Most websites get paid if an ad is clicked or the product is purchased, not just for exposure. As a result, they want promotions that are relevant to the user. They get paid, and the user gets to see the products they’re interested in. It seems advantageous to both parties.
However, to target these ads, agencies need information about a website’s users. Companies like Facebook embed trackers across the web to build a detailed profile of individuals. This includes things like your gender, age, location, and websites you frequent. Information from multiple ad agencies can then be combined to build a detailed picture of your interests and personality.
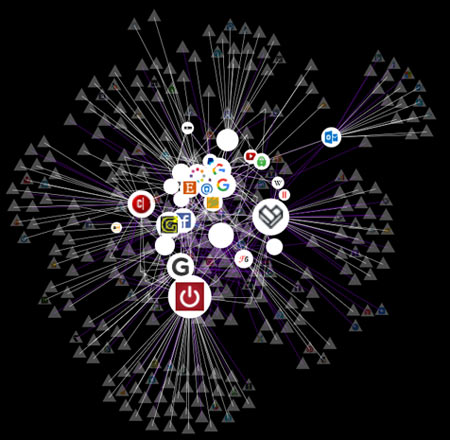
Firefox's Lightbeam Plugin provides a visual map of sites visited during our session
Here’s the result of two hours of browsing activity with the Lightbeam plugin. The circle articles are sites we visited, while the triangles are third parties. Together, they can create an interconnected web of information. Visiting just 32 sites fed 371 third parties data!
They can do this across the web through identifying information like your IP address. When you connect to a network, your device is given a unique string of numbers by the ISP or mobile service provider. These can be cross-referenced across the internet to find your browsing habits.
If that’s not enough, there are also government agencies to worry about. IP addresses usually give websites a rough idea of your location by pointing to your service provider. That’s not a barrier for government. They can ask the ISP who the IP was assigned to and find your name and address. You would think that such power would be used sparingly, but unfortunately, it’s not.
Former NSA contractor Edward Snowden revealed that major powers are spying on citizens across the world on an unprecedented level. Authorities request all that tracking data we mentioned earlier and combine it with information from the internet service provider (ISP). From 2011-2012, Australian agencies requested ISP logs over 300,000 times. This can include every website the user has visited over a period of years.
And that’s someone who has the country’s best interests at heart. This kind of information is also accessible to a number of people who work for the ISP. Earlier this year, an ex-technician for Verizon pleaded guilty to selling phone call and location information to a private investigator. Web browsing information could equally be sold off to the highest bidder.
And that’s assuming they even have to buy it in the first place. In 2012, internet activist group anonymous hacked into the servers of telecommunications company AAPT. They stole over 40GB of information relating to business customers to show that the logs are not always safe. A redacted copy of the data was later published online.
What is the Threat?
With so many parties interested in such data, anonymous browsing is becoming difficult. The sad fact is that without protection from the Best VPN providers, you aren’t truly safe.
Firstly, there’s the threat of this information falling into the hands of hackers. Imagine a person with malicious intent having a record of your name, address, interests, habits, and every website you’ve been to. It could easily be used to blackmail someone or make threats to their friends and family.
It can also be used to identify potential weak points in your security. For example, if you regularly visit an insecure site, it could be hacked with an end goal of getting to you. Tools such as a key logger could then be used to collect usernames, passwords, and credit card data.
Furthermore, such access can be used for types of identity theft. Combined with an email account, an attacker has access to basically everything. Password resets for various accounts, name, age, date of birth. Bank details can be used to place illegal purchases on your behalf or commit fraud. Most of our lives are stored online, and the attack could gain access to all of it.
The same methods can be used by authorities in oppressive regimes. Even if the current government protects its citizens from such things, a power shift could change that. Because tracking information and ISP logs are kept for a long time, the data will still be around years into the future.
Then there’s the issue of illegal activities. Previously, nobody would know if you were breaking the law in the privacy of your own home. However, with the increase in logs, activities like torrenting can result in warnings, loss of service, or huge fines.
