Boost Firewall Security with Automation: Compliance, Vulnerability, Validation & Real-Time Control
 Firewall automation is becoming essential as organizations strive to streamline configuration management, enforce compliance, and boost security across increasingly complex infrastructures. Without the right tools in place, misconfigurations and policy gaps can quietly take root within enterprise networks, exposing them to escalating threats. The challenge isn’t just visibility — it’s the ability to apply consistent policies, detect drift early, and ensure continuous validation at scale. Without automation, these tasks become too resource-intensive to maintain effectively, especially in environments with multiple vendors, users, and changing business demands.
Firewall automation is becoming essential as organizations strive to streamline configuration management, enforce compliance, and boost security across increasingly complex infrastructures. Without the right tools in place, misconfigurations and policy gaps can quietly take root within enterprise networks, exposing them to escalating threats. The challenge isn’t just visibility — it’s the ability to apply consistent policies, detect drift early, and ensure continuous validation at scale. Without automation, these tasks become too resource-intensive to maintain effectively, especially in environments with multiple vendors, users, and changing business demands.
This is where firewall automation proves transformative. By continuously tracking configuration changes, validating against compliance rules, and detecting vulnerabilities in real time, automation fills the gaps that manual oversight inevitably leaves behind. The result is a proactive security posture — one that blocks threats, enforces policy uniformly, and maintains resilience without compromising operational agility.
In this article, we explore how firewall automation reduces risk, accelerates efficiency, and strengthens control. Key areas covered include configuration management, compliance policy enforcement, firmware vulnerability detection, and the deployment of remediation templates and configlets to streamline operational workflows across complex environments.
Key Topics:
- Configuration Control and Drift Validation
- Using Configuration Templates for Scalable Change Deployment
- Compliance Policies with Continious Validation
- Firewall Vulnerability Mapping and Risk Scoring
- Remediation Templates and Automated Rollback
- Network Automation and Integration with IT workflows
- Identity-aware Controls and Internal Traffic Visibility
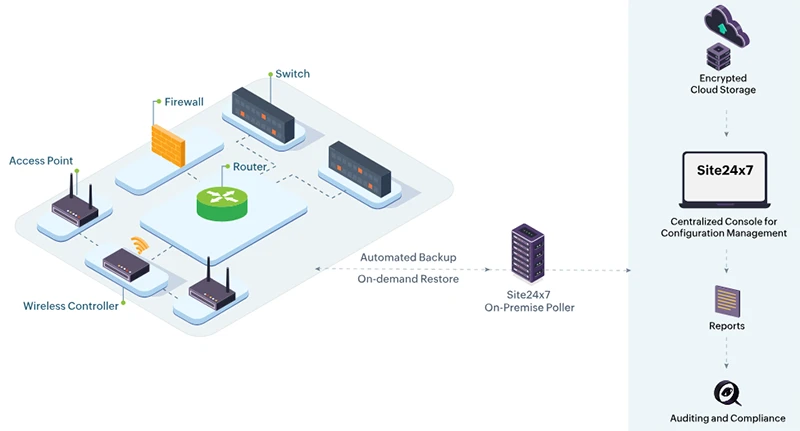
- Site24x7 Network Configuration Manager
- Summary
Configuration Control and Drift Validation
Business applications shift, projects launch, and policies evolve. These changes often introduce new access requirements, temporary exceptions, or updates to Network Address Translation and access control list (ACL) configurations. Manual workflows in such scenarios often become resource- and cost-prohibitive. Without centralized visibility and control, this leads to configuration drift across firewalls.
Automated version tracking addresses this by creating a complete audit trail for every configuration.
Administrators can easily compare versions, pinpoint unauthorized changes, identify the user who made them, and roll back to a known good state. Drift trends and rollback frequency can also highlight devices that require deeper scrutiny. Suppose a device experiences repeated rollbacks or frequent unauthorized edits. In that case, it means that the device requires tighter oversight or policy revision since even internal and external threat actors could be the cause of the changes. This greater scrutiny helps network administrators track if the changes are planned, traceable, and aligned with approved policies.
