Transmission Control Protocol - Part 1: Introduction to TCP
Understanding how each protocol fits into the OSI Model is essential for any network engineer. This page analyses how TCP is classified as a 'transport protocol' and gives you an insight into what to expect from the protocol.
Fitting TCP into the OSI Model
As most of you are well aware, every protocol has its place within the OSI Model. The OSI Model is an indication of the complexity and intelligence of the protocol. As a general rule, the higher you move up the OSI Model, the more intelligent protocols become. The positioning of the layer also reflects how CPU entensive they are, whereas the lower layers of the OSI Model are quite the opposite, that is, less CPU intensive and less intelligent.
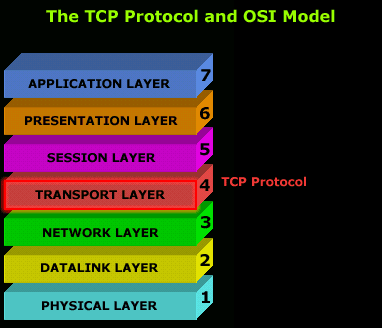
TCP is placed at the 4th layer of the OSI Model, which is also known as the transport layer. If you have read through the OSI model pages, you will recall that the transport layer is responsible for establishing sessions, data transfer and tearing down virtual connections.
With this in mind, you would expect any protocol that's placed in the transport layer to implement certain features and characteristics that would allow it to support the functionality the layer provides.
So as we analyse TCP, you will surely agree that it fits right into the transport layer.
The diagram below shows you where the TCP header is located within a frame that's been generated by a computer and sent to the network. If you rotate it 90 degrees to your left, you would get something similar to the previous diagram. This of course is because each layer appends its own information, or header if you like:
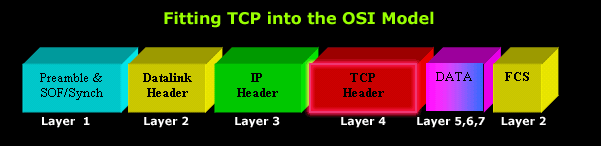
The frame is made up of six 3d blocks so you can see which piece is added by every OSI layer. You can see that the TCP Header containing all the options the protocol supports, is placed right after the IP Header (Layer 3), and before the data section that contains upper layer information (Layers 5,6,7).
Note: For those who are wondering about the presence of the FCS block at the end, it contains a special checksum that is placed by the datalink layer in order to allow the receiving host to detect if the current frame has been corrupt during transit.
Please refer to the Ethernet II Frame page for more information.
Where and Why Would we use the TCP?
TCP is used in almost every type of network. As a protocol, it is not restricted to any type of network topology, whether it be a local area network (LAN) or wide area network (WAN). Being a transport protocol, we call it a transport protocol because it's located in the transport layer of the OSI model its primary job is to get data from one location to another, regardless of the physical network and location.
As most of you already know, there are two types of transport protocols, TCP being one of them and UDP (User Datagram Protocol) being the other. The difference between these two transport protocols is that TCP offers an extremely reliable and robust method of transferring data, ensuring that the data being transferred does not become corrupt in any way. UDP, on the other hand, offers a non reliable way of transferring data without being able to guarantee the data has arrived to its destination or its integrity when it does arrive.
The Concept of a Transport Protocol
As we mentioned, TCP is a transport protocol and this means it is used to transfer data of other protocols. At first, this might sound weird or confusing but this is exactly why it was designed, adding substantial functionality to the protocols it carries.
The diagram below is the simplest way to show the concept of a 'transport' protocol:
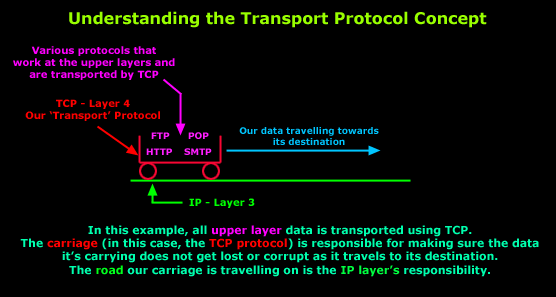
In the pages to follow, we will have a closer look at how TCP manages to provide its reliable data transfer method and make sure packets get to their destination without errors. This whole process is the work of many 'subsystems' within the TCP that work together to provide the reliability that TCP gives us.
Before we dive in deeper though, let's have a quick overall view of the protocol. If you're not interested in too much technical detail, then the next page is for you! For those looking for an in-depth analysis, you should read the quick-overview page to give you an idea on what we will be analysing soon.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