Without a VPN, torrents can be traced straight back to the user. Copyright holders hire companies to search through swarms of people torrenting their property. With an IP address, they can request a user’s details from the ISP and pursue legal action. The ISP is often compelled to do this or face legal repercussions themselves.
Though torrenting is a morally grey area, this can also affect customers who have done nothing wrong. WiFi networks can be hacked or information can be incorrect. In 2010, 53-year-old Cathi Paradiso ran into this problem when she was accused of downloading 18 films and TV shows illegally. In reality, her IP address was identified incorrectly, and her internet access cut off unjustly. It’s clear that even if you’re a regular internet user, anonymous browsing has its benefits.
What Is Anonymous Browsing & How Does it Help?
Anonymous browsing is usually achieved by routing a normal internet connection through a virtual private network. We won’t go into too much detail here, as it’s been already covered in our Beginner’s Guide to VPNs.
However, it’s important to have a basic idea of how a VPN can provide anonymous browsing. A VPN uses a method called tunnelling to wrap the data packets you send to your ISP in encryption. Various methods such OpenVPN, L2TP, PPTP and STTP are used to achieve this. Through a VPN, your information goes from clear and readable to a string of random letters and numbers.
As a result, those trying to grab the data in transit get a useless pile of text. They don’t have the cypher, so they can’t unlock it. This is particularly useful on public WiFi, where hackers can often see what you are doing and perform attacks.
It also has the knock-on effect of hiding your IP address. The connection goes through the servers of the VPN provider, where’s its assigned an anonymous IP from the server. Unlike ISPs, the best VPNs don’t keep logs. The original IP address can’t be compelled by third-parties, and the user can surf anonymously.
However, this anonymous browsing doesn’t always extend to web trackers. Various methods can allow them to grab identifying information like IP addresses despite a VPN connection. Thankfully, many of the providers have built-in protection for this. Domain Name Server requests are routed through their servers and resolved by a special process that protects the user. As a result, malicious domains can’t find the user’s true identity.
How to Get VPN Services
Fortunately, it’s quite easy to browse anonymously via a VPN. There are thousands of different providers out there, each with different merits and price points. Some can even be used free of charge, but they can be subject to bandwidth caps and have been sold user data. For a premium and safe service, it’s always best to go with a paid provider.
We strongly recommend you examine StrongVPN - one of the most stable and fast VPN service providers globally.
Luckily, we have a round up all the best VPNs so that you don’t have to search through hundreds yourself. Our experts have rounded up all the major features of each, ranking them based on quality.
Once you have found one that meets your requirements, you’ll have to sign up. You usually need an email address, password, and a payment method. The privacy conscious can often use bitcoins or trade gift cards to protect their identity while paying.
That payment can be anywhere between $3-$8 per month, depending on provider. You usually get a better service the more you pay, but there are some exceptions. Either way, it’s a small price for anonymous browsing, whether you’re using a VPN to torrent, or just conscious about types of identity theft and government surveillance.
On sign up, you usually get an email with a username and password, as well as a link to the login page. Some providers will take care of this for you through a download link that incorporates sign-in details.
You then install the program, enter your details, and click connect. They have clients for all the major platforms, including Mac OSX, Windows, iOS, and Android. The Βest VPN providers have thousands of servers all over the world and can provide fast, anonymous browsing in a few minutes.
Some VPNs provide details for an additional SOCKS5 proxy, which you can read about here. This can provide anonymous browsing against web hosts, but not the ISP or government.
Best Practices For Enhanced Protection
Though VPNs are great for browsing anonymously, they aren’t infallible. There are many methods to get information, and the providers can’t protect against them all. For complete anonymity on the internet, you may want to take some additional steps.
Cookies & Browser History
One thing a VPN cannot control is the data that’s stored locally on your computer. As you browse the web, your computer keeps a record of the history so you can go back to it later. It also retains cookies, which will save your settings on various websites, and images, so that you don’t have to download them every time.