Configuration management helps:
- Automate version tracking to ensure accurate record keeping
- Detect unauthorized changes and flag risky edits
- Track drift trends and rollback events for better oversight
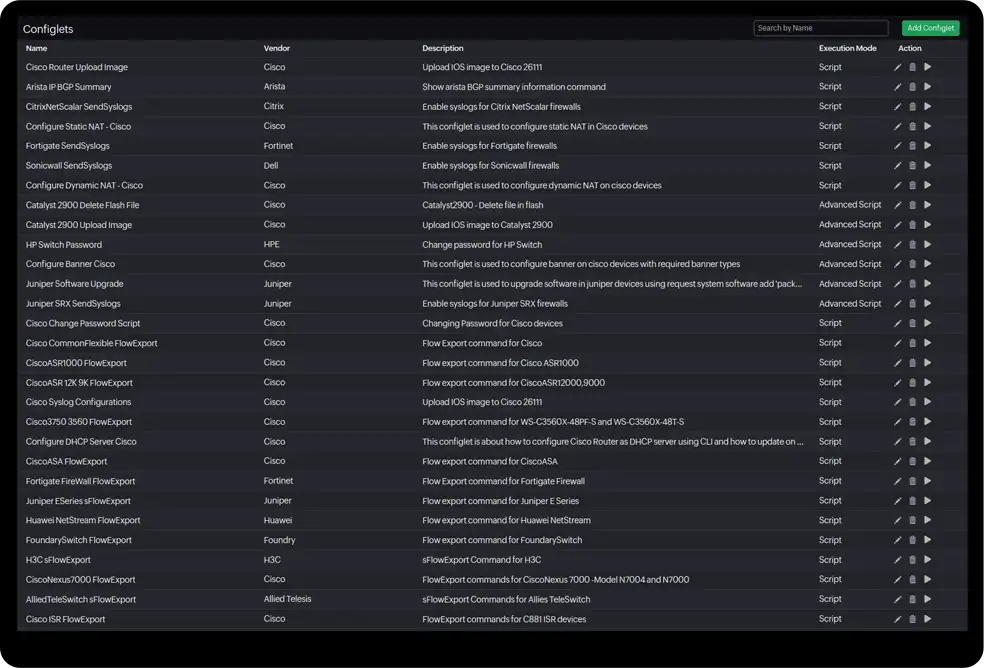
Using Configuration Templates for Scalable Change Deployment
Configuration templates (or configlets, as it is called in a few tools) are modular snippets of configuration logic. They can be used to standardize and push configuration changes across multiple devices with minimal variation. Unlike monolithic configuration files, configlets allow teams to build reusable blocks for common tasks, such as enforcing logging, disabling legacy protocols, or defining traffic shaping rules.
In a network with a mix of firewall vendors and models, configlets can be customized to device types and OS versions. This flexibility enables teams to deploy a unified policy framework without rewriting configurations from scratch for every environment.
For instance, a configlet enforcing interface-level SSH access could minimize configuration differences between Fortinet and Palo Alto devices. When policy updates are required, the central configlet is updated once and pushed automatically to the relevant devices.
