Secure CallManager Express Communications - Encrypted VoIP Sessions with SRTP and TLS
In this article we discuss about the security and encryption of Cisco Unified Communications Manager Express (CUCME) which is an integral part of Cisco UC; and more so of Cisco Express Call processing regime.
Voice over IP (VoIP) is not just need of hour for most enterprises; it’s something their business depends on to a degree that without IP communications in place, their business processes and revenue streams will fall apart. In such case, it goes without saying; security of voice networks is one of the chief concerns when it comes to security of intellectual capital and customer data. More often than not, one of the first thoughts is how to secure the VoIP network itself which is leveraged by IP Telephony / Unified Communication (UC) applications.
So what is that may be the most commonly sought after yet elusive security control which plays an indispensable role in securing a VoIP network? Your guess is as good as mine, it is encryption! Now, you are well within your rights to ask why elusive? The simple answer is – where encryption can help you succeed and protect the privacy of communications, it can also be detrimental for various functions / organizations e.g. monitoring secure calls is not a trivial task and encrypting all endpoints has an impact on platform sizing and performance.
The use of authentication and encryption helps protect confidentiality and makes it harder for malicious insiders or outsiders from tampering with the signaling and media streams, the CUCME router, and IP phones. When the CUCME security features are enabled i.e. the media streams (SRTP) and call signaling (TLS), the communication between Cisco Unified IP phones and CUCME as well as Phones is encrypted as shown in figure 1:
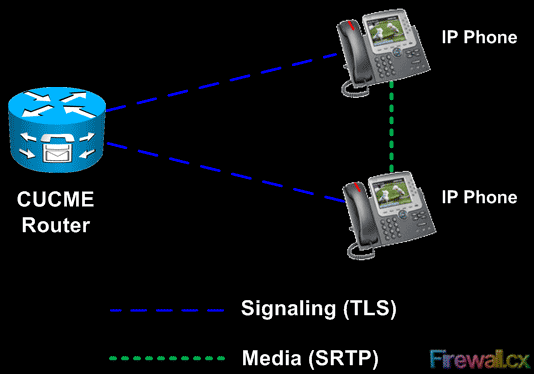 Figure 1 - CUCME to Cisco IP Phone SRTP and TLS
Figure 1 - CUCME to Cisco IP Phone SRTP and TLS
Let’s go over some of the assumptions, requirements and caveats before we dwell further into CUCME security configuration.
Assumptions For CUCME Encryption
- It is assumed that CUCME is configured and operational (without security in place); this article only serves to elucidate the process of implementing authentication and encryption on the CUCME
- It must also be understood that authentication is an integral part of overall security construct when the discussion is around encryption since; authentication provides integrity whereas encryption provides privacy.
Requirements For CUCME Encryption
- Enabling CUCME encryption requires Cisco IOS feature set Advanced Enterprise Services (adventerprisek9) or Advanced IP Services (advipservicesk9)
- CUCME version 4.2 or later is require to provide media encryption
- Supported platforms include 2800, 2900, 3200, 3800, and 3900 series routers
- Network Time Protocol (NTP) must be enabled to ensure the certificate dates are correct and to check validity of certificates
- IOS CA to sign various certificates (on same router as that of CUCME or different router
Caveats For CUCME Encryption
- Secure three-way software conference is not supported therefore, while in conference, the call falls back to plain RTP. However, if a party drops from a three-party conference, the call between the remaining two parties returns to a secure state (if the two endpoints are configured for encryption)
- Media and signaling encryption requires the Cisco CTL client service
- Calls to Cisco Unity Express (CUE) do not support SRTP or TLS for media and signaling respectively
- Music on Hold (MOH) does not support encryption
- Modem relay and T.3 fax relay calls not support encryption
- Secure CUCME does not support Session Initiation Protocol (SIP) trunks and only H.323 trunks are supported (with IPSec for signaling protection)
With above in mind, let’s take a deep dive into the enablement of security (Encryption, Authentication) for Cisco Unified IP Phones on CUCME.
Enabling SRTP & TLS On CUCME For Endpoints
Alike any PKI hierarchy, enabling encryption (and authentication) on CUCME requires the use of a Certificate Authority (CA) server/process. CA can be configured on the same router on which CUCME application is running or it can be a different IOS router (dedicated to CA function in an organization). The major function of CA for CUCME security is to provide certificates, duration for which certificates are valid, and trust-relationship between different entities by virtue of certificates.