The implications of this are fairly straightforward. If somebody gets access to your computer, physically or remotely, they have tons of information about you. To avoid this, you’ll want to use the “Private Browsing” feature in your browser.
In Firefox, you can get there by hitting the fly out menu on the top right and pressing New Private Window. Alternatively, you can press Ctrl+Shift+P.
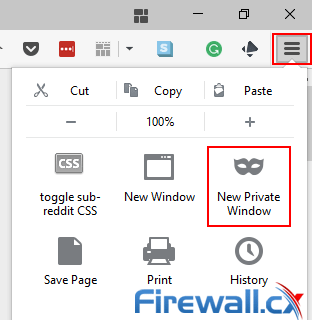
Anonymous browsing in Firefox- Enabling a new private window
The things you do in this session will not be recorded. That covers the pages you visit, cookies, searches, and temporary files. There’s also the option for tracking protection, which will block many of those third parties we talked about earlier. However, Firefox does keep downloads and bookmarks for later use.
![]()
Mozilla also stresses that Private Browsing doesn’t necessarily mean anonymous browsing. By itself, this is no protection against the information ISPs and government agencies collect. You’ll still need a VPN for that.
Google Chrome users can make use of a similar feature, though it has a different name. Incognito mode provides much of the same functionality but doesn’t have tracking protection like Firefox. Its shortcut is also different, using Ctrl+Shift+N.
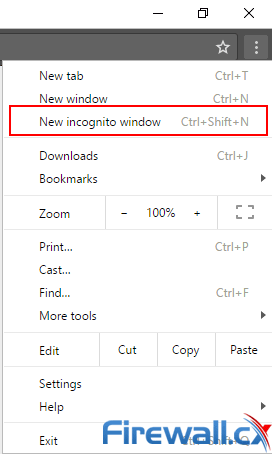
Anonymous browsing chrome - Enabling a incognito mode window
Like Mozilla, Google stresses that Incognito mode does not provide anonymous browsing at work, home or any other location. Once more, files and bookmarks are still stored, so you have to be careful to delete those afterwards.
Other browsers have this functionality built in. In Internet Explorer and Edge, it’s called In Private Browsing/Window, with the same Ctrl+Shift+P shortcut as Firefox. Mac OSX users can use Private Browsing in Safari for the same effect.
Though they took a little while to catch up, most mobile browsers support it too. In Firefox, it’s called “New Private Tab” while in Chrome it's “New incognito tab”. Most Android stock browsers also support private browsing, though there are a few exceptions.
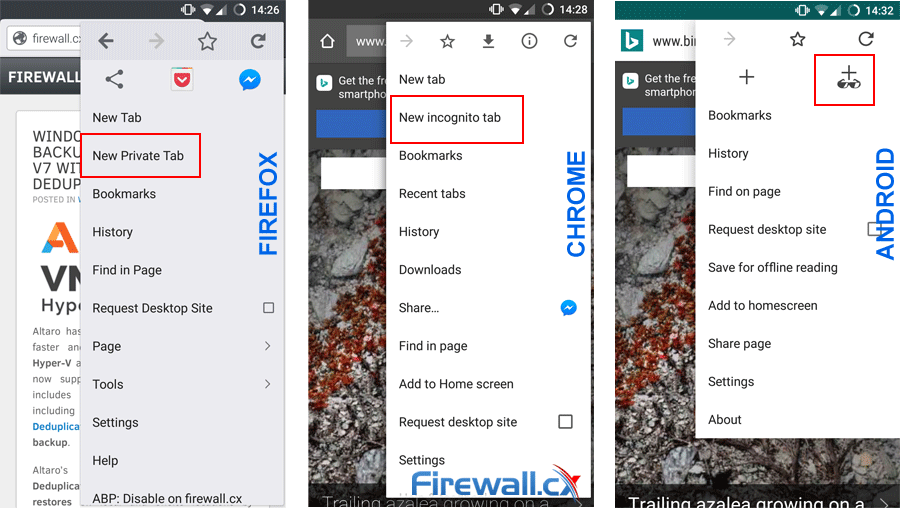
Enabling safe private browsing in Firefox, Chrome and Android O/S
The Safari browser on iOS also supports anonymous browsing. It can be found by hitting the icon, tapping Private, and then Done. This applies to iPads, iPods, iPhones, and most other Apple devices.

