Suggested Articles:

ManageEngine Firewall Analyzer
Achieving Modern Compliance: Navigate PCI DSS v4…
In an era where cyber threats are growing in both volume and sophistication, failing to meet security compliance standards is no longer just a legal…

ManageEngine Firewall Analyzer
Challenges & Solutions to Managing Firewall Rules…
In today's interconnected digital landscape, where businesses rely heavily on networked systems and the internet for their operations, the importance…

OpManager - Network Monitoring & Management
Elevate your network management: Maximizing effic…
As technology evolves, so do our networks. Today's sprawling network infrastructures are intricate ecosystems, demanding more from IT teams than ever…
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Featured Subcategories:
WireShark Articles:
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
How To Detect ARP Attacks & ARP Flooding With Col…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addres…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on P…
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a P…
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtual…
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fire…

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based Po…
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient wa…
Windows Servers
Configuring Local Group Policy for Windows 2003
Windows 2003 Group Policies allow the administrators to efficiently manage a group of people accessing a resource. Group policies can be used to control b…
Windows Servers
Windows Server 2016 – Hyper-V Virtualization Update
The new Hyper-V virtualization features offered by Windows Server 2016 are planning to make major changes in the virtualization market. From Nested Hyper-…

Windows Servers
Deploying Active Directory & DNS Services on Windows S…
This article provides a comprehensive guide to deploying Active Directory and DNS Services on Windows Server 2022, encompassing the Essential, Standard, a…
Windows Servers
Renaming Windows 2000 Domain Name
Sometimes renaming a domain is an essential business requirement. There are many situations, such as mergers, change of company name or migration from a t…
Popular Topics
Routing
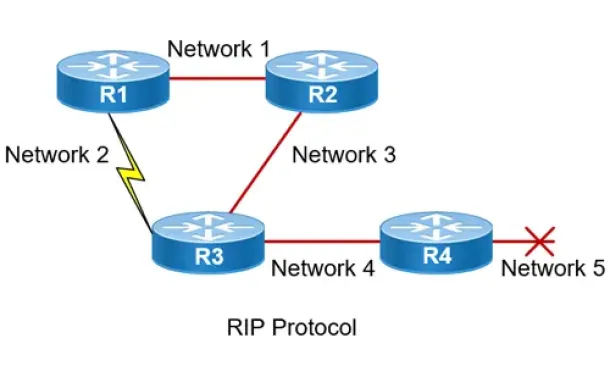
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…

Network Fundamentals
Network Switches & Bridges
Network Switches are the evolution of Hubs and Repeaters, and enable the creation of networks by connecting multiple devices together. They are critical c…
Network Protocol Analyzers
Improve Network Analysis Efficiency with Colasoft's Ca…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network proble…
Network Protocol Analyzers
Detect Brute-Force Attacks with nChronos Network Secur…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/database…
Cisco Routers
Configuring Cisco SSL VPN AnyConnect (WebVPN) on Cisco…
Our Web SSL VPN article written back in 2011 introduced this new wave of VPN services. This article extends the topic by covering the installation a…
Cisco Routers
Installing Security Device Manager (SDM) on a Cisco Ro…
For years now, Cisco has been developing its Security Device Manager (SDM) software. This web-based software is designed to help the less experienced user…
Cisco CallManager-CCME
CallManager Express GUI Software Installation & Config…
This article covers the installation of Cisco's CallManager Express on Cisco routers. Here you'll find the necessary installation commands, files to downl…
Cisco Routers
Troubleshooting PPP Internet Connection On A Cisco Rou…
The Point-to-Point Protocol is one of the most popular protocols around used by engineers, ISPs and companies around the globe for authentication of remot…



















