TCP Header Anaylsis - Section 7: TCP Data Payload Analysis
Finally, the last page of our incredible TCP Analysis. As most of you would expect, this section is dedicated to the DATA section that follows the TCP Header.
The Data Section
The following diagram may have been tiresome, however, it will be displayed one final time to note the data portion of the packet:
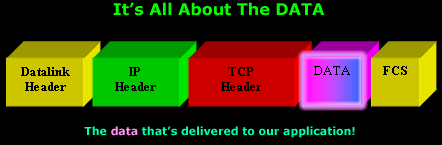
Your knowledge regarding the procedure followed when the above packet arrives to its destination is assumed. However, a summary is given below to refresh our understanding in order to avoid confusion.
When the above packet arrives at the receiver, a decapsulation process is required in order to remove each OSI layer's overhead and pass the Data portion to the application that's waiting for it. As such, when the packet is received in full by the network card, it is given to the 2nd OSI layer (Datalink) which, after performing a quick check on the packet for errors, it will strip the overhead associated with that layer, meaning the yellow blocks will be removed.
The remaining portion, that is, the IP header, TCP header and Data, now called an IP Datagram, will be passed to the 3rd OSI layer (Network) where another check will be performed and if found to be error free, the IP header will be stripped and the rest (now called a Segment) is passed to the 4th OSI layer.
The TCP protocol (4th OSI layer) will accept the segment and perform its own error check on the segment. Assuming it is found error free, the TCP header is stripped off and remaining data is given to the upper layers eventually arriving at the application waiting for it.
Summary
Our in-depth analysis of the the TCP protocol has reached its conclusion. After reading all these pages, we are sure you have a much better understanding regarding the TCP protocol's purpose and process, and you are able to really appreciate its functions.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














