Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
|
Articles:
Dynamic NAT - Part 2
| Read |
|
Articles:
Dynamic NAT - Part 1
| Read |
|
Articles:
Static NAT - Part 2
| Read |
|
Articles:
Static NAT - Part 1
| Read |
|
Articles:
The Network Address Translation Table
| Read |
| Read | |
Suggested Articles:
Network Fundamentals
The Importance of a Network Analyzer – Packet Sni…
Network Analyzers, also known as Packet Sniffers, are amongst the most popular network tools found inside any Network Engineer’s toolkit. A Network A…
Ethernet Protocol, CSMA/CD, Collisions
Ethernet Troubleshooting - Physical Frame Corrupt…
When troubleshooting your Ethernet network, the first thing to look for is physical frame corruption. In this essay, we will discuss the different ca…
Network Cabling
USB Direct Cable Connection, USB Versions, Specif…
Today, Serial and Parallel Direct Cable Connections are considered obsolete methods of transferring data between computers. The fact is that even USB…
Network Protocols
Understanding VPN IPSec Tunnel Mode and IPSec Tra…
IPSec’s protocol objective is to provide security services for IP packets such as encrypting sensitive data, authentication, protection against repla…
Featured Subcategories:
Netflow Articles:
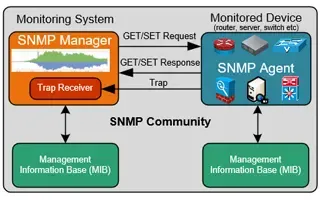
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
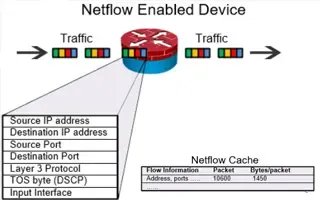
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
Comparing Traditional Flat & VLAN Networks
Designing and building a network is not a simple job. VLANs are no exception to this rule, in fact they require a more sophisticated approach because of t…

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…
VLAN Networks