Safari Web Browser - Private Mode
Web Trackers & Encryption
Unfortunately, Firefox is the only one of these browsers that fights tracking. We highly recommend using Firefox if you are privacy conscious, but sometimes that’s not possible. For enhanced anonymous browsing, you should consider using browser plugins on Chrome, Firefox, or Edge.
Privacy Badger
Privacy Badger is an extension created and managed by the Electronic Frontier Foundation (EFF). It stops third-party trackers from following you across the web. Based on smart algorithms and policies, it brings protection to windows that aren’t private browsing. It’s also a little more advanced than Firefox’s methods.
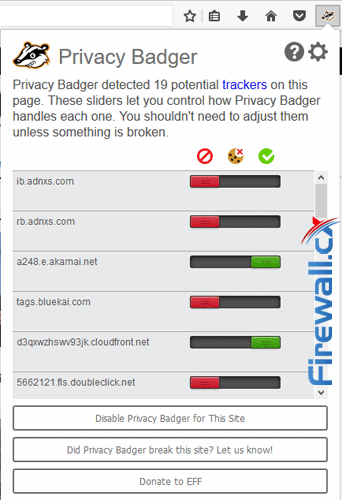
Privacy Badger Help Enforce Anonymous Browsing
However, Privacy Badger can prevent some functions like sharing articles to Facebook. Thankfully, EFF has built a simple slider system that lets you turn trackers on and off at will. Green means the tracker is third-party but isn’t following you across the web, so it’s allowed. Red means it has been completely blocked. Yellow means the tracker is necessary for web browsing, but it’s cookies have been blocked.
There is one caveat. Privacy Badger blocks third-party trackers, but it doesn’t stop tracking from the first party websites.

Referring to our diagram, it blocks all the little triangles, but not the large circles. If you frequently visit a website, they may still collect information. You should still be using a VPN if you want to surf anonymously.
uBlock Origin
As well as Privacy Badger, you may want to consider an Ad-Blocker. uBlock Origin has a dual purpose, blocking trackers and malware as well as advertisements. It’s compatible with Privacy Badger, so you can use both at the same time.
What’s more, uBlock protects against WebRTC leaks. WebRTC is a communications protocol that lets you share files and video in real-time without the need for plugins. Unfortunately, it can also reveal a user’s true IP address, even if they’re using a VPN.
You can enable protection in uBlock Origin by hitting the settings tab. Under the Settings tab, you’ll see an option named Prevent WebRTC from leaking local IP addresses. Hit the checkbox and you’re done:
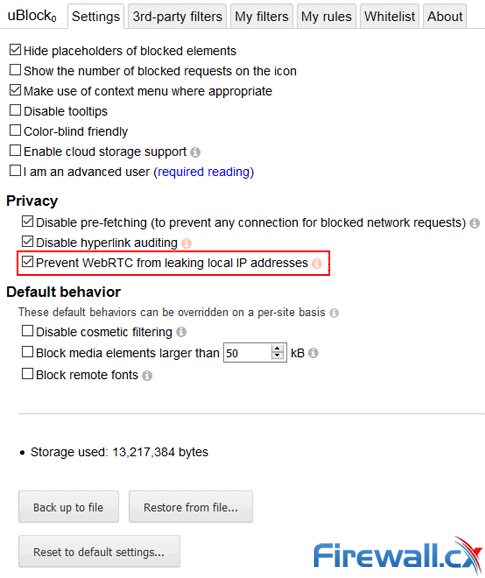
uBlock Origin - Protection Against Malware, Trackers & WebRTC
It’s worth noting that this feature won’t provide anonymous browsing if you aren’t using a VPN. It only hides your local IP address, so the IP of non-VPN users will be visible.