Configuring IOS Certificate Authority (CA)
The following commands are required to configure the IOS CA. For the following example, we are enabling the CA on the same router as that of CUCME.
First we must ensure that the HTTP server on the router is enabled since, by default port 80 (TCP) will be used for granting certificates and for accepting certificate signing requests by IOS CA.
Now, we need to configure the CA process and enable CA process:
Finally define the CA trustpoint and define (globally) enrollment URL:
CUCME(ca-trustpoint)# enrollment url http://10.10.10.1:80
CUCME(ca-trustpoint)# revocation-check none
At this time, we are done with CA server definition. Next step is to start defining the various certificates which will be used for CUCME security processes (CME, TFTP, CAPF and so on).
Generate Certificates For Enabling Security
A number of certificates must be generated by creating a trustpoint and enrolling it with the CA for enabling various security processes on CUCME. Although CUCME supports leveraging a single trustpoint for all certificate functions, it is a leading practice recommendation to have different trust points for different certificate functions so, it is easier to manage different certificate expiry, revocation, regeneration and so on.
The different certificates required for SRTP and TLS are:
- CUCME
- TFTP
- CAPF
- SAST tokens
Creating a Certificate For CUCME, TFTP, CAPF, SAST1 & SAST2 Processes
Following commands outline the process to generate the certificate for the secure CME function:
CUCME(ca-trustpoint)# enrollment url http://10.10.10.1:80
CUCME(ca-trustpoint)# revocation-check none
CUCME(ca-trustpoint)# rsakeypair CUCME
The next step to creating the certificate is to authenticate and enroll the trust point with the Certificate Authority.
Note: Each of the command i.e. trustpoint authenticate and enroll provide interactive prompts. Extraneous output has been omitted
Authenticating CUCME trustpoint & Enrolling CUCM Trustpoint:
<output omitted>
% Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
CUCME(config)# crypto pki enroll CUCME
% Start certificate enrollment ..
<output omitted>
Password: *******
Re-enter password: *******
<output omitted>
Request certificate from CA? [yes/no]: yes
% Certificate request sent to Certificate Authority
Next, we define the other trsutpoints, authenticate and enroll them with Certificate Authority.
TFTP Trustpoint definition:
CUCME(config)# crypto pki trustpoint TFTP
CUCME(ca-trustpoint)# enrollment url http://10.10.10.1:80
CUCME(ca-trustpoint)# revocation-check none
CUCME(ca-trustpoint)# rsakeypair TFTP
Authenticating and enrolling TFTP trustpoint:
CUCME(config)# crypto pki authenticate TFTP
<output omitted>
!
CUCME(config)# crypto pki enroll TFTP
<output omitted>
CAPF Trustpoint definition:
CUCME(config)# crypto pki trustpoint CAPF
CUCME(ca-trustpoint)# enrollment url http://10.10.10.1:80
CUCME(ca-trustpoint)# revocation-check none
CUCME(ca-trustpoint)# rsakeypair CAPF
Authenticating and enrolling CAPF trustpoint:
<output omitted>
!
CUCME(config)# crypto pki enroll CAPF
<output omitted>
SAST1 Trustpoint definition:
CUCME(ca-trustpoint)# enrollment url http://10.10.10.1:80
CUCME(ca-trustpoint)# revocation-check none
CUCME(ca-trustpoint)# rsakeypair SAST1
Authenticating and enrolling SAST1 trustpoint:
CUCME(config)# crypto pki authenticate SAST1
<output omitted>
!
CUCME(config)# crypto pki enroll SAST1
<output omitted>
SAST2 Trustpoint definition:
CUCME(config)# crypto pki trustpoint SAST2
CUCME(ca-trustpoint)# enrollment url http://10.10.10.1:80
CUCME(ca-trustpoint)# revocation-check none
CUCME(ca-trustpoint)# rsakeypair SAST2
Authenticating and enrolling SAST2 trustpoint:
CUCME(config)# crypto pki authenticate SAST2
<output omitted>
!
CUCME(config)# crypto pki enroll SAST2
<output omitted>
Enabling CAPF server on CUCME
Alike CUCM, Certificate Authentication Proxy Function (CAPF) server is accountable for issuing CTL signed Locally Significant Certificates (LSC). Following commands enable CAPF server on CUCME.
