Suggested Articles:
Domain Name System (DNS)
The DNS Protocol - Part 2: DNS Queries & Resoluti…
This section will help you understand how the DNS queries work on the Internet and your home network. There are two ways to use the domain name syste…
Network Address Translation - NAT
Network Address Translation (NAT) Overload - Part…
NAT Overload is the most common NAT method used throughout all networks that connect to the Internet. This is because of the way it functions and the…
Network Fundamentals
Firewall Topologies
In this section we are going to talk about the different ways a firewall can be set up. Depending on your needs, you can have a very simple firewall…
Ethernet Protocol, CSMA/CD, Collisions
Integrating Fast Ethernet into 10MB Ethernet Netw…
Now that Fast Ethernet is here, the question becomes, "How do I start using it ?" Integrating Fast Ethernet into existing networks need not be done a…
Featured Subcategories:
Netflow Articles:

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
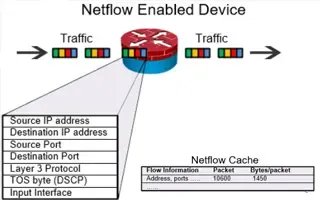
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
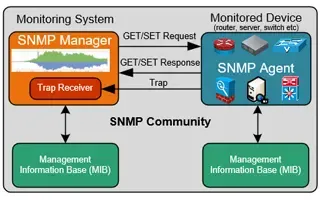
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
Your IP address:
192.178.4.98
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
The VLAN Concept - Introduction to VLANs
We hear about them everywhere, vendors around the world are constantly trying to push them into every type of network and as a result, the Local Area Netw…

VLAN Networks
Comparing Traditional Flat & VLAN Networks
Designing and building a network is not a simple job. VLANs are no exception to this rule, in fact they require a more sophisticated approach because of t…

VLAN Networks
Dynamic VLANs
Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of their…

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informati…
Routing
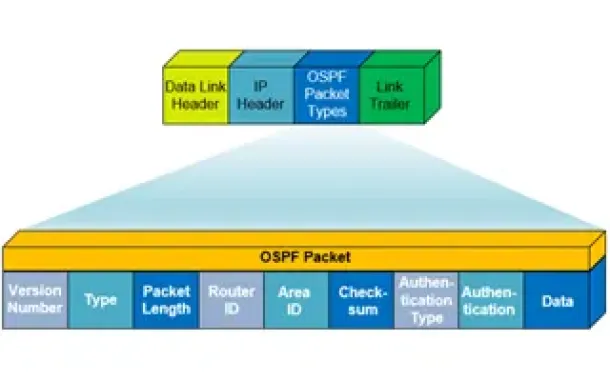
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
Routing
Routed Protocols
We all understand that TCP/IP, IPX-SPX are protocols which are used in a Local Area Network (LAN) so computers can communicate between with each other and…
Routing
Link State Routing Protocols
Link State routing protocols do not view networks in terms of adjacent routers and hop counts, but they build a comprehensive view of the overall network…
Cisco Wireless
Configuring Cisco WLC Link Aggregation (LAG) with Port…
Cisco Wireless Controllers (WLC) support the configuration of Link Aggregation (IEEE 802.3ad - LAG) which bundles the controller ports into a single port…
Windows Servers
Introduction to Windows DNS – The Importance of DNS fo…
The Domain Name System (DNS) is perhaps one of the most important services for Active Directory. DNS provides name resolution services for Active Director…
Cisco Firewalls
Cisco ASA Firepower Threat Defense (FTD): Download and…
One Appliance – One Image is what Cisco is targeting for its Next Generation Firewalls. With this vision, Cisco has created a unified software image named…
Security Service Edge (SSE)
Security Service Edge (SSE) Limitations & Disadvantage…
This article explores the Security Service Edge (SSE) portion of Secure Access Service Edge (SASE) and the need for holistic cybersecurity protections.
W…


