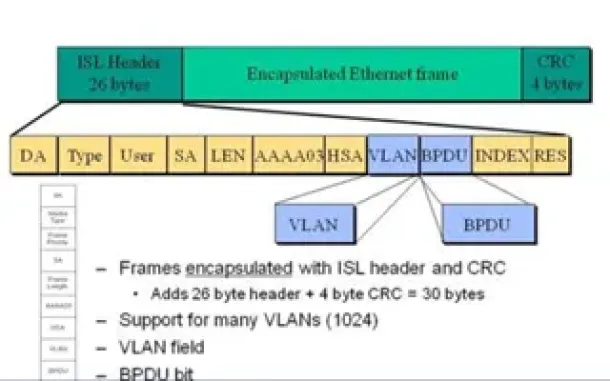
VLAN InterSwitch Link (ISL) Protocol Analysis
Deciding whether to use ISL or IEEE 802.1q to power your trunk links can be quite confusing if you cannot identify the advantages and disadvantages of eac…
VLAN Networks
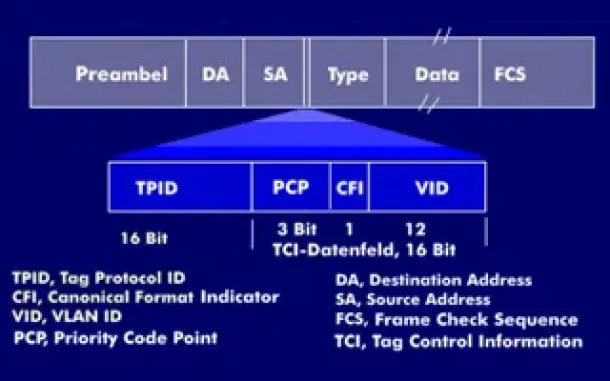
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…
Routing
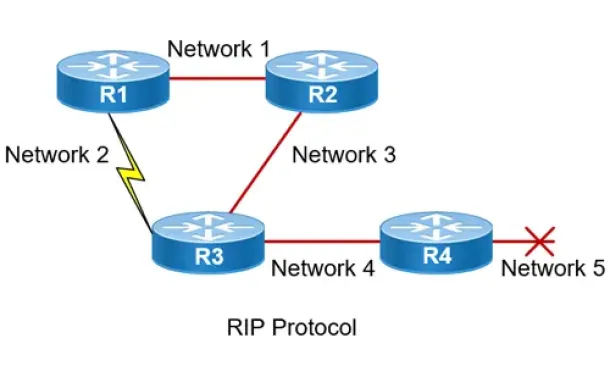
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…
Routing
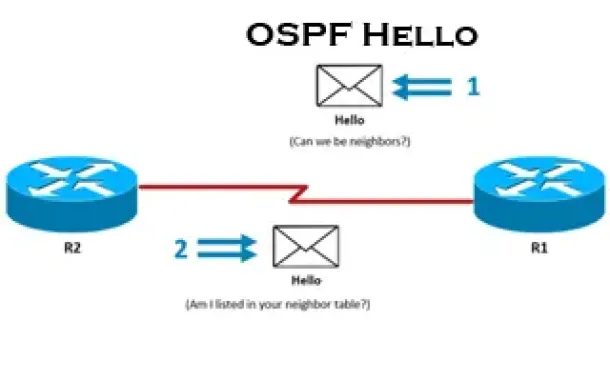
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Proce…
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll examine…
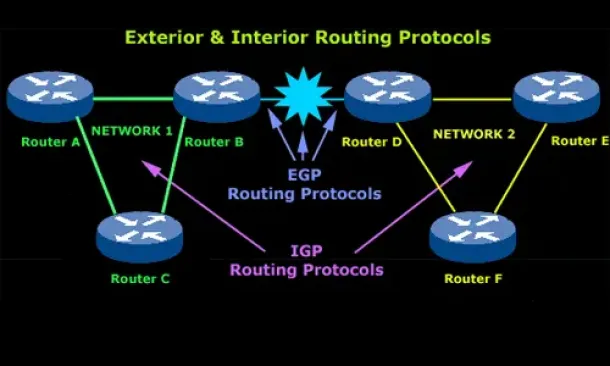
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchange…
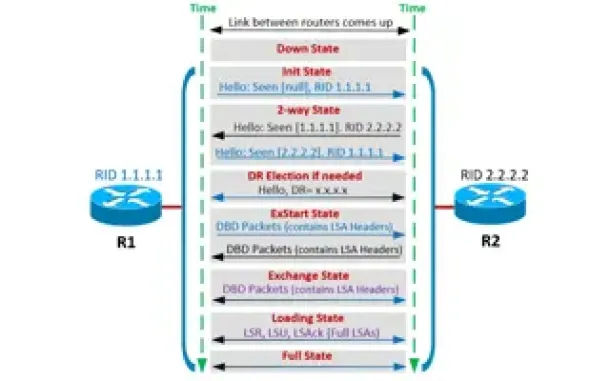
Routing
OSPF - Part 4: OSPF Neighbor States – OSPF Neighbor Fo…
This is the third article of our OSPF series which analyzes the different OSPF States routers go through during the OSPF discovery and neighbor forming pr…
Cisco Routers
Configuring Static Route Tracking using IP SLA (Basic)
In today's network environment, redundancy is one of the most important aspects, whether its on the LAN side or on the WAN side. In this topic we will be…
SASE & SD-WAN Networks
Complete Guide to SD-WAN. Technology Benefits, SD-WAN…
SD-WAN is the answer for enterprises and organizations seeking to consolidate network functions and services while at the same time simplify their WAN inf…
Cisco Switches
VLAN Security Tips - Best Practices
This article focuses on VLAN Security and its implementation within the business network environment. We provide tips and Cisco CLI commands that will hel…
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…



