Configuration templates, or configlets:
- Support multi-vendor deployment with reusable logic
- Reduce configuration errors and effort
- Enable uniform policy rollouts across environments
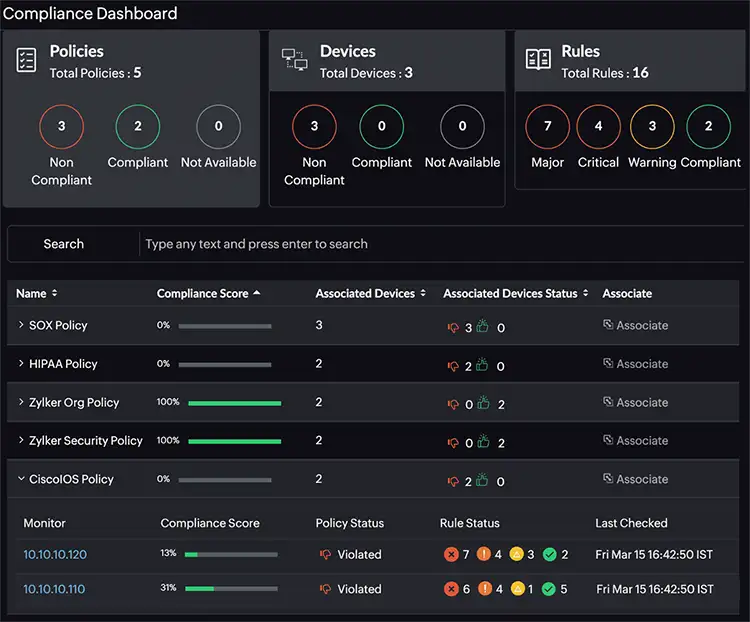
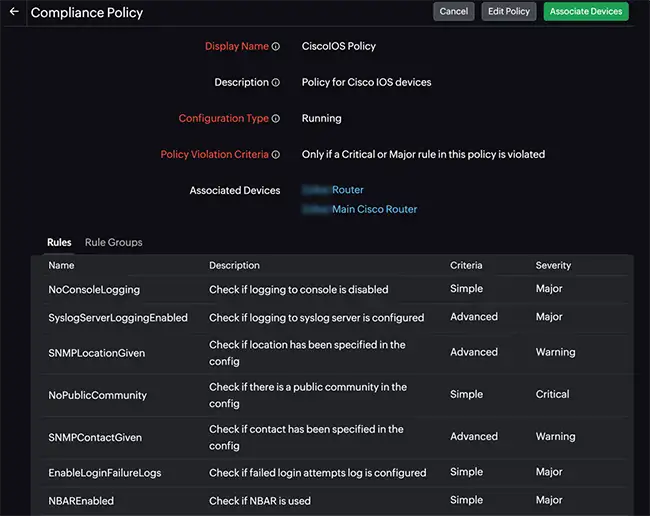
Compliance Policies with Continuous Validation
Internal policies and external standards like PCI-DSS or HIPAA require firewalls to follow specific control requirements. These might include disallowing insecure services, enforcing SSH access for administration, or applying deny-first ACL strategies. Defining these policies is straightforward. Verifying them across a dynamic environment is not.
Compliance automation tools enable teams to define these rules once and then apply them continuously across all monitored devices. Policies are written as condition-based checks that validate configuration structure and values. Failures generate real-time alerts, annotated audit logs, and compliance scoring dashboards.
For example, a custom rule might require that all management interfaces reject HTTP connections and allow only HTTPS and SSH. When a new device is added or reconfigured to permit HTTP, the system identifies the violation and can optionally remediate it using a predefined configlet.