CUCME(config)# capf-server
CUCME(config-capf-server)# trustpoint-label CUCME
CUCME(config-capf-server)# cert-enroll-trustpoint CA password 0 cisco123
CUCME(config-capf-server)# phone-key-size 1024
CUCME(config-capf-server)# port 3084
CUCME(config-capf-server)# auth-mode null-string
CUCME(config-capf-server)# source-addr 10.10.10.1
Invoking IOS CTL Client
The final step, before an e-phone can be configured for encryption and authentication is to enable Certificate Trust List (CTL) client on CUCME. CTL client helps sign the list of servers which can be trusted by a Cisco IP Phone with the certificates generated earlier – CUCME, TFTP, CAPF and so on.
The IP Phone will download the CTL file via TFTP and store the file on the phone. This is analogous to CUCM CTL and CTL client must be configured explicitly on IOS leverage the various certificates.
CUCME(config-ctl-client)# server cme 10.10.10.1 trustpoint CUCME
CUCME(config-ctl-client)# server tftp 10.10.10.1 trustpoint TFTP
CUCME(config-ctl-client)# server cme 10.10.10.1 trustpoint CAPF
CUCME(config-ctl-client)# sast1 trustpoint SAST1
CUCME(config-ctl-client)# sast2 trustpoint SAST2
CUCME(config-ctl-client)# regenerate
Configuring Telephony-Service To Leverage Security
CUCME support configuring endpoints for SRTP (media) and TLS (signaling). Once, the aforementioned steps are concluded, CUCME needs to be configured to use the defined certificates for different functions. The following commands in telephony-service mode helps enable authenticated TFTP file transfer and TLS for signaling.
CUCME(config-telephony)# secure-signaling trustpoint CUCME
CUCME(config-telephony)# tftp-server-credentials trustpoint TFTP
CUCME(config-telephony)# server-security-mode secure
CUCME(config-telephony)# cnf-file perphone
CUCME(config-telephony)# cnf-file location flash:
Configuring Endpoints (E-Phones) For Security
The final step is to configure the e-phones for security mode. Now, there are two ways to configure the e-phones for security mode. Those two ways are as follows:
- Configure e-phone (device) security at global mode for all supported phone models
- Configure e-phone (device) security mode on a device by device basis
Configuring Device Security at Global Level
To enable security at global level in CUCME for all Cisco IP Phones which support encryption and authentication, issue the following commands in global configuration mode:
Configuring Device Security per Device Basis
In certain cases, it may be required to apply encryption to some, authentication to other devices, and no security to the rest of the phones. In such case, for each e-phone commands can be entered at e-phone level, on phone by phone basis.
Following series of commands can issued to enable security on phone by phone basis:
CUCME(config)# ephone 110
CUCME(config-ephone)# mac-address 1234.1234.1234
CUCME(config-ephone)# device-security-mode [none | authenticated | encrypted]
CUCME(config-ephone)# cert-oper upgrade auth-mode null-string
CUCME(config-ephone)# reset
About the Author
Akhil Behl is a Solutions Architect with Cisco Advanced Services, focusing on Cisco Collaboration and Security Architectures. He leads collaboration and security projects worldwide for Cisco Advanced Services and the Collaborative Professional Services (CPS) portfolio. Prior to his current role, he spent ten years working in various roles at Linksys as a Technical Support Lead, as an Escalation Engineer at Cisco Technical Assistance Center (TAC), and as a Network Consulting Engineer in Cisco Advanced Services. Akhil has a bachelor of technology degree in electronics and telecommunications from IP University, India, and a master’s degree in business administration from Symbiosis Institute, India.
Summary
Cisco Unified Communications Manager Express (CUCME) is an indispensible component of Cisco’s UC Express portfolio and has CUCM like capabilities. Moreover, CUCME can provide enterprise wide security by empowering you to enable media and signaling encryption between CUCME and Phones. This article outlines the capabilities of CUCME to support encryption and authentication for phone calls and signaling. The process to enable and pull together CUCME security may seem daunting at first however; it is a onetime configuration and can go a long way in safeguarding an organization’s voice channels.
|
CUCME(config)# crypto pki server CA CUCME(ca-server)# database level complete CUCME(ca-server)# database url nvram: CUCME(ca-server)# grant auto CUCME(ca-server)# lifetime certificate 1095 CUCME(ca-server)# lifetime ca-certificate 1095 |
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