HTTPS Encryption
You should also be forcing a HTTPS connection wherever possible. HTTPS provides SSL encryption, which makes it harder for attackers to intercept your communications. This is particularly important if you’re using public WiFi. Visiting a HTTP website lets attackers packet sniff and spy on what you are doing. This can lead to the capture of passwords, bank details, or personal information.
Though using a VPN will protect you from this, it never hurts to have an extra layer of protection. Before the initial connection of a VPN there’s a small window where you are connected to WiFi, but not to the VPN. It can also be a problem if your VPN cuts out and you don’t a backup.
Though HTTPS is rapidly spreading, the implementation is still limited on many websites. Visiting the site from a link with “http://” in front often takes users to the unencrypted version. This can be a major problem if the site links back to itself this way.
Thankfully, EFF has a solution once more. HTTPS Everywhere forces SSL encryption no matter what link you click. It uses “clever technology” to rewrite requests into a HTTPS format and prevent interception.
Though HTTPS Everywhere can’t help when sites don’t support SSL at all, it does create a more consistent experience on those that do. It will also warn you when portions of a website can’t be encrypted, such as images. When you’re on Public WiFi, you can additionally choose to block all HTTP sites.
By itself, HTTPS Everywhere does not provide anonymous browsing. An interested party will still be able to see what web pages you are accessing. However, on sites that support SSL, it will stop people on the same network seeing specifics.
The Tor Browser
Finally, the extra conscious can use Tor to protect their identity. The Tor Browser bundles several add-ons into its core, including NoScript, an extension that blocks JavaScript, Flash and Java tracking. It also incorporates HTTPS Everywhere for added protection.
However, Tor’s main privacy feature is its underlying protocols. Communication in Tor is layered in encryption. Data sent through the browser goes through another user’s computer, each decrypting a small chunk. Each link in the chain only knows the IP address of the computer before it, so the user can surf anonymously.
Though Tor has some security issues, it can be used on top of a VPN to provide an extra barrier for attackers or law enforcement to get through. It’s not a substitute for a paid VPN, but it does provide considerable protection over regular browsing.
Mobile Devices
On mobile devices, anonymous browsing can be harder to achieve. If you don’t want to be tracked across the web, you may have to change your browser.
Unlike Firefox, Chrome does not support extensions on mobile. This means the aforementioned addons can’t be installed. To surf anonymously, you should be using Firefox or a dedicated privacy browser.
Users of Mozilla’s browser can go to addons.mozilla.org/android and pick up HTTPS Everywhere, uBlock, and Privacy Badger just like on desktop. They require no additional permissions and work just as well.
If you don’t like Firefox, there’s still a few options:
- Ghostery Browser (Android, iOS)– inbuilt tracking protection and other privacy features.
- Brave Browser (Android, iOS) – inbuilt Adblock, tracker protection, HTTPS Everywhere, Script blocking, and tracker blocking.
- Orfox (Android) – Official Tor-based browser with NoScript and HTTPS Everywhere, automatic history and cookie deletion. Removes permission requests for Contacts, Camera, Microsoft, Location and NFC. Removes WebRTC.
- Onion Browser (iOS) – Unofficial, open source Tor browser. NoScript-like mode and user-agent spoofing.
Despite these methods, it’s important to realise that mobile devices are not a substitute for desktop when it comes to anonymous browsing. By default, phones have far more in-built tracking, from location services, cell towers, and more. If you’re doing something questionable, it's best to stick to a PC.
Summary
The bottom line is that though you can add protection free of charge, it wont give fully anonymous browsing like a VPN. Though uBlock and Privacy Badger protect against web tracking, they do nothing to stop spying by ISPs or government agencies.
A VPN can protect users against web tracking, ISP tracking, government spying, and man-in-the-middle attacks. They are low-cost, easy to implement, and allow a fast browsing experience, unlike Tor. Though they aren’t perfect, extra precautions make them as close to it as possible. VPNs are therefore the natural solution for anonymous surfing at work, on public WiFi, or at home.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