Compliance automation helps:
- Enforce custom compliance policies at scale
- Validate the configuration structure continuously
- Flag violations and generate audit-ready reports
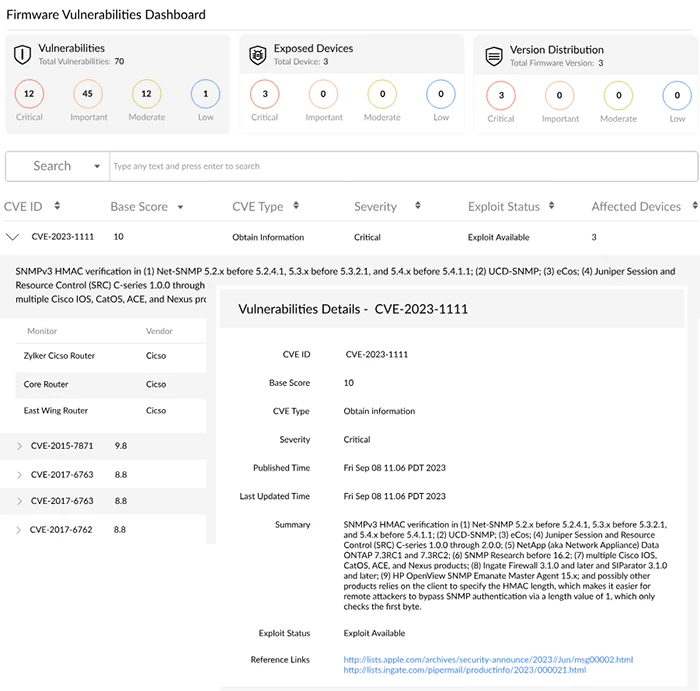
Firmware Vulnerability Mapping and Risk Scoring
Firewall software should be regularly updated to fix bugs and patch vulnerabilities. In larger environments, tracking version numbers and matching them to vendor advisories becomes difficult. It's not unusual for teams to overlook critical CVEs affecting older firmware, especially when no official end-of-support notice has been issued.
Firmware vulnerability management automates this mapping process. The system collects OS version data from each device. It compares the versions with a curated feed of security advisories and CVEs from organizations like the NIST. Devices are flagged if the installed firmware matches a known vulnerable version. Teams receive reports that prioritize devices by risk exposure and exploit availability.
Consider a network where different branches use different models of the same firewall platform. When a remote code execution flaw is disclosed for a particular version, automation pinpoints the exact locations where that version is active and helps schedule patching or configuration-based mitigation.
In short, firmware vulnerability management helps:
- Map OS versions to vendor CVEs automatically
- Prioritize patching based on risk and exposure
- Provide location-specific remediation planning
Remediation Templates and Automated Rollback
If a vulnerability or compliance issue is detected, the next step is resolution. Remediation templates define pre-authorized actions that can be applied across devices to bring them back into a baseline state. These templates can include specific configuration lines, access list rules, or even interface shutdown commands.
By standardizing the remediation process, teams reduce the likelihood of introducing new errors. Templates also support accountability by linking every action to a triggering condition and a historical execution log.
Automated rollback mechanisms are also vital during incident response. Suppose administrators observe that multiple devices in a specific region of the topology are down and trace the issue to a configuration change. In that case, they can deploy a remediation template to promptly correct the conflicting lines across all impacted devices—minimizing downtime and avoiding repetitive manual intervention.
Remediation templates help:
- Define reusable corrective actions
- Improve remediation speed and accuracy
- Ensure consistent rollback during incidents
Network Automation and Integration with IT Workflows
Firewall configuration management does not touch change management, incident response, compliance reporting, or vulnerability remediation. Network automation connects all these aspects, reducing time to resolution and improving consistency. A configuration change that can be deployed across devices from multiple vendors gives network administrators the control and consistency that manual updates often fail to deliver.
Additionally, by integrating with third-party vendors, tickets can be automatically generated for failed compliance checks or firmware alerts. Security teams can triage and assign these tasks without switching between systems.
APIs also enable integration with SIEM platforms, configuration orchestration tools, and policy management frameworks. This provides a feedback loop where firewall posture is visible across operational domains, and policy changes can be evaluated and deployed centrally.
Network automation and integrations help:
- Connect firewall automation with service desks, SIEM, and orchestration platforms
- Automate ticketing and remediation actions, saving valuable time
- Enhance operational visibility through bidirectional data sharing
Identity-aware Controls and Internal Traffic Visibility
Automation for firewalls enables administrators to define and enforce configuration rules based on organizational context. By applying consistent rule sets across devices, teams can maintain access boundaries that reflect business structure and reduce the risk of unauthorized lateral movement.
