Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
|
Articles:
VLAN Security - Making the Most of VLANs
| Read |
|
Articles:
VTP Pruning
| Read |
|
Articles:
VTP Protocol - In-Depth Analysis
| Read |
|
Articles:
VTP Introduction & Modes
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
VLANs - Access & Trunk Links
| Read |
|
Articles:
Dynamic VLANs
| Read |
|
Articles:
Static VLANs
| Read |
| Read | |
|
Articles:
The VLAN Concept - Introduction to VLANs
| Read |
Suggested Articles:
Network Cabling
10Base-T/2/5/F/35 - Ethernet
The 10Base-T UTP Ethernet and 10Base-2 Coax Ethernet were very popular in the early to mid 1990's when 100 Mbps network cards and hubs/switches were…
Subnetting
IP Subnetting - Part 2: Subnet Masks & Their Effe…
There are a few different ways to approach subnetting and it can get confusing because of the complexity of some subnets and the flexibility they off…
ICMP Protocol
ICMP Protocol - Part 1: Introduction
The Internet Control Message Protocol (ICMP), is a very popular protocol and actually part of an Internet Protocol (IP) implementation. Because IP wa…
Network Cabling
Serial Direct Cable Connection, DB9, DB25, COM Po…
This article covers the popular serial ports on workstations, servers and laptop computers. We cover serial data transfer, port pinouts, port speeds…
Featured Subcategories:
Netflow Articles:
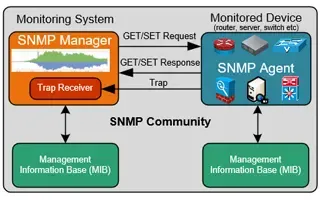
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
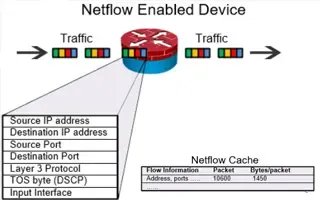
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
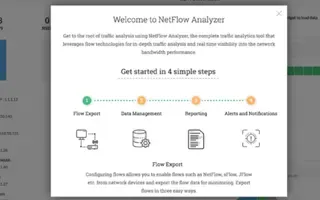
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
InterVLAN Routing - Routing between VLAN Networks
This article deals with the popular topic of InterVLAN routing, which is used to allow routing & communication between VLAN networks. Our article anal…

VLAN Networks
VTP Introduction & Modes
The invention of VLANs was very much welcomed by all engineers and administrators, allowing them to extend, redesign and segment their existing network wi…

VLAN Networks
Comparing Traditional Flat & VLAN Networks