Administrators can also automate internal firewall rule checks to monitor traffic between segments. When policies deviate from approved templates—such as permitting unsecured communication between critical zones—alerts can be triggered, and corrective actions initiated. This helps maintain isolation between workloads and provides operational visibility into east-west traffic behavior.
- Apply consistent policies based on device groupings and access roles
- Monitor policy deviations between internal network segments
- Automate corrective actions when internal firewall rules drift from the baseline
Simulated Use Cases That Illustrate Operational Impact
The following simulated scenarios demonstrate how firewall automation can be applied across different environments to improve control, reduce risk, and streamline operations.
1. Segment-based compliance enforcement in retail
A retail chain with segmented store networks enforces geo-specific firewall policies based on compliance needs. European locations must meet the GDPR standards, while North American stores comply with local privacy and payment regulations. Automation applies region-specific policy templates and checks for violations weekly. Reports are shared with compliance leads without manual intervention.
2. Time-based firewall rules for R&D environments
A technology firm provides R&D teams temporary access to external services during product testing. Access rules are automatically created with expiration timestamps. After the defined period, rules are revoked by a scheduled automation job.
3. Device profiling for life cycle and patch planning
An insurance provider uses firmware inventory and configuration history to plan device refresh cycles. Devices nearing software end-of-life or showing frequent configuration rollback activity are prioritized for replacement. The system also flags when newly deployed models deviate from the approved configuration baseline.
4. Continuous policy simulation in higher education
A university maintains a virtual lab where proposed firewall rule changes are tested in a simulated environment. The same automation engine that manages production policies is used to simulate effects and compliance outcomes before deployment. This avoids disruptions during peak academic periods and allows faculty-managed services to remain secure.
5. SLA tracking for configuration deployment timelines
A managed service provider defines SLAs for customer configuration updates. When customers request rule changes, automation timestamps the request, tracks deployment completion, and records validation status. SLA compliance reports are automatically generated and shared with clients.
How Site24x7 Network Configuration Manager Supports this Framework
Site24x7 Network Configuration Manager provides a SaaS-based platform for managing firewall configurations, enforcing policy, identifying vulnerabilities, and deploying fixes. It supports multi-vendor environments and integrates with broader IT workflows.
Capabilities include:
- Scheduled and on-demand configuration backups
- Versioning with visual comparison
- Real-time change alerts and rollback
- Custom compliance policy creation and validation
- Firmware vulnerability detection with CVE mapping
- Configlet deployment with vendor-specific syntax support
- Remediation templates for compliance and incident response
- Role-based access controls and audit trails
Using a configuration management tool for firewall security ensures that changes are reviewed, policies are followed, and risks are managed in real time, resulting in audit readiness, faster remediation, or operational consistency. Automation provides the structure required to execute.
Summary
As enterprise networks expand and evolve, the need to boost security, maintain compliance, and streamline configuration management has never been more critical. Manual processes can no longer keep pace with the demands of dynamic, multi-vendor environments. This is where firewall automation emerges as a strategic enabler — delivering the control, visibility, and efficiency required to protect digital infrastructure at scale.
By automating version tracking, policy enforcement, and firmware vulnerability detection, organizations can ensure consistent validation of configurations while proactively addressing risks before they escalate. From remediation templates that reduce downtime to configlets that enable uniform policy deployment, automation offers a framework for both operational consistency and agile response.
Integration with IT workflows, ticketing systems, and SIEM platforms further enhances the value of automation by closing the loop between detection and resolution. Combined with identity-aware controls and internal segmentation monitoring, firewall automation helps reduce security risk, eliminate blind spots, and maintain strong governance across every layer of the network.
Whether it’s supporting regulatory frameworks like PCI-DSS and HIPAA or meeting SLAs with precision, modern solutions like Site24x7 Network Configuration Manager empower organizations to manage firewall infrastructure with confidence. Ultimately, firewall automation is not just a tool — it’s a blueprint for building secure, resilient, and audit-ready enterprise networks.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!