Designing and building a network is not a simple job. VLANs are no exception to this rule, in fact they require a more sophisticated approach because of t…
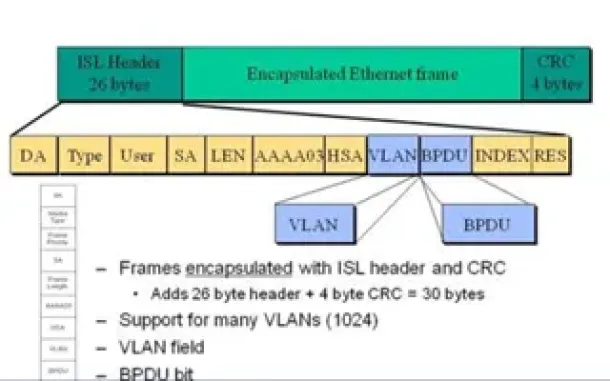
VLAN Networks
VLAN InterSwitch Link (ISL) Protocol Analysis
Deciding whether to use ISL or IEEE 802.1q to power your trunk links can be quite confusing if you cannot identify the advantages and disadvantages of eac…
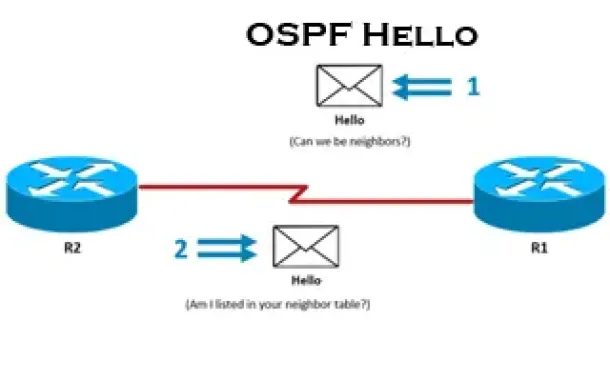
Routing
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Proce…
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll examine…
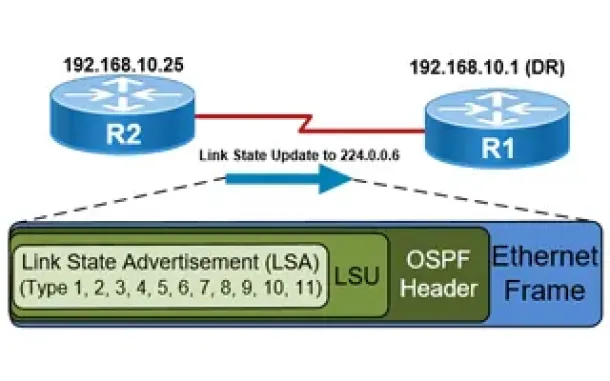
Routing
OSPF - Part 5: Analysis of OSPF Link State Update (LSU…
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router recei…
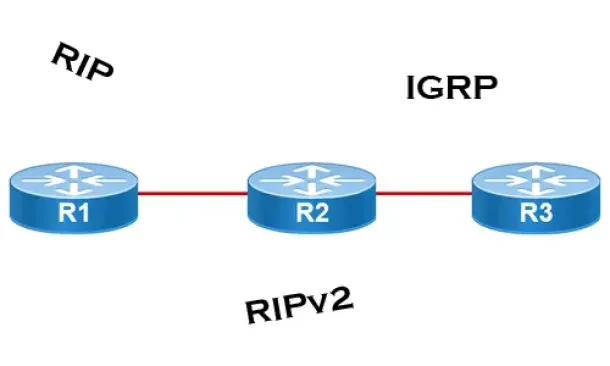
Routing
Distance Vector Routing Protocols
Distance Vector routing protocols use frequent broadcasts (255.255.255.255 or FF:FF:FF:FF) of their entire routing table every 30 sec. on all their interf…
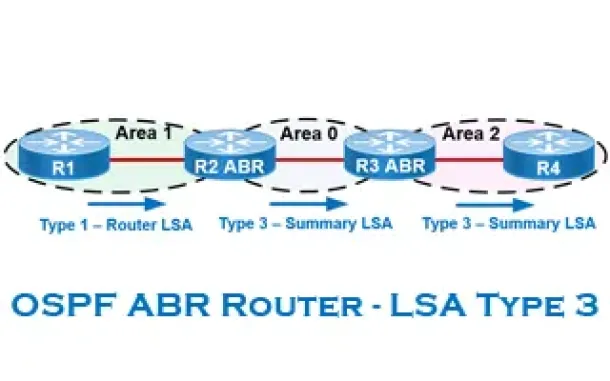
Routing
OSPF - Part 6: OSPF LSA Types - Purpose and Function o…
Our previous article explained the purpose of Link State Update (LSU) packets and examined the Link State Advertisement (LSA) information contained within…
Cisco Routers
Cisco Type 7 Password Decrypt / Decoder / Crack Tool
The Firewall.cx Cisco Password Decoder Tool (see below) provides readers with the ability to decrypt 'Type 7' cisco passwords.
For security reasons, we d…
Cisco Switches
How to Disable or Enable the Password Recovery Procedu…
Our previous article shows how to perform a password recovery on the Cisco Catalyst switches. This article will now explain how to disable or enable the C…
Cisco Wireless
Wireless (Wifi) WEP WPA WPA2 Key Generator
The Firewall.cx Wireless LAN Key Generator will allow the generation of a WEP or WPA ASCII based encryption key and will provide the equivalent HEX or…
Cisco Routers
How To Fix Cisco Configuration Professional (CCP) Disp…
Cisco Configuration Professional (CCP) is Cisco’s latest GUI administration tool used to administer Cisco routers. CCP is basically the next step up from…



